交叉编译sudo-1.9.16p2,并在幸狐rv1106板子上使用,解决sudo即使输入正确的密码也提示Sorry, try again.的问题
这是因为./configure找不到crypt.h,config.h里面没有定义HAVE_CRYPT宏,#ifdef HAVE_CRYPT不成立,所以plugins/sudoers/auth/passwd.c里面的sudo_passwd_verify函数是直接用strcmp比较,看输入的密码是否和/etc/passwd里面写的加密后的密码相同。wget https://电脑IP/oct1158/s
交叉编译器下载地址:https://developer.arm.com/downloads/-/arm-gnu-toolchain-downloads/14-2-rel1
x86_64 Linux hosted cross toolchains
AArch32 GNU/Linux target with hard float (arm-none-linux-gnueabihf)
笔者用的虚拟机系统为fedora42。
下载交叉编译器后解压出来,然后放到PATH环境变量里面。
export PATH=$PATH:/home/oct1158/Downloads/arm-gnu-toolchain-14.2.rel1-x86_64-arm-none-linux-gnueabihf/bin
由于这个交叉编译器不带crypt.h头文件和crypt函数,如果我们直接编译sudo的话能编译成功,但是在板子上运行sudo命令,即使输入正确的密码也会提示Sorry, try again.。只有输入/etc/passwd里面写的加密后的密码,密码才正确。
这是因为./configure找不到crypt.h,config.h里面没有定义HAVE_CRYPT宏,#ifdef HAVE_CRYPT不成立,所以plugins/sudoers/auth/passwd.c里面的sudo_passwd_verify函数是直接用strcmp比较,看输入的密码是否和/etc/passwd里面写的加密后的密码相同。
因此,我们必须想办法使config.h里面的HAVE_CRYPT为1。
libxcrypt库里面有crypt.h头文件和crypt函数,我们只要交叉编译libxcrypt库,然后在交叉编译sudo的时候在CFLAGS和LDFLAGS里面指定libxcrypt库的路径,就可以使HAVE_CRYPT=1了。
【交叉编译libxcrypt-4.4.38】
wget https://github.com/besser82/libxcrypt/releases/download/v4.4.38/libxcrypt-4.4.38.tar.xz
tar xf libxcrypt-4.4.38.tar.xz
cd libxcrypt-4.4.38
./configure --host=arm-none-linux-gnueabihf
make
make install DESTDIR=$(pwd)/_install
cd _install
sudo chown -R root:root usr
tar czf libxcrypt-4.4.38-binary.tar.gz usr
mv libxcrypt-4.4.38-binary.tar.gz /var/www/html/oct1158
cd ../..【交叉编译sudo-1.9.16p2】
wget https://www.sudo.ws/dist/sudo-1.9.16p2.tar.gz
tar xf sudo-1.9.16p2.tar.gz
cd sudo-1.9.16p2
./configure --host=arm-none-linux-gnueabihf CFLAGS=-I$(pwd)/../libxcrypt-4.4.38/_install/usr/local/include LDFLAGS="-L$(pwd)/../libxcrypt-4.4.38/_install/usr/local/lib -lcrypt"
执行grep HAVE_CRYPT config.h确认一下HAVE_CRYPT的值是否为1,这个很重要!
make
sudo su
export PATH=$PATH:/home/oct1158/Downloads/arm-gnu-toolchain-14.2.rel1-x86_64-arm-none-linux-gnueabihf/bin
make install DESTDIR=$(pwd)/_install
exit
cd _install
sudo tar czf sudo-1.9.16p2-binary.tar.gz *
sudo mv sudo-1.9.16p2-binary.tar.gz /var/www/html/oct1158
cd ../..【在板子上安装和配置sudo】
提示:如果在安装apache2.4.63时已经在板子上本地编译安装了libxcrypt-4.4.38软件包,那就不用解压libxcrypt-4.4.38-binary.tar.gz。
cd /mnt/sdfat
wget https://电脑IP/oct1158/libxcrypt-4.4.38-binary.tar.gz --no-check-certificate
tar xf libxcrypt-4.4.38-binary.tar.gz -C /
wget https://电脑IP/oct1158/sudo-1.9.16p2-binary.tar.gz --no-check-certificate
tar xf sudo-1.9.16p2-binary.tar.gz -C /
[oct1158@luckfox-rv1106 ~]$ passwd
passwd: must be suid to work properly
[oct1158@luckfox-rv1106 ~]$ su
su: must be suid to work properly解决passwd和su命令无法使用的问题:
[root@luckfox-rv1106 ~/software/sudo-1.9.16p2]# ls -l /bin/busybox
-rwxr-xr-x 1 root root 1385804 Jun 18 08:37 /bin/busybox
[root@luckfox-rv1106 ~/software/sudo-1.9.16p2]# chmod 4755 /bin/busybox
[root@luckfox-rv1106 ~/software/sudo-1.9.16p2]# ls -l /bin/busybox
-rwsr-xr-x 1 root root 1385804 Jun 18 08:37 /bin/busybox
[root@luckfox-rv1106 ~/software/sudo-1.9.16p2]# 新建/etc/sudoers.d/oct1158文件(其中oct1158是用户名):
echo "oct1158 ALL=(ALL:ALL) ALL" > /etc/sudoers.d/oct1158
现在就可以正常在oct1158用户下使用sudo了,密码是oct1158用户的密码,不是root用户的密码。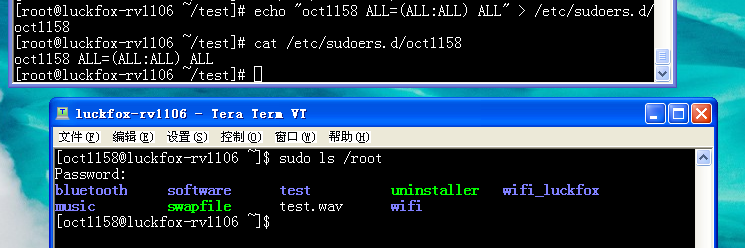
也可以选择在板子上用gcc14.2本地编译sudo-1.9.16p2。
在板子上本地编译sudo-1.9.16p2前也必须编译安装libxcrypt-4.4.38库(perl-5.40.2是libxcrypt-4.4.38的依赖项),否则sudo命令只能输入/etc/passwd里面的加密后的密码,输入linux用户本身的密码会提示密码不正确。
一定要确保系统里面设置了C_INCLUDE_PATH环境变量,不然编译会出错:export C_INCLUDE_PATH=/usr/include
工作目录:
mkdir -p /root/software/sudo
cd /root/software/sudo
【在板子上本地编译安装perl-5.40.2】
见在幸狐RV1106板子上用gcc14.2本地编译安装apache2.4.63,开启http2和tls1.3,并且https支持XP系统的IE6-8浏览器
【在板子上本地编译安装libxcrypt-4.4.38】
见在幸狐RV1106板子上用gcc14.2本地编译安装apache2.4.63,开启http2和tls1.3,并且https支持XP系统的IE6-8浏览器
【在板子上本地编译安装sudo-1.9.16p2】
wget https://www.sudo.ws/dist/sudo-1.9.16p2.tar.gz --no-check-certificate
tar xf sudo-1.9.16p2.tar.gz
cd sudo-1.9.16p2
./configure
执行grep HAVE_CRYPT config.h确认一下HAVE_CRYPT的值是否为1,这个很重要!
make
make install
ldconfig
cd ..
【配置sudo】
解决passwd和su命令无法使用的问题:chmod 4755 /bin/busybox
新建/etc/sudoers.d/oct1158文件(其中oct1158是用户名):echo "oct1158 ALL=(ALL:ALL) ALL" > /etc/sudoers.d/oct1158
串口里面只能登录root账户,可以在Windows系统下开一个telnet窗口连接板子,以非root用户登录:telnet 板子IP
现在就可以正常在oct1158用户下使用sudo了,密码是oct1158用户的密码,不是root用户的密码。
可以用sudo -V或sudo sudo -V命令查看sudo的版本信息。
luckfox-rv1106 login: oct1158
Password:
Processing /etc/profile... Done
[oct1158@luckfox-rv1106 ~]$ sudo -V
Sudo version 1.9.16p2
Sudoers policy plugin version 1.9.16p2
Sudoers file grammar version 50
Sudoers I/O plugin version 1.9.16p2
Sudoers audit plugin version 1.9.16p2
[oct1158@luckfox-rv1106 ~]$
[oct1158@luckfox-rv1106 ~]$
[oct1158@luckfox-rv1106 ~]$ sudo sudo -V
Password:
Sudo version 1.9.16p2
Configure options:
Sudoers policy plugin version 1.9.16p2
Sudoers file grammar version 50
Sudoers path: /etc/sudoers
Authentication methods: 'passwd'
Syslog facility if syslog is being used for logging: authpriv
Syslog priority to use when user authenticates successfully: notice
Syslog priority to use when user authenticates unsuccessfully: alert
Send mail if the user is not in sudoers
Lecture user the first time they run sudo
Require users to authenticate by default
Root may run sudo
Allow some information gathering to give useful error messages
Visudo will honor the EDITOR environment variable
Set the LOGNAME and USER environment variables
Length at which to wrap log file lines (0 for no wrap): 80
Authentication timestamp timeout: 5.0 minutes
Password prompt timeout: 5.0 minutes
Number of tries to enter a password: 3
Umask to use or 0777 to use user's: 022
Path to mail program: /usr/sbin/sendmail
Flags for mail program: -t
Address to send mail to: root
Subject line for mail messages: *** SECURITY information for %h ***
Incorrect password message: Sorry, try again.
Path to lecture status dir: /var/db/sudo/lectured
Path to authentication timestamp dir: /var/run/sudo/ts
Default password prompt: Password:
Default user to run commands as: root
Value to override user's $PATH with: /usr/local/sbin:/usr/local/bin:/usr/sbin:/u
sr/bin:/sbin:/bin
Path to the editor for use by visudo: /usr/bin/vi
When to require a password for 'list' pseudocommand: any
When to require a password for 'verify' pseudocommand: all
File descriptors >= 3 will be closed before executing a command
Reset the environment to a default set of variables
Environment variables to check for safety:
TZ
TERM
LINGUAS
LC_*
LANGUAGE
LANG
COLORTERM
Environment variables to remove:
*=()*
RUBYOPT
RUBYLIB
PYTHONUSERBASE
PYTHONINSPECT
PYTHONPATH
PYTHONHOME
TMPPREFIX
ZDOTDIR
READNULLCMD
NULLCMD
FPATH
PERL5DB
PERL5OPT
PERL5LIB
PERLLIB
PERLIO_DEBUG
JAVA_TOOL_OPTIONS
SHELLOPTS
BASHOPTS
GLOBIGNORE
PS4
BASH_ENV
ENV
TERMCAP
TERMPATH
TERMINFO_DIRS
TERMINFO
_RLD*
LD_*
PATH_LOCALE
NLSPATH
HOSTALIASES
RES_OPTIONS
LOCALDOMAIN
CDPATH
IFS
Environment variables to preserve:
XDG_CURRENT_DESKTOP
XAUTHORIZATION
XAUTHORITY
PS2
PS1
PATH
LS_COLORS
KRB5CCNAME
HOSTNAME
DISPLAY
COLORS
Locale to use while parsing sudoers: C
Always run commands in a pseudo-tty
Directory in which to store input/output logs: /var/log/sudo-io
File in which to store the input/output log: %{seq}
Add an entry to the utmp/utmpx file when allocating a pty
PAM service name to use: sudo
PAM service name to use for login shells: sudo
Attempt to establish PAM credentials for the target user
Create a new PAM session for the command to run in
Perform PAM account validation management
Do not allow PAM authentication modules to generate output
Enable sudoers netgroup support
Check parent directories for writability when editing files with sudoedit
Allow commands to be run even if sudo cannot write to the audit log
Allow commands to be run even if sudo cannot write to the log file
Log entries larger than this value will be split into multiple syslog messages:
960
File mode to use for the I/O log files: 0600
Execute commands by file descriptor instead of by path: digest_only
Type of authentication timestamp record: tty
Ignore case when matching user names
Ignore case when matching group names
Log when a command is allowed by sudoers
Log when a command is denied by sudoers
Sudo log server timeout in seconds: 30
Enable SO_KEEPALIVE socket option on the socket connected to the logserver
Verify that the log server's certificate is valid
Set the pam remote user to the user running sudo
The format of logs to produce: sudo
Allow an intercepted command to run set setuid or setgid programs
The largest size core dump file that may be created (in bytes): 0,0
Store plaintext passwords in I/O log input
List of regular expressions to use when matching a password prompt
[Pp]assword[: ]*
The mechanism used by the intercept and log_subcmds options: trace
Attempt to verify the command and arguments after execution
Local IP address and netmask pairs:
192.168.4.21/255.255.248.0
Sudoers I/O plugin version 1.9.16p2
Sudoers audit plugin version 1.9.16p2
[oct1158@luckfox-rv1106 ~]$
更多推荐
 已为社区贡献29条内容
已为社区贡献29条内容






所有评论(0)