[OtterCTF 2018]电子取证(后)
摘要:该系列题目围绕内存取证展开,通过Volatility工具分析OtterCTF.vmem内存镜像。首先发现恶意软件通过Rick下载的M3an_T0rren7_4_R!ck种子文件传播,溯源到mail.com网站的下载记录。随后在Chrome进程内存中提取出邮箱凭证rickopicko@mail.com和疑似flag的字符串。针对勒索软件部分,通过分析3720进程内存获取比特币地址和加密密码&q
[OtterCTF 2018]Path To Glory
题目描述
How did the malware got to rick's PC? It must be one of rick old illegal habits...
F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 filescan | findstr "BitTorrent" | findstr ".torrent"
找到了我们需要的文件
F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007dcbf6f0 -D ./
>F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007dae9350 -D ./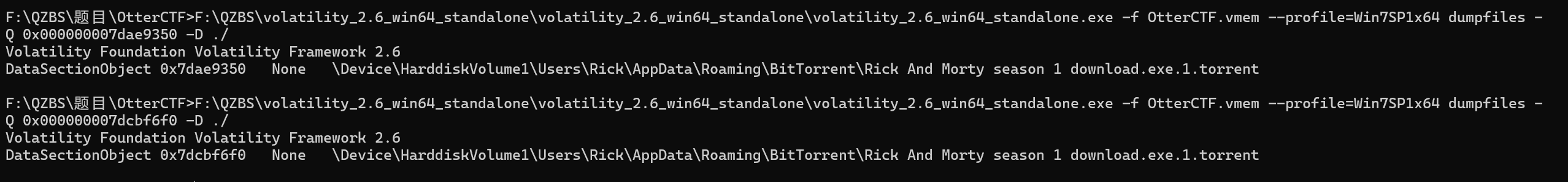
把文件下载下来查看
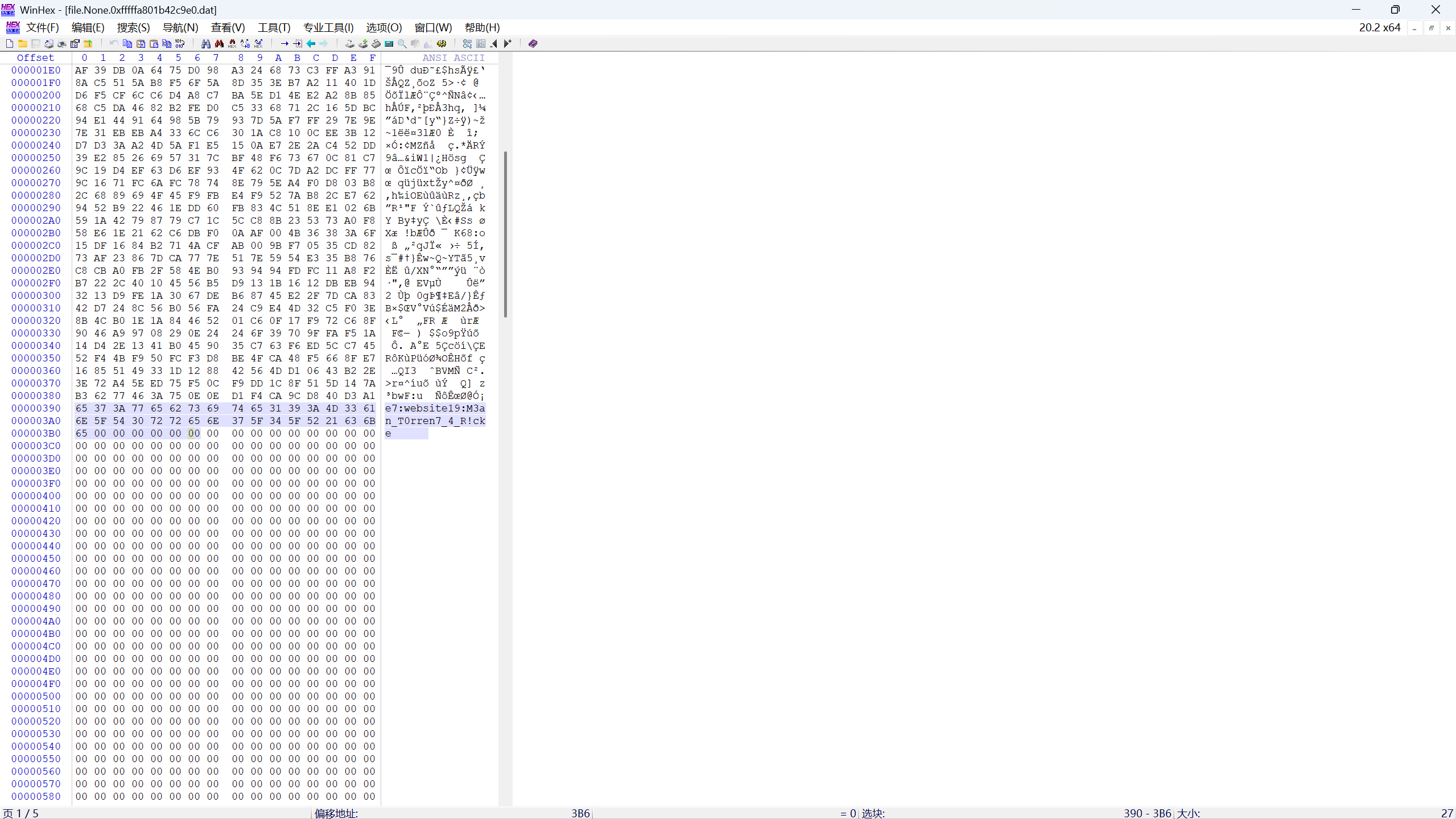
M3an_T0rren7_4_R!ck
[OtterCTF 2018]Path To Glory 2
题目描述
Continue the search after the way that malware got in.
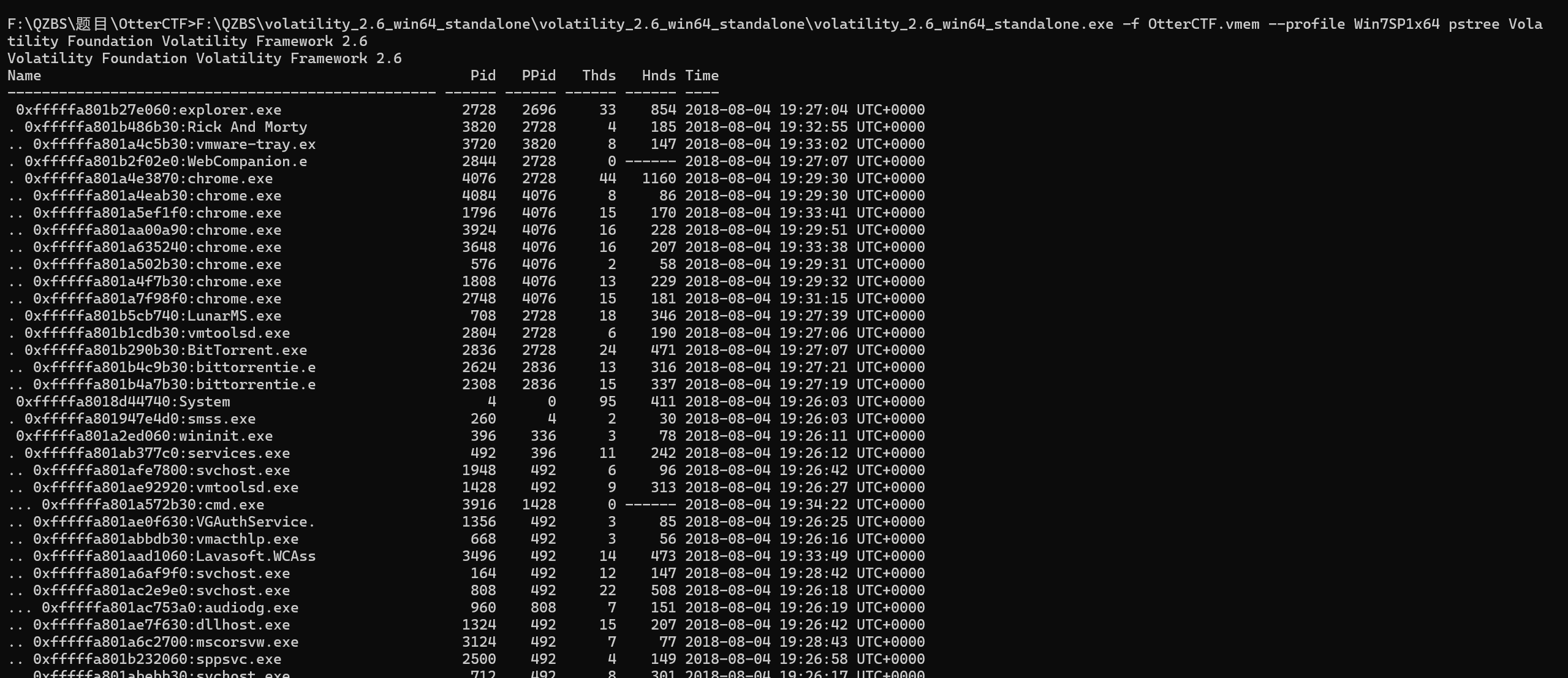
F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile Win7SP1x64 pstree Volatility Foundation Volatility Framework 2.6刚刚 pslist 查进程的时候,Chrome.exe 进程是出现次数最多的,说明是最主要使用的浏览器
我们可以使用 filescan 和 dumpfiles 来查找和提取Chrome浏览器历史记录数据库(豆知识:Chrome 将历史数据存储在 SQLite 数据库中)
>F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007d45dcc0 -D ./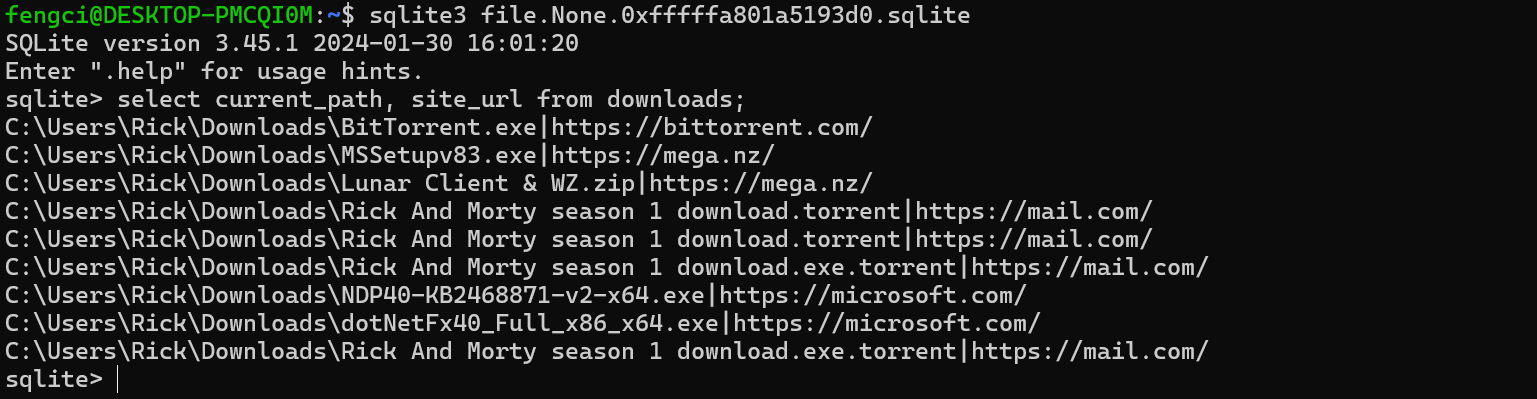
执行语句select current_path, site_url from downloads;查询下载路径和url
可以看到种子文件是从 https://mail.com 这个网址下载的,我们将 chrome.exe 进程内存中文件的文件提取出来

F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 memdump -n chrome.exe -D .\然后我们用 strings 配合 grep 查看这些提取出来的文件,筛选邮箱后缀 @mail.com的前后十行
$ strings *|grep -C 10 "@mail.com"
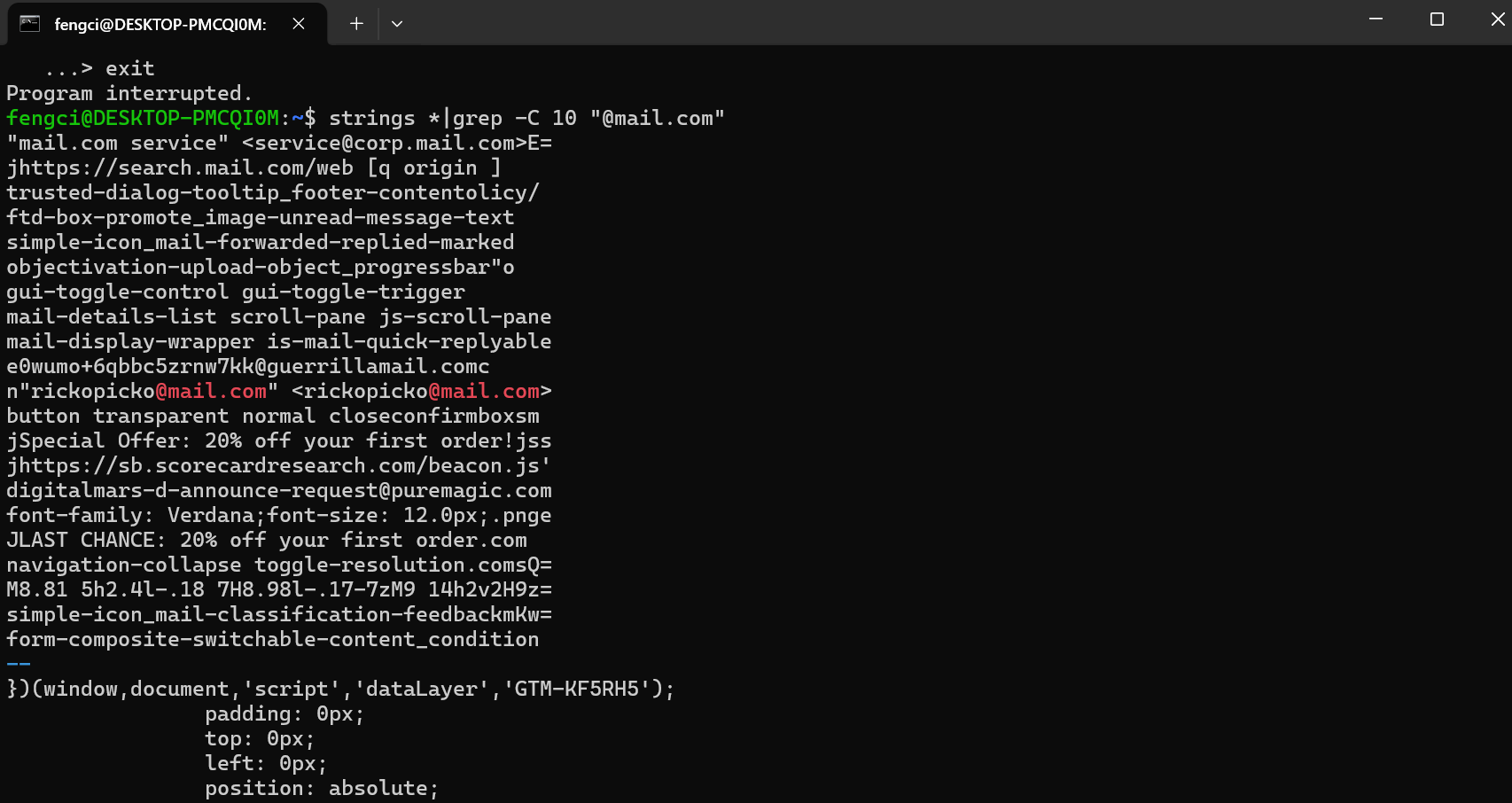
这里找到 Rick 的邮箱,有邮箱和密码了,我尝试去登陆邮箱寻找线索,但是显示邮箱/密码错误(毕竟这是个内存取证题,还是老实点吧),然后继续跟进 rickopicko@mail.com的前后二十行,这串很像flag,提交果然是正确的
strings * |grep -C 20 "rickopicko@mail.com"
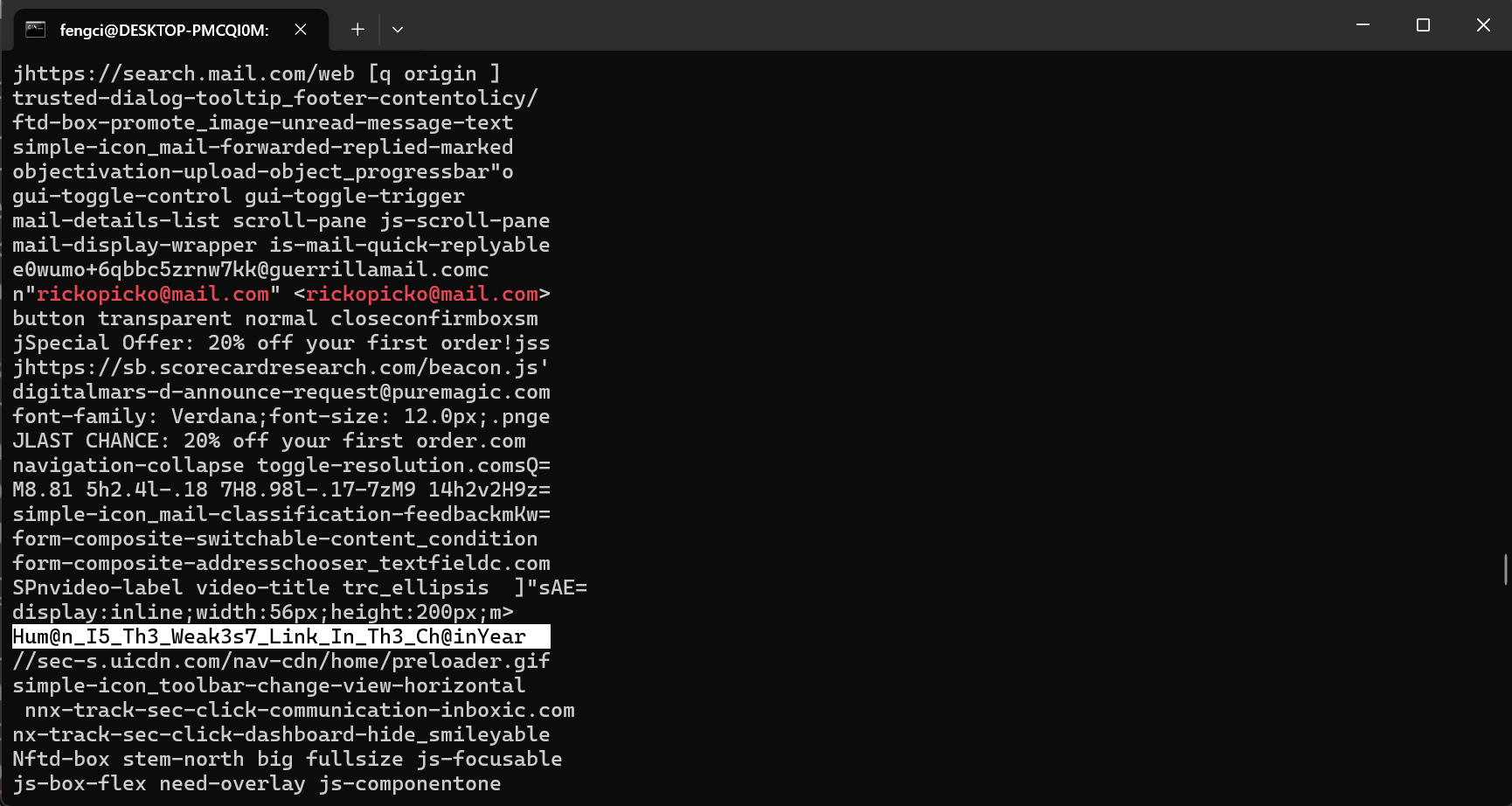
[OtterCTF 2018]Bit 4 Bit
题目描述
We've found out that the malware is a ransomware. Find the attacker's bitcoin address.
F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 memdump -p 3720 -D ./ Volatility Foundation Volatility Framework 2.6.1
Volatility Foundation Volatility Framework 2.6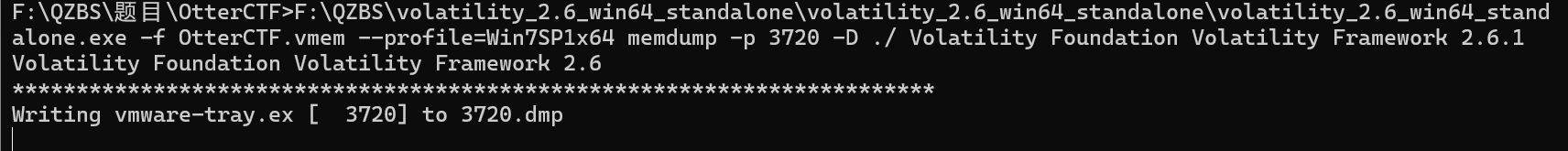
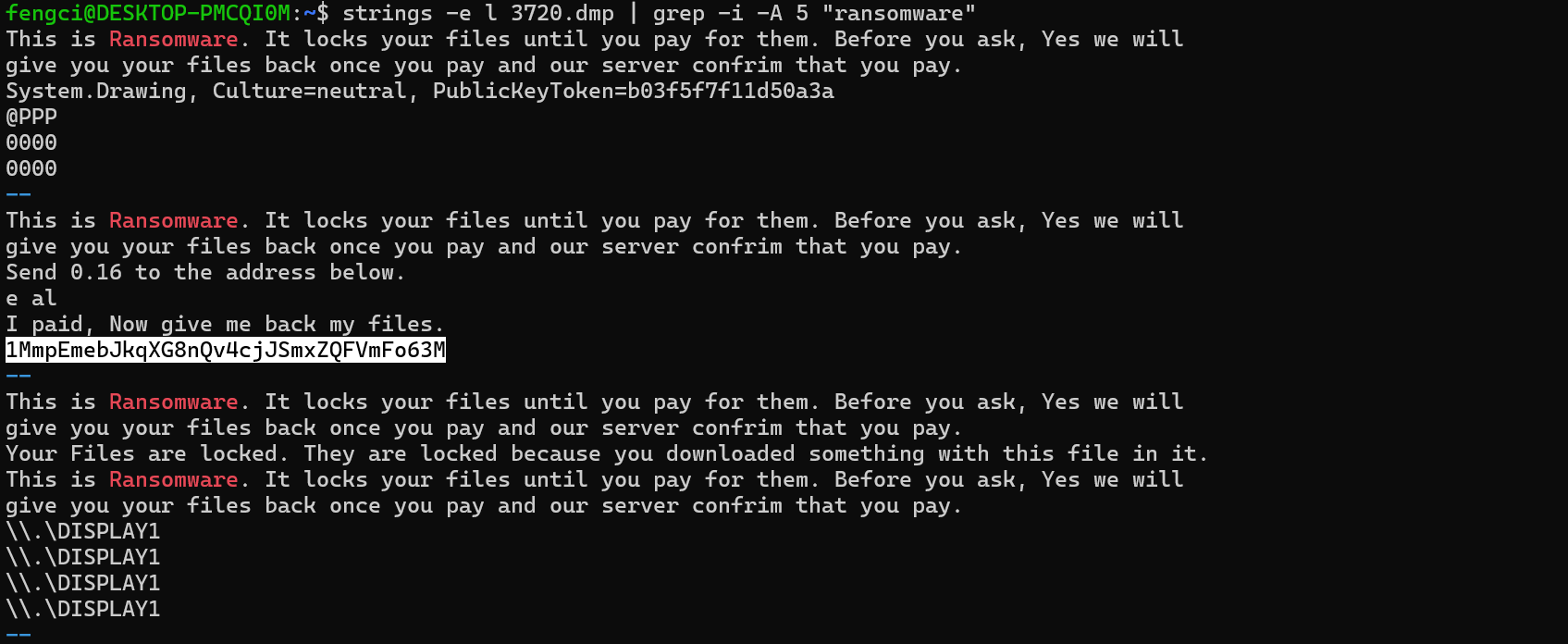
使用strings查找ransomware相关的内容
[OtterCTF 2018]Graphic's For The Weak
题目描述
There's something fishy in the malware's graphics.
恶意软件的图形中有问题, 用foremost分离一下程序
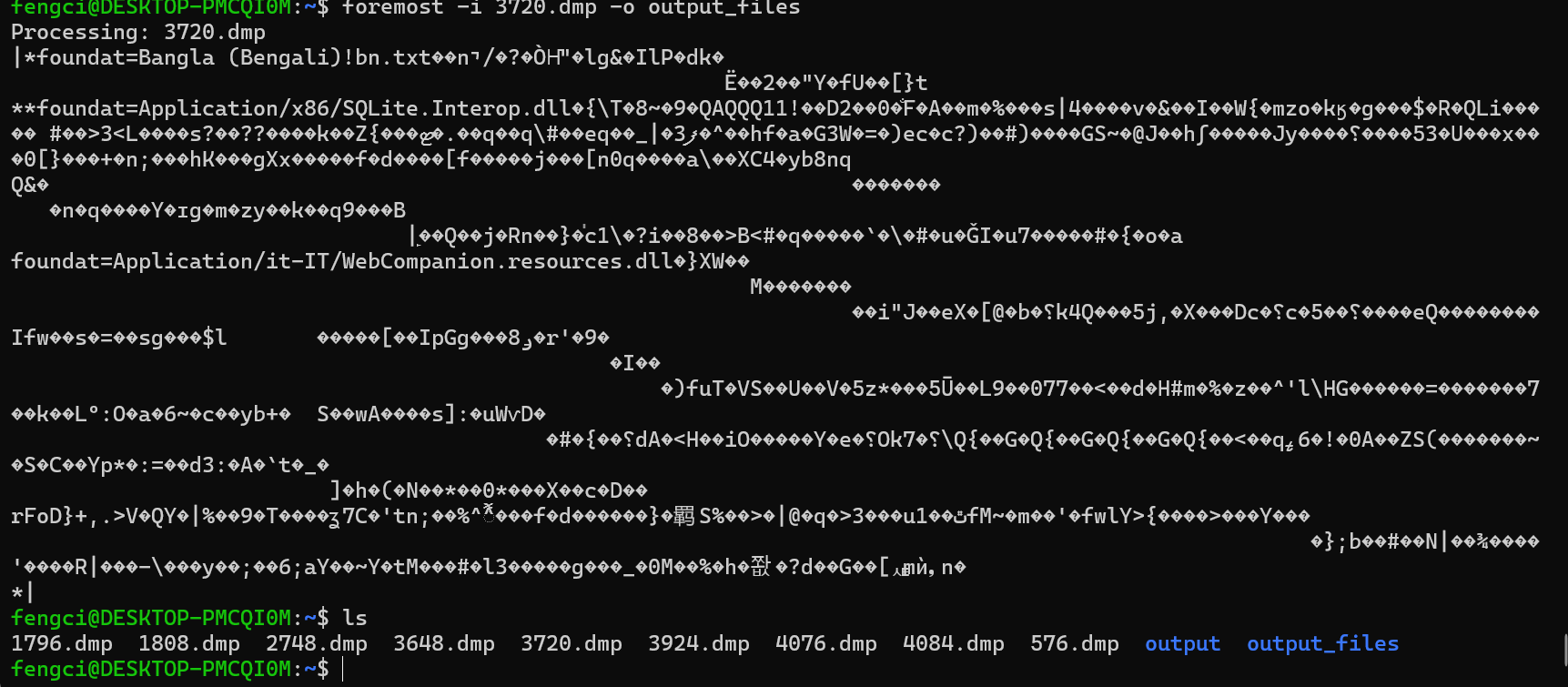
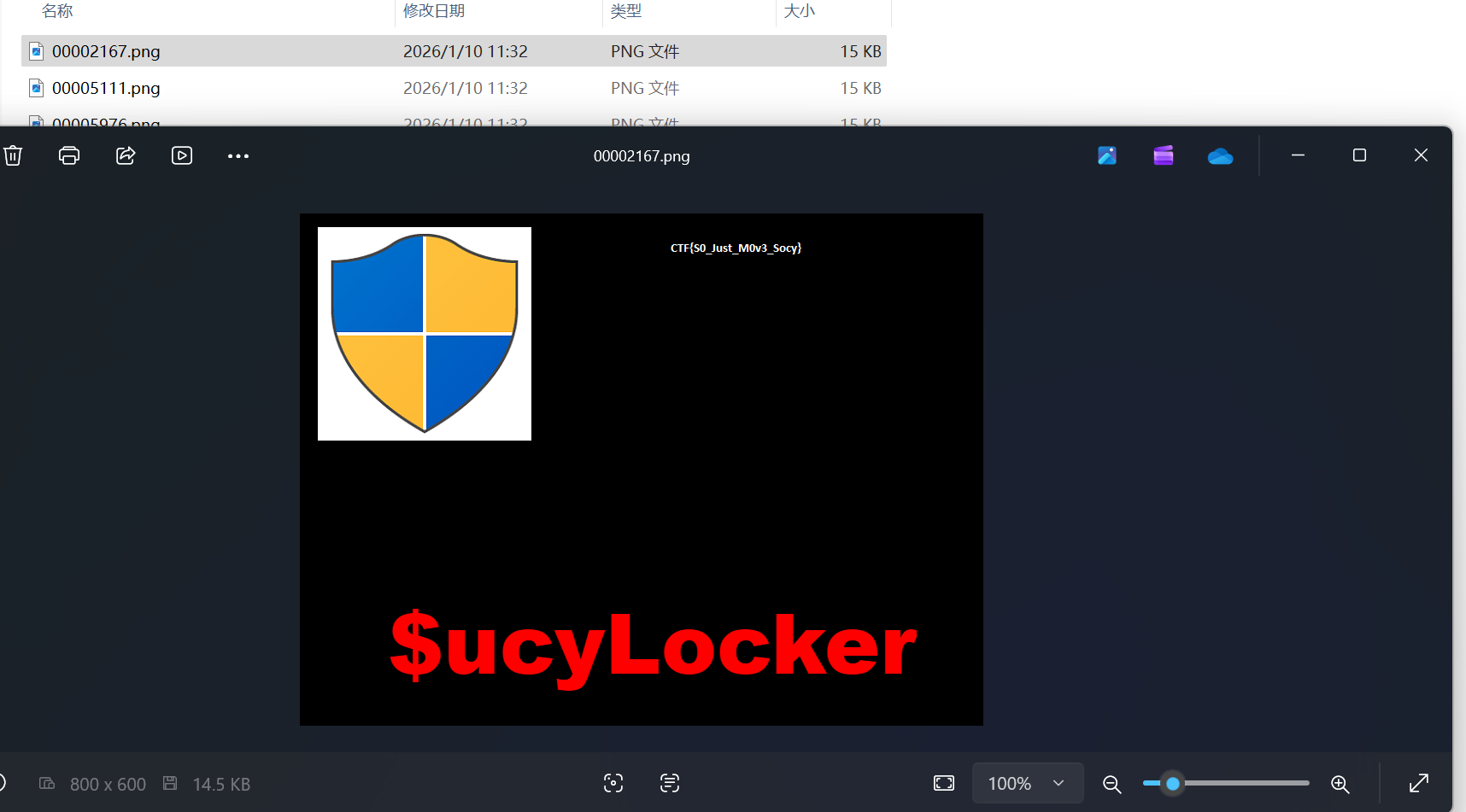
CTF{S0_Just_M0v3_Socy}
[OtterCTF 2018]Recovery
题目描述
Rick got to have his files recovered! What is the random password used to encrypt the files?
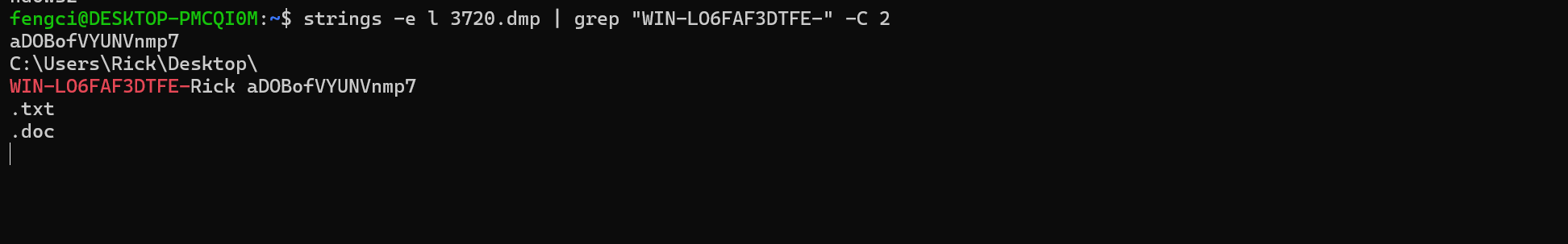
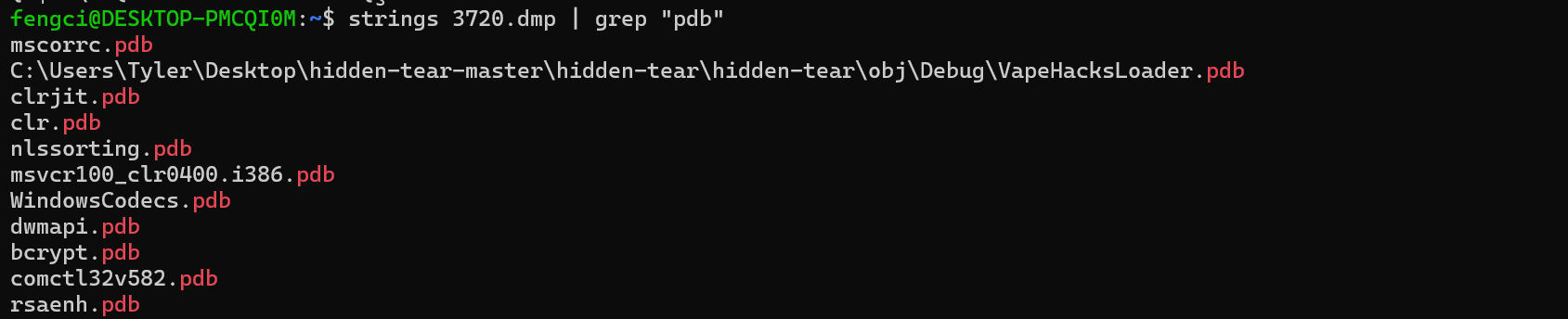
strings -e l 3720.dmp | grep "WIN-LO6FAF3DTFE-" -C 2
[OtterCTF 2018]Closure
题目描述
Now that you extracted the password from the memory, could you decrypt rick's files?
之前看到有txt文件这时候用上了
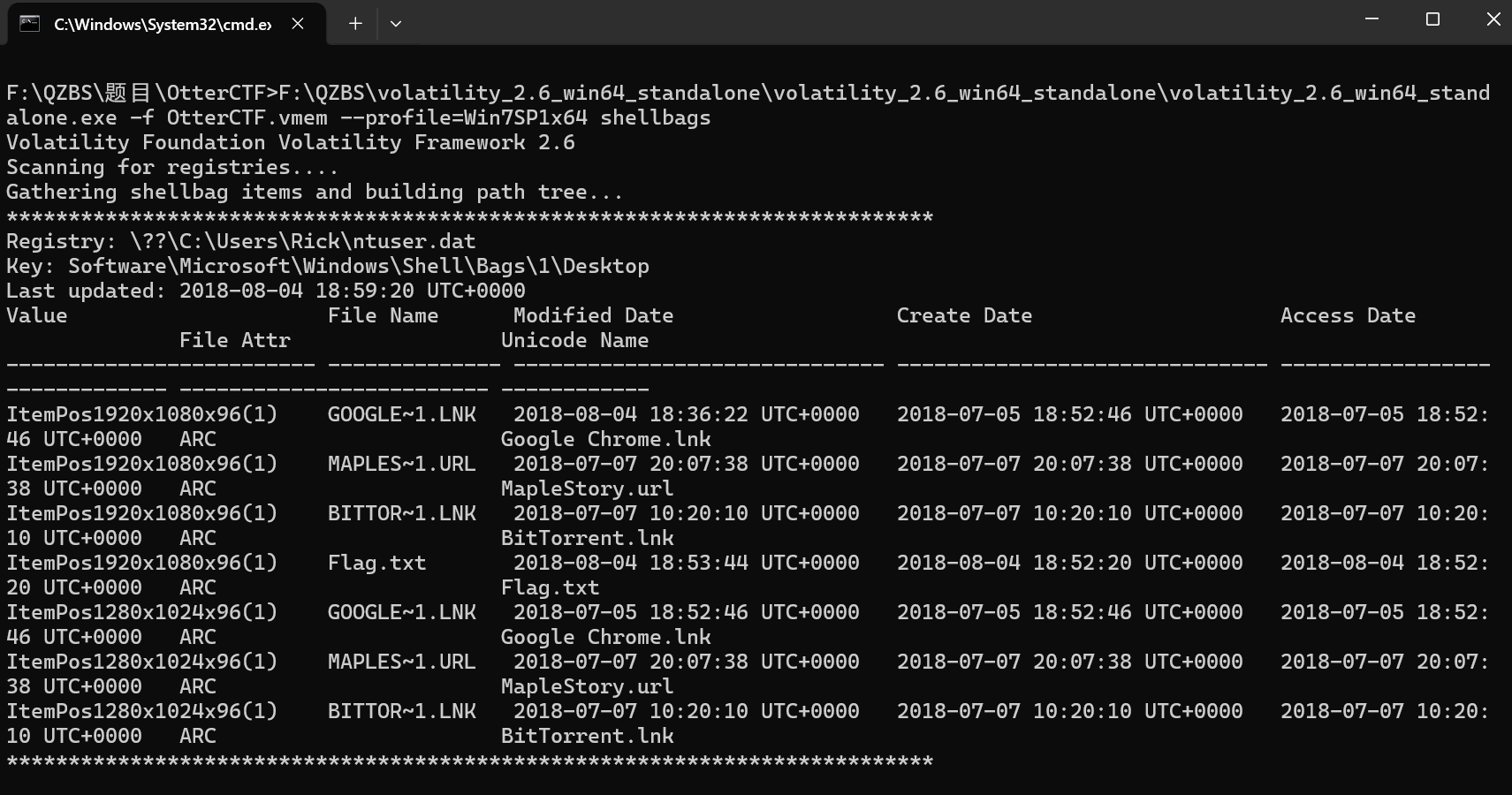
F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 shellbags
F:\QZBS\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone\volatility_2.6_win64_standalone.exe -f OtterCTF.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007e410890 -D .\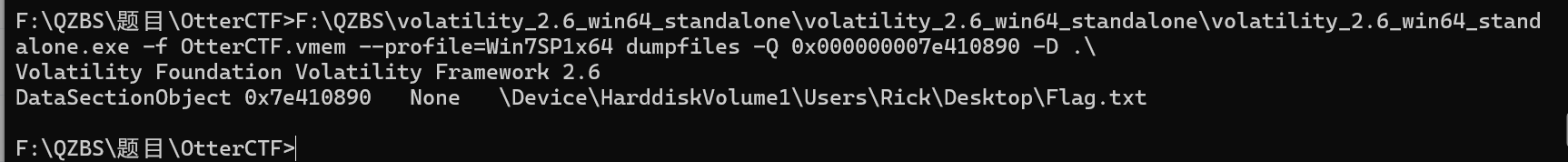
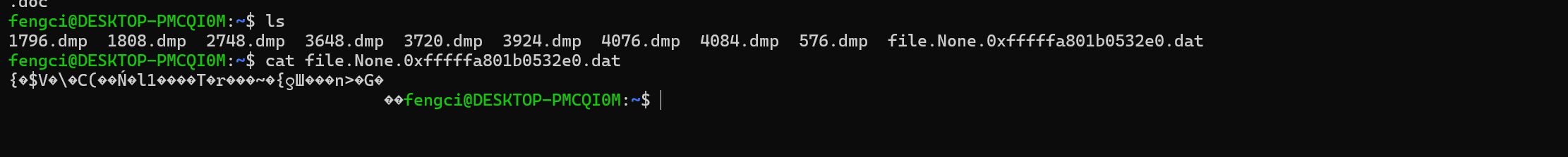
直接查看不了
import hashlib
from Crypto.Protocol.KDF import PBKDF2
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
def decrypt_flag():
# 1. 题目给出的原始信息
password = "aDOBofVYUNVnmp7"
salt = bytes([1, 2, 3, 4, 5, 6, 7, 8])
# 2. 对应 C# 中的 SHA256.Create().ComputeHash(Encoding.UTF8.GetBytes(password))
password_bytes = password.encode('utf-8')
sha256_hash = hashlib.sha256(password_bytes).digest()
# 3. 对应 C# 中的 Rfc2898DeriveBytes(passwordBytes, salt, 1000)
# KeySize 是 256 bits (32 bytes), BlockSize 是 128 bits (16 bytes)
# 总共派生 32 + 16 = 48 字节的数据
kdf_data = PBKDF2(sha256_hash, salt, dkLen=48, count=1000)
key = kdf_data[:32]
iv = kdf_data[32:48]
# 4. 读取加密的文件 (请确保文件名和路径正确)
try:
# 将你提取出的那个 .dat 文件改名为 Flag.txt.WINDOWS
with open('Flag.txt.WINDOWS', 'rb') as f:
encrypted_data = f.read()
# 5. AES CBC 解密
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_padding = cipher.decrypt(encrypted_data)
# 移除 PKCS7 填充
final_data = unpad(decrypted_padding, AES.block_size)
print("解密成功!内容如下:")
print(final_data.decode('utf-8'))
except Exception as e:
print(f"解密失败: {e}")
print("提示:请检查当前目录下是否存在 Flag.txt.WINDOWS 文件,以及文件内容是否完整。")
if __name__ == "__main__":
decrypt_flag()
成功获取flag
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容








所有评论(0)