校园网络小综合
<jiaoxuequyu>displaycurrent-configuration#sysname jiaoxuequyu#vlan batch 100#cluster enablentdp enablendp enable#drop illegal-mac alarm#diffserv domain default#drop-profile default#vlan 100description
1 拓扑
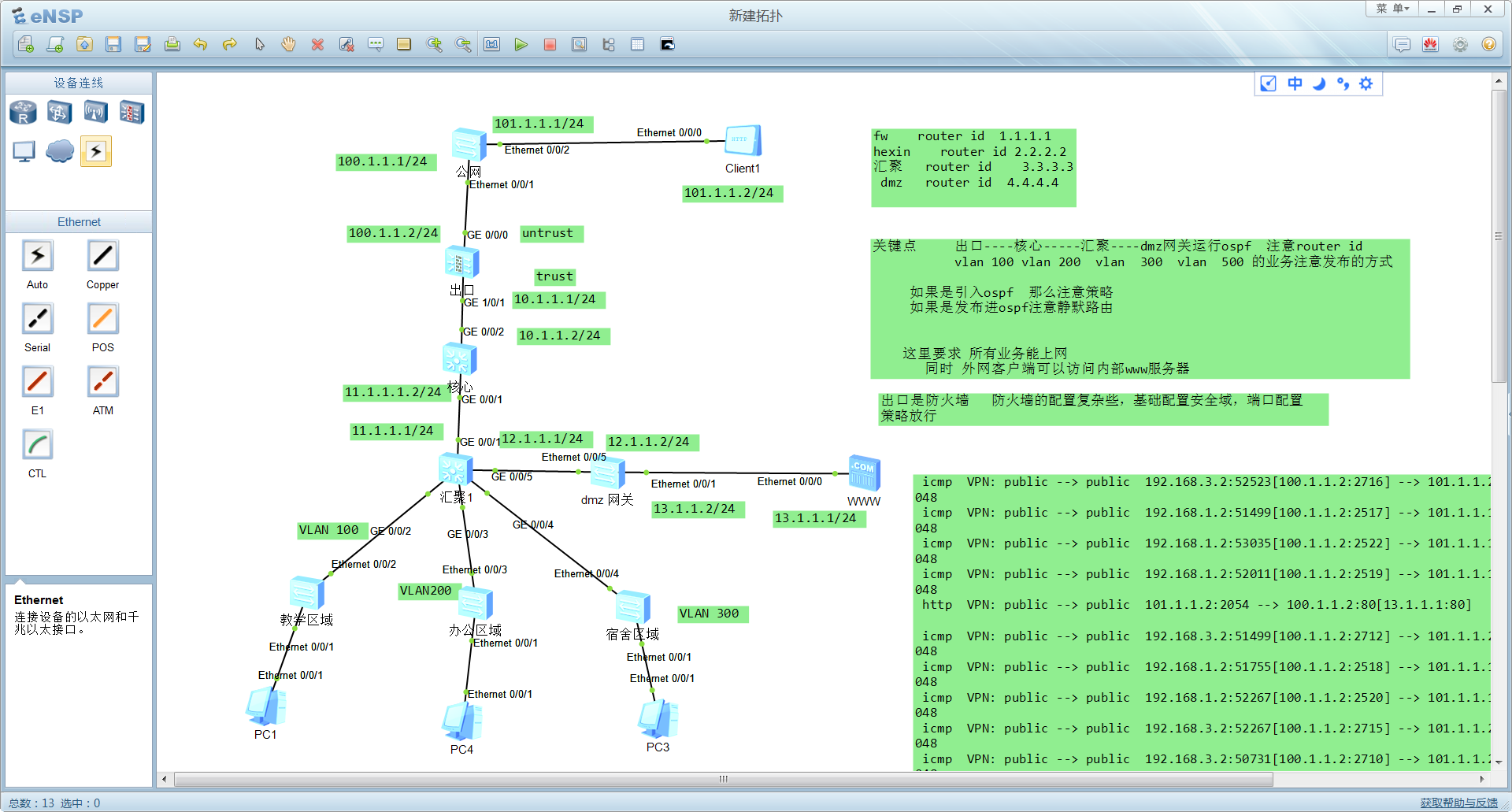
2 配置
2.1 接入交换机配置
<jiaoxuequyu>display current-configuration
#
sysname jiaoxuequyu
#
vlan batch 100
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
vlan 100
description jiaoxueyuju
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type access
port default vlan 100
#
interface Ethernet0/0/2
port link-type access
port default vlan 100
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface Ethernet0/0/8
#
interface Ethernet0/0/9
#
interface Ethernet0/0/10
#
interface Ethernet0/0/11
#
interface Ethernet0/0/12
#
interface Ethernet0/0/13
#
interface Ethernet0/0/14
#
interface Ethernet0/0/15
#
interface Ethernet0/0/16
#
interface Ethernet0/0/17
#
interface Ethernet0/0/18
#
interface Ethernet0/0/19
#
interface Ethernet0/0/20
#
interface Ethernet0/0/21
#
interface Ethernet0/0/22
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return
--------------------------------------------------------------------
<bangong>display current-configuration
#
sysname bangong
#
vlan batch 200
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type access
port default vlan 200
#
interface Ethernet0/0/2
#
interface Ethernet0/0/3
port link-type access
port default vlan 200
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface Ethernet0/0/8
#
interface Ethernet0/0/9
#
interface Ethernet0/0/10
#
interface Ethernet0/0/11
#
interface Ethernet0/0/12
#
interface Ethernet0/0/13
#
interface Ethernet0/0/14
#
interface Ethernet0/0/15
#
interface Ethernet0/0/16
#
interface Ethernet0/0/17
#
interface Ethernet0/0/18
#
interface Ethernet0/0/19
#
interface Ethernet0/0/20
#
interface Ethernet0/0/21
#
interface Ethernet0/0/22
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return
---------------------------------------------
<sushe>display current-configuration
#
sysname sushe
#
vlan batch 300
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type access
port default vlan 300
#
interface Ethernet0/0/2
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
port link-type access
port default vlan 300
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface Ethernet0/0/8
#
interface Ethernet0/0/9
#
interface Ethernet0/0/10
#
interface Ethernet0/0/11
#
interface Ethernet0/0/12
#
interface Ethernet0/0/13
#
interface Ethernet0/0/14
#
interface Ethernet0/0/15
#
interface Ethernet0/0/16
#
interface Ethernet0/0/17
#
interface Ethernet0/0/18
#
interface Ethernet0/0/19
#
interface Ethernet0/0/20
#
interface Ethernet0/0/21
#
interface Ethernet0/0/22
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
2.2 核心区域的配置
<dmz>display current-configuration
#
sysname dmz
#
vlan batch 10 20
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
acl number 2000
rule 1 permit source 13.1.1.0 0.0.0.255
#
drop-profile default
#
vlan 10
description to-wangguang
vlan 20
description to-server
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
ip address 13.1.1.2 255.255.255.0
#
interface Vlanif10
description to-huiju
ip address 12.1.1.2 255.255.255.0
#
interface MEth0/0/1
#
interface Ethernet0/0/1
#
interface Ethernet0/0/2
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
port link-type access
port default vlan 10
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface Ethernet0/0/8
#
interface Ethernet0/0/9
#
interface Ethernet0/0/10
#
interface Ethernet0/0/11
#
interface Ethernet0/0/12
#
interface Ethernet0/0/13
#
interface Ethernet0/0/14
#
interface Ethernet0/0/15
#
interface Ethernet0/0/16
#
interface Ethernet0/0/17
#
interface Ethernet0/0/18
#
interface Ethernet0/0/19
#
interface Ethernet0/0/20
#
interface Ethernet0/0/21
#
interface Ethernet0/0/22
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ospf 1 router-id 4.4.4.4
import-route direct route-policy 1
area 0.0.0.0
network 12.1.1.0 0.0.0.255
#
route-policy 1 permit node 10
if-match acl 2000
apply cost 1000
#
user-interface con 0
user-interface vty 0 4
#
return
---------------------------------------
<huiju>display current-configuration
#
sysname huiju
#
vlan batch 10 20 100 200 300 500
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
acl number 2000
rule 1 permit source 192.168.4.0 0.0.0.255
rule 2 permit source 192.168.1.0 0.0.0.255
rule 3 permit source 192.168.3.0 0.0.0.255
#
drop-profile default
#
vlan 10
description to-dmz-wangguan
vlan 100
description jiaoxuequyu
vlan 200
description bangongquyu
vlan 300
description sushequyu
vlan 500
description dmzquyu
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif10
description to-dmz-wangguan
ip address 12.1.1.1 255.255.255.0
#
interface Vlanif20
ip address 11.1.1.1 255.255.255.0
#
interface Vlanif100
description jiaoxuequyu
ip address 192.168.4.1 255.255.255.0
#
interface Vlanif200
description bangongquyu
ip address 192.168.1.1 255.255.255.0
#
interface Vlanif300
description sushequyu
ip address 192.168.3.1 255.255.255.0
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 100
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 200
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 300
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
ospf 1 router-id 3.3.3.3
import-route direct route-policy 1
area 0.0.0.0
network 11.1.1.0 0.0.0.255
network 12.1.1.0 0.0.0.255
#
route-policy 1 permit node 10
if-match acl 2000
apply cost 10000
#
user-interface con 0
user-interface vty 0 4
#
return
----------------------------------------------------------------
<hexin>display current-configuration
#
sysname hexin
#
vlan batch 10 20
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif10
ip address 10.1.1.2 255.255.255.0
#
interface Vlanif20
ip address 11.1.1.2 255.255.255.0
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 10.1.1.0 0.0.0.255
network 11.1.1.0 0.0.0.255
#
user-interface con 0
user-interface vty 0 4
#
return
--------------------------------------------------
#
interface GigabitEthernet0/0/0
undo shutdown
ip address 100.1.1.2 255.255.255.0
alias GE0/METH
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.1.1.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet0/0/0
#
firewall zone dmz
set priority 50
#
ospf 1 router-id 1.1.1.1
default-route-advertise always
area 0.0.0.0
network 10.1.1.0 0.0.0.255
#
ip route-static 0.0.0.0 0.0.0.0 100.1.1.1
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
nat server 0 global 100.1.1.2 inside 13.1.1.1
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name nat
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
action permit
rule name zhilian
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 100.1.1.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 100.1.1.0 mask 255.255.255.0
action permit
rule name ospf
source-zone local
source-zone trust
destination-zone local
destination-zone trust
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name nat
source-zone trust
destination-zone untrust
source-address 192.168.1.0 mask 255.255.255.0
source-address 192.168.2.0 mask 255.255.255.0
source-address 192.168.3.0 mask 255.255.255.0
source-address 192.168.4.0 mask 255.255.255.0
action source-nat easy-ip
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return
2.2 公网配置
<isp>display current-configuration
#
sysname isp
#
vlan batch 2
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
ip address 100.1.1.1 255.255.255.0
#
interface Vlanif2
ip address 101.1.1.1 255.255.255.0
#
interface MEth0/0/1
#
interface Ethernet0/0/1
#
interface Ethernet0/0/2
port link-type access
port default vlan 2
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface Ethernet0/0/8
#
interface Ethernet0/0/9
#
interface Ethernet0/0/10
#
interface Ethernet0/0/11
#
interface Ethernet0/0/12
#
interface Ethernet0/0/13
#
interface Ethernet0/0/14
#
interface Ethernet0/0/15
#
interface Ethernet0/0/16
#
interface Ethernet0/0/17
#
interface Ethernet0/0/18
#
interface Ethernet0/0/19
#
interface Ethernet0/0/20
#
interface Ethernet0/0/21
#
interface Ethernet0/0/22
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return
3 测试
汇聚网关能通
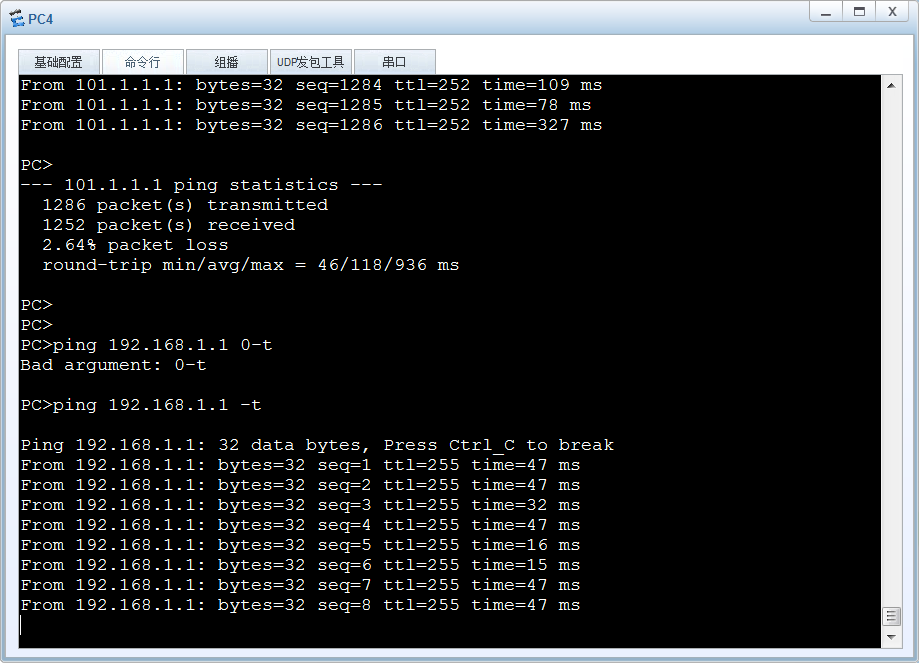
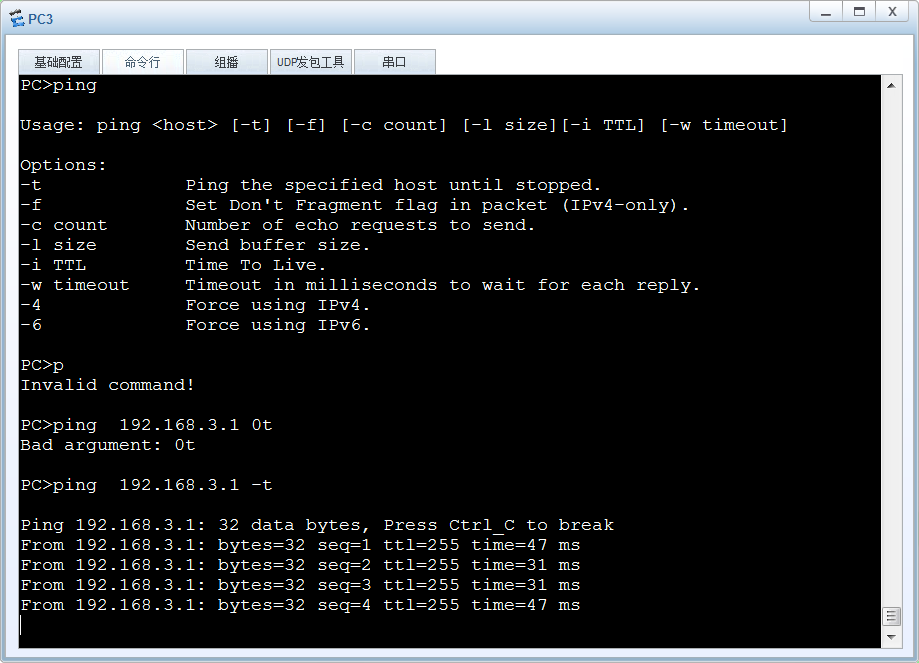
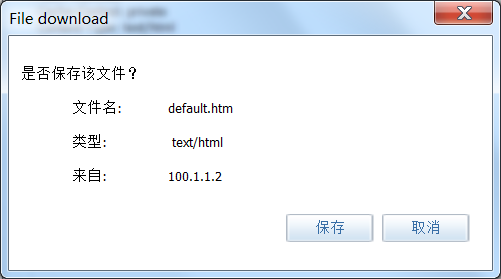
<chukou-fw>display firewall session table
2025-12-21 17:35:34.350
Current Total Sessions : 44
http VPN: public --> public 101.1.1.2:2057 --> 100.1.1.2:80[13.1.1.1:80]
icmp VPN: public --> public 192.168.1.2:58927[100.1.1.2:3340] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.3.2:61743[100.1.1.2:4228] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:60207[100.1.1.2:4215] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:61231[100.1.1.2:4224] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:56879[100.1.1.2:4201] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:59183[100.1.1.2:3341] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.4.2:58415[100.1.1.2:4206] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:61487[100.1.1.2:4226] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:61231[100.1.1.2:4223] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:60463[100.1.1.2:4218] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:58159[100.1.1.2:3337] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.1.2:60975[100.1.1.2:3347] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.4.2:60719[100.1.1.2:4219] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:58671[100.1.1.2:3339] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.1.2:60719[100.1.1.2:3346] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.4.2:57903[100.1.1.2:4204] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:59951[100.1.1.2:3343] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.1.2:60463[100.1.1.2:3345] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.3.2:59951[100.1.1.2:4214] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:59439[100.1.1.2:3342] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.4.2:61743[100.1.1.2:4227] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:60975[100.1.1.2:4222] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:60207[100.1.1.2:4216] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:58927[100.1.1.2:4208] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:58159[100.1.1.2:4205] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:60463[100.1.1.2:4217] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:61487[100.1.1.2:3349] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.3.2:59439[100.1.1.2:4212] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:59695[100.1.1.2:4213] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:57391[100.1.1.2:4202] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:57647[100.1.1.2:4203] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:61743[100.1.1.2:3350] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.4.2:59183[100.1.1.2:4209] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:60719[100.1.1.2:4220] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.4.2:61487[100.1.1.2:4225] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:60207[100.1.1.2:3344] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.1.2:57903[100.1.1.2:3336] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.4.2:59439[100.1.1.2:4211] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:59183[100.1.1.2:4210] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.1.2:61231[100.1.1.2:3348] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.1.2:58415[100.1.1.2:3338] --> 101.1.1.1:2
048
icmp VPN: public --> public 192.168.4.2:58671[100.1.1.2:4207] --> 101.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:60975[100.1.1.2:4221] --> 101.1.1.2:2
048
注意测试这些数据流
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容






所有评论(0)